Varonis Is Ending On-Prem. BigID Gives You a Choice.
Don’t get forced into SaaS. Get freedom instead.
Varonis just announced the end of on-prem support. Customers are being told: migrate to SaaS or walk away. If you’ve spent years investing in on-prem infrastructure, you’re now being pushed into a model that doesn’t fit your business, your compliance windows, or your risk tolerance.
You deserve a partner who gives you options - not ultimatums.
-1.png)
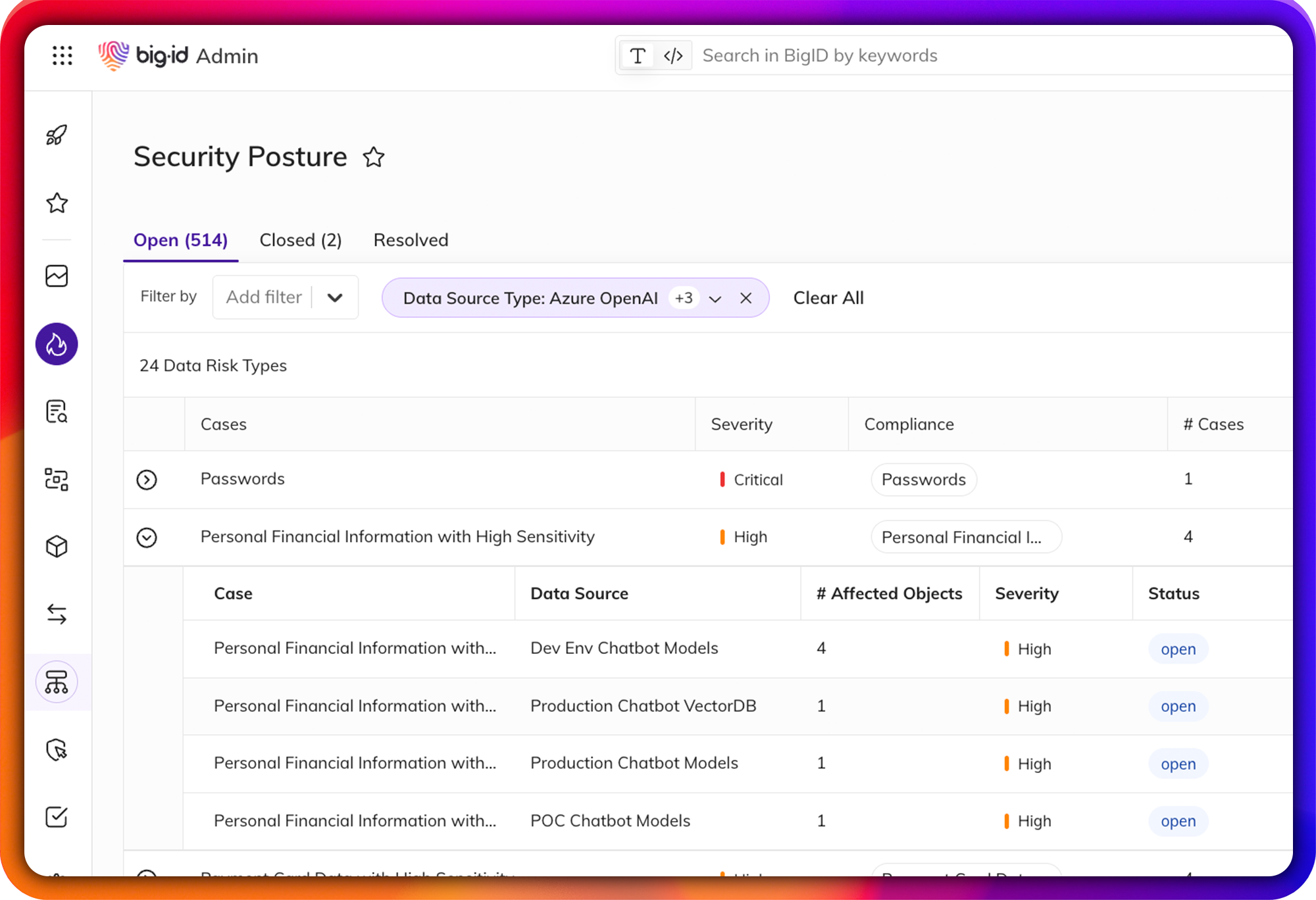
Why Customers Switch to BigID
Category |
Varonis |
The BigID Advantage |
| Discovery & Classification | Agent-based, limited accuracy | Agentless, multi-cloud, identity-aware classification with tuning and accuracy |
| DSPM & Cloud Coverage | File shares, basic cloud | Full DSPM for AWS, Azure, GCP, SaaS, Snowflake, Dev environments and more |
| AI & GenAI Security | Limited | AI SPM, protect data used in AI pipelines, vector DBs, and LLMs |
| Data Mapping & Context | Manual mapping | Automated data mapping with context and flow analysis |
| Policy & Access Controls | Manual, role-based | Intelligent policy automation and identity correlation |
| Remediation & Actions | Alert-only | Automated remediation, tagging, and deletion workflows |
| Compliance Reporting | Basic templates | Built-in frameworks for NIST, GDPR, SEC 540, NYDFS 500, and more |
What You Get with BigID
Deploy where you want
Migrate at your own pace
Gain full visibility
Coverage across cloud, SaaS, and AI environments
Discover, classify, and protect
Automate security and compliance for sensitive data
Replace legacy tools
Leverage a single, modern platform
Get a partner
Partner with a vendor that listens, not dictates
Recognized as the #1 data security, privacy, and AI data management solution



-1.png?width=152&height=193&name=image%20(23)-1.png)

Data-Centric, Risk-Aware Security for the Multi-Cloud & Beyond
- Cloud, hybrid, & on-prem
- Deep & accurate classification
- Automatically take action
- Enterprise-scale security
Shine a Light on Dark Data
Automatically find and inventory your most sensitive, critical, and high-priority data - wherever it lives.
Get unmatched data discovery and classification to find and protect the data that matters most to you: whether it's critical, regulated, personal, secrets, passwords, IP, financial, or more across structured and unstructured data. Get more accurate results every time with ML-driven data classification - across your entire data landscape (from on-prem to cloud to everywhere in between).
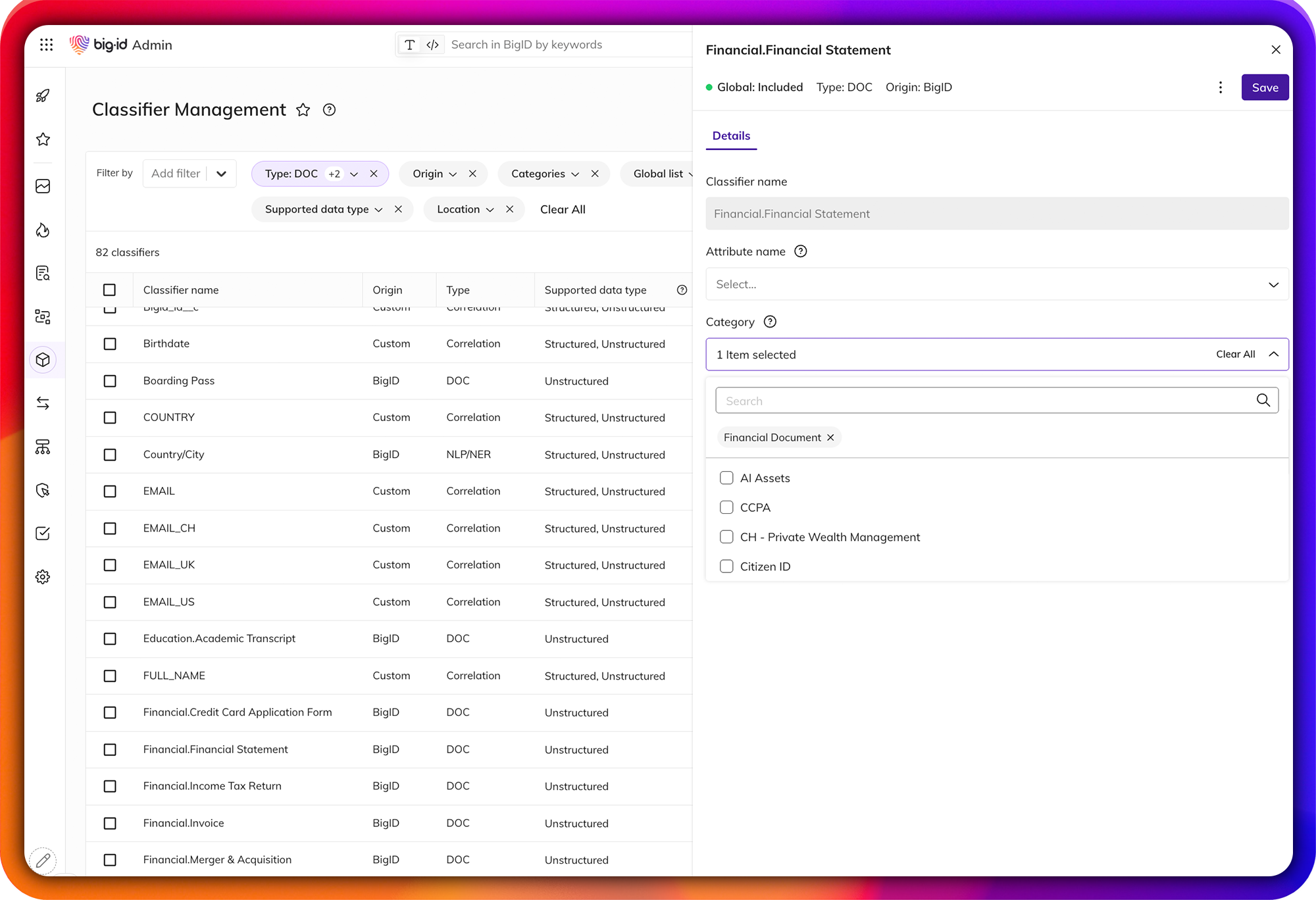
Advanced Sensitivity Classification
Achieve unparalleled accuracy and scalability in data classification.
Go beyond traditional pattern-matching and regular expression (RegEx) with advanced, trainable ML and NLP-based classification. Create custom classifiers that can be tailored specifically to your unique data environment. Test and fine-tune them before deployment to enhance accuracy and mitigate the number of false positives. Label and tag all of your data using a single unified classification ruleset.
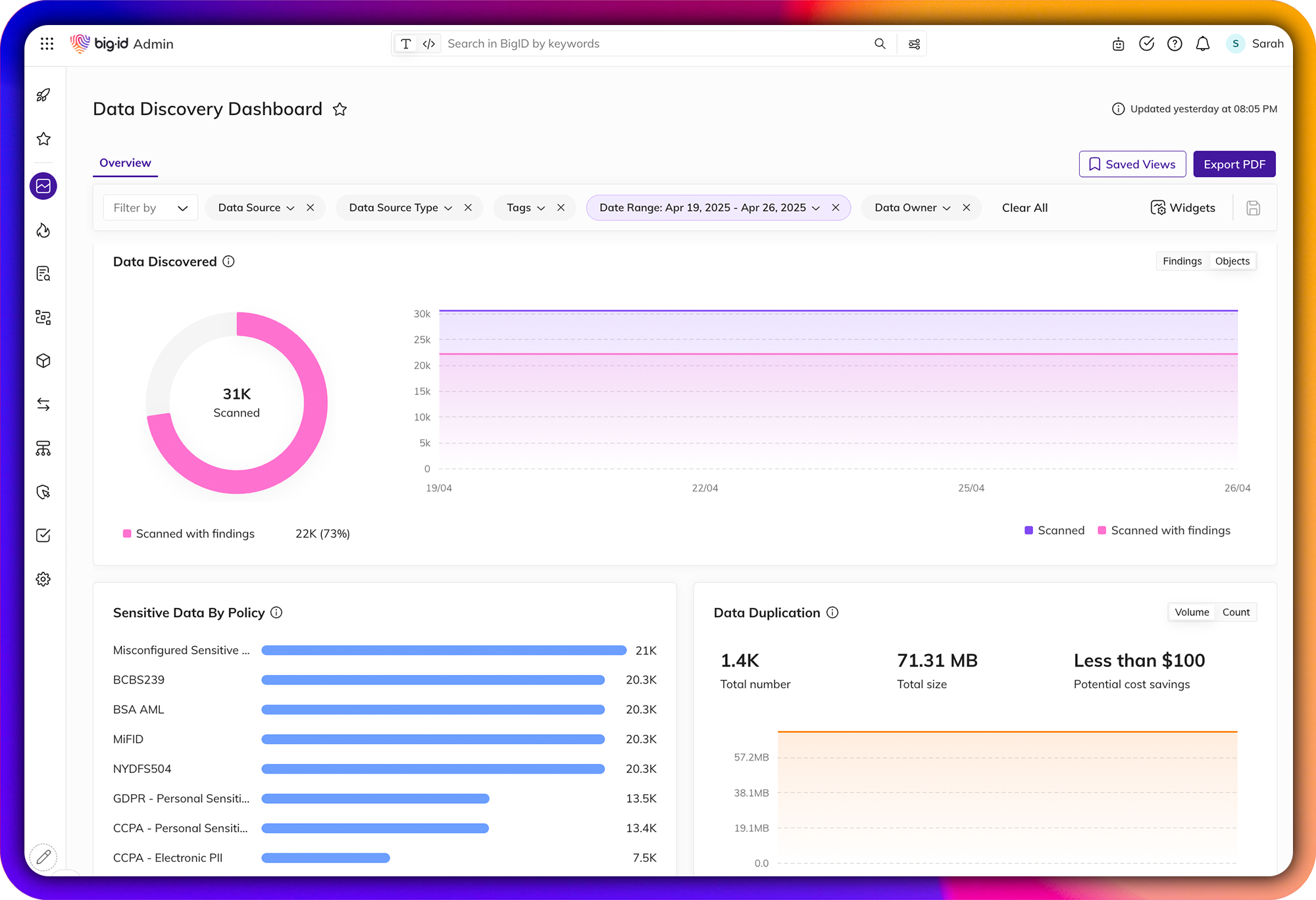
Jumpstart DSPM
Data Security Posture Management for the Multicloud and beyond
Accelerate DSPM: manage risk across the multicloud with a data-centric approach. Automatically map, monitor, and remediate data – with the first platform based on ML-driven in depth data discovery and automation.
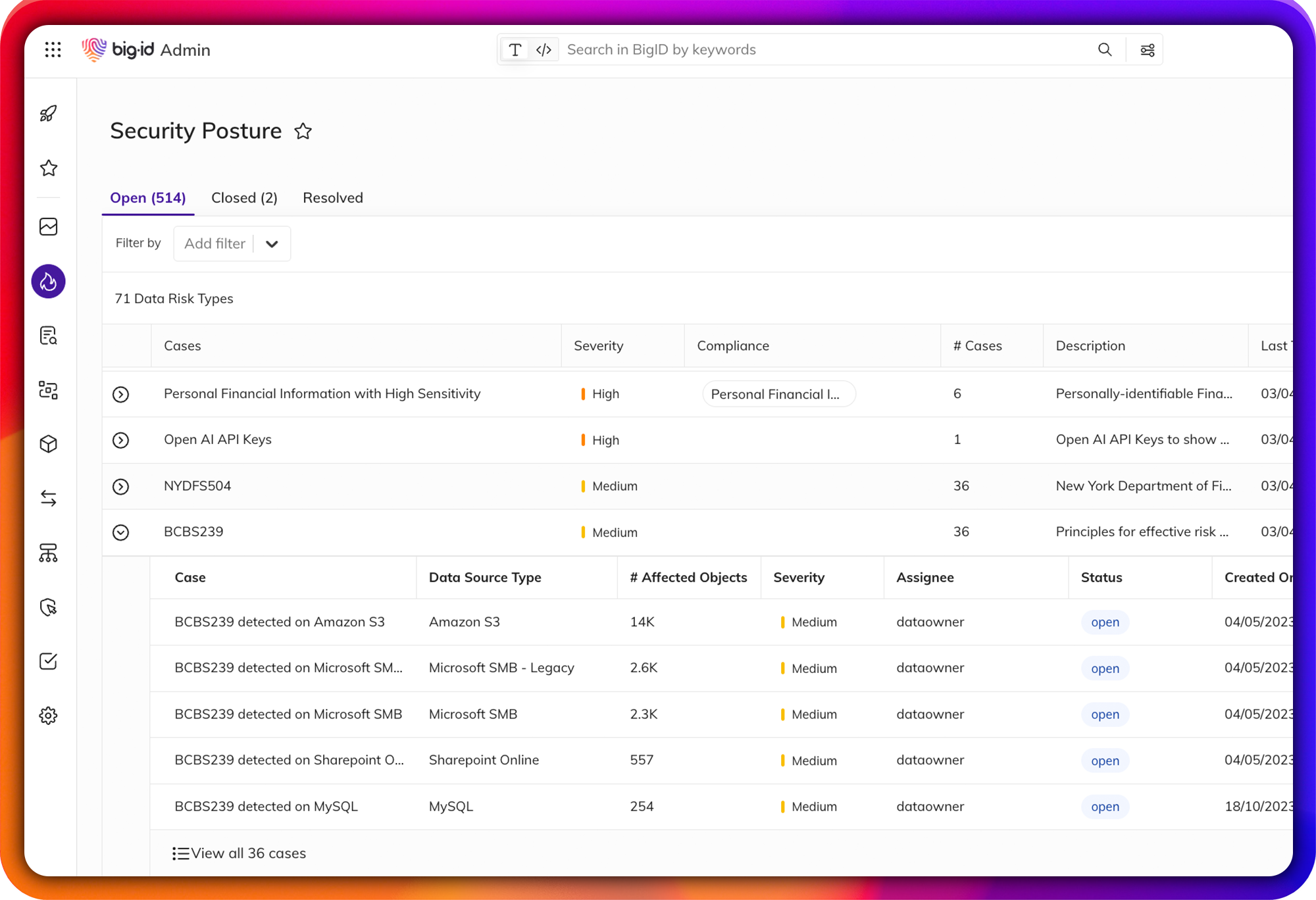
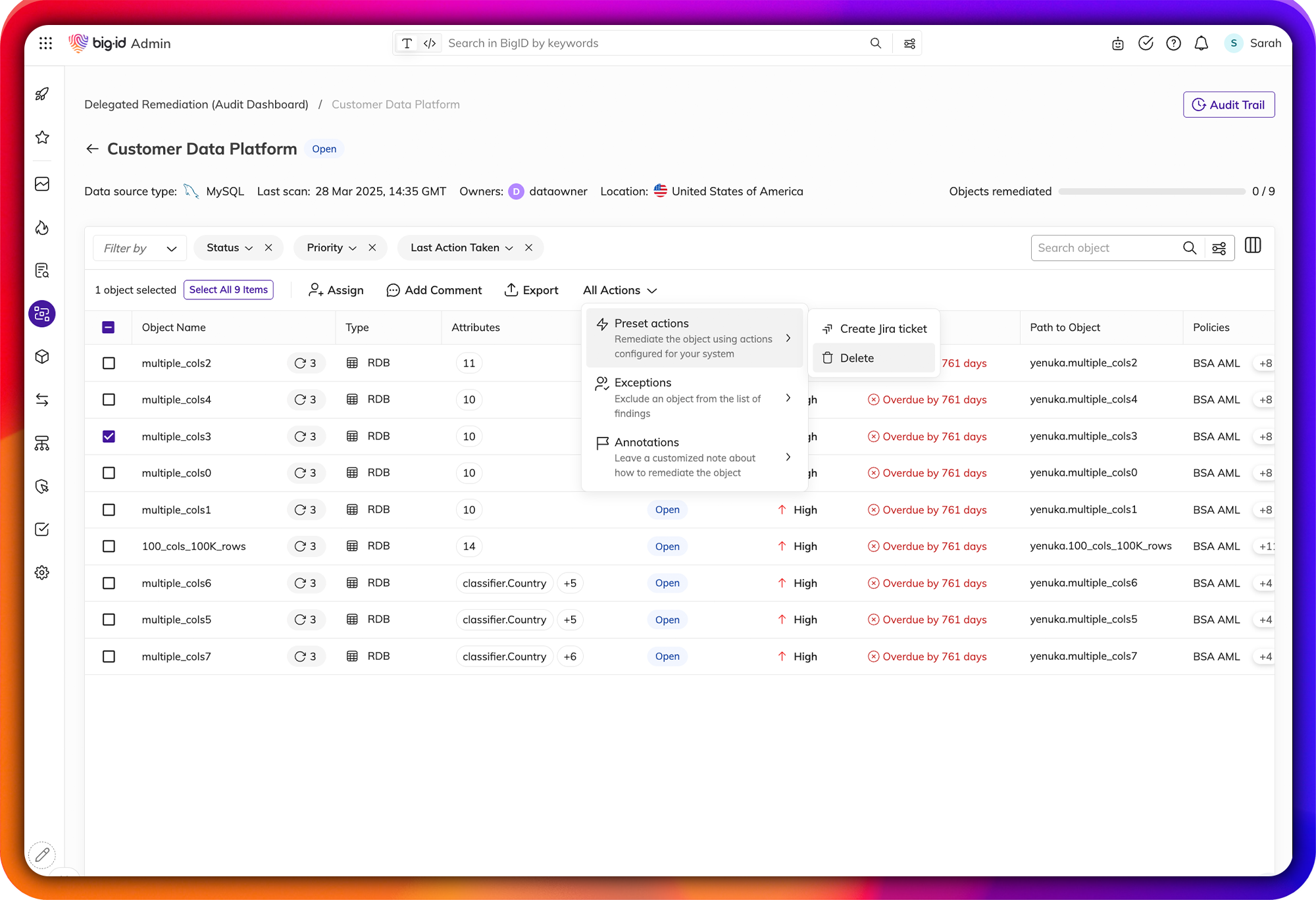
Streamline Data Protection Workflows
Remediate high-risk, sensitive, & critical data, everywhere.
Make it easier than ever for the right people to take the right actions, on the right data. Manage data protection all in one place - a single pane of glass to annotate, delete, quarantine, archive, mask, encrypt, and anonymize sensitive data.
Assign findings and tasks to the right data owners, take action on the right data, and maintain an audit trail of all data protection activity. Enforce and prioritize your remediation actions by policy and report on actions taken on sensitive data.
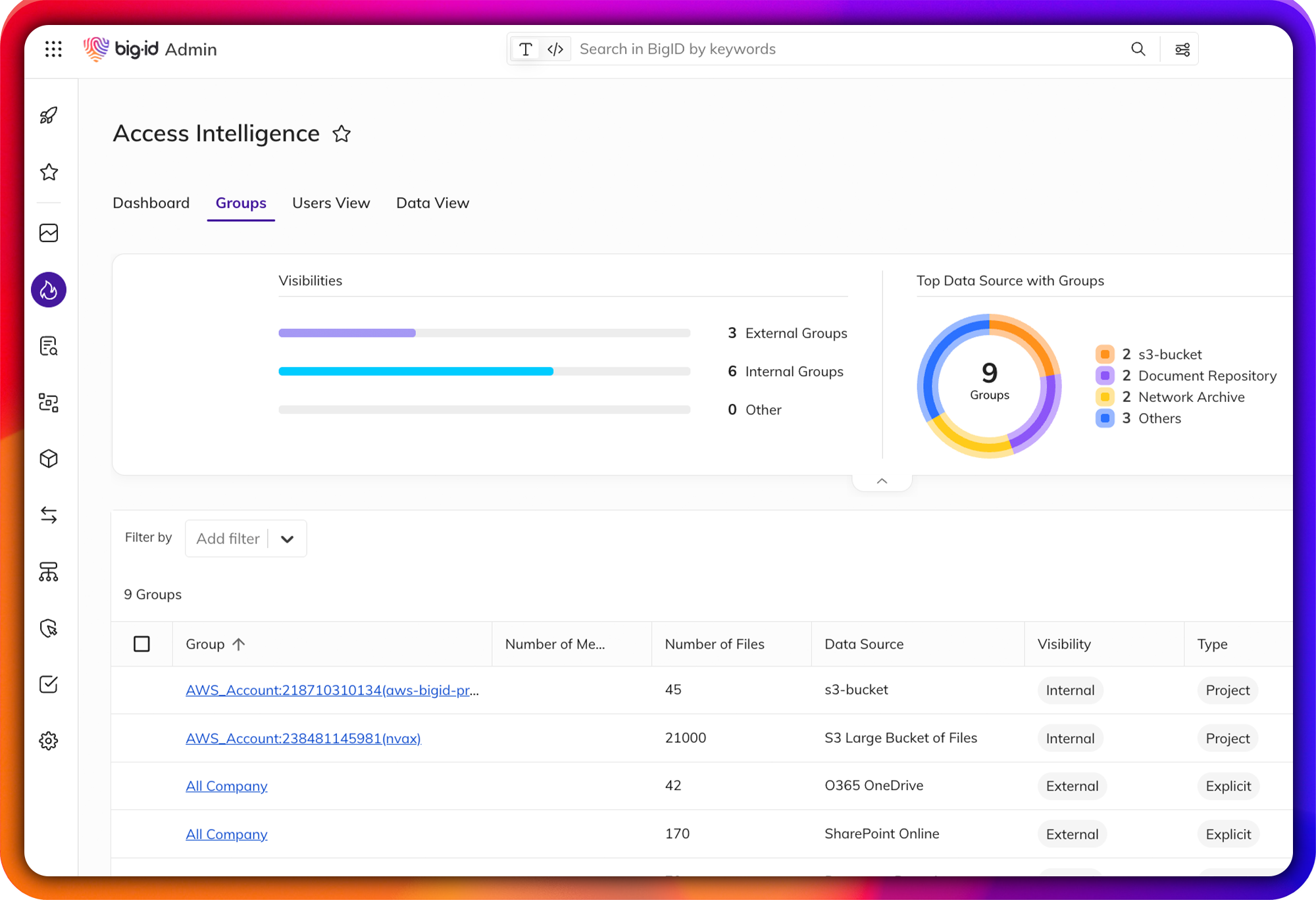
Enable Zero Trust for Data
Identify & remediate high-risk data access issues.
Easily find over-permissioned and over-exposed data across your entire data landscape: mitigate unauthorized use, reduce the risk of data leaks or breaches., and get to a least privileged permissions model for zero trust.
BigID Ranked #1 in Intuit’s Data Classification Challenge
In a highly competitive data classification challenge, Intuit compared vendors’ ability to rapidly and accurately identify sensitive data within massive datasets, ultimately recognizing BigID for its unmatched performance in accuracy, speed, and precision.
See How The University of Maryland Saved $5 Million in Risk Exposure
The University of Maryland faced a familiar yet daunting challenge: sprawling cloud data, scattered sensitive records, and increasing exposure to risk. Their solution? BigID.
Data Security Posture Management (DSPM) for 2025 & Beyond
Stay on the cutting edge of DSPM with the latest innovations and best practices covered in our ultimate guide. We'll dive into the critical capabilities of DSPM and how BigID's pioneering approach enables organizations to keep their data safeguarded, secure, and compliant for 2025 and beyond.
Ready to move on?
Don’t wait until your support runs out. See how easy it is to replace Varonis and upgrade your data security in weeks. Schedule a 1:1 today and we’ll show you how!


