Find and Protect High Risk, Sensitive Data
Fortify your data security strategy to find and protect high-risk, sensitive, and regulated data. Reduce risk and take action to minimize your attack surface, achieve compliance, and improve data protection.
Talk to one of our data protection security specialists 👇 and check out what we put together for you below.
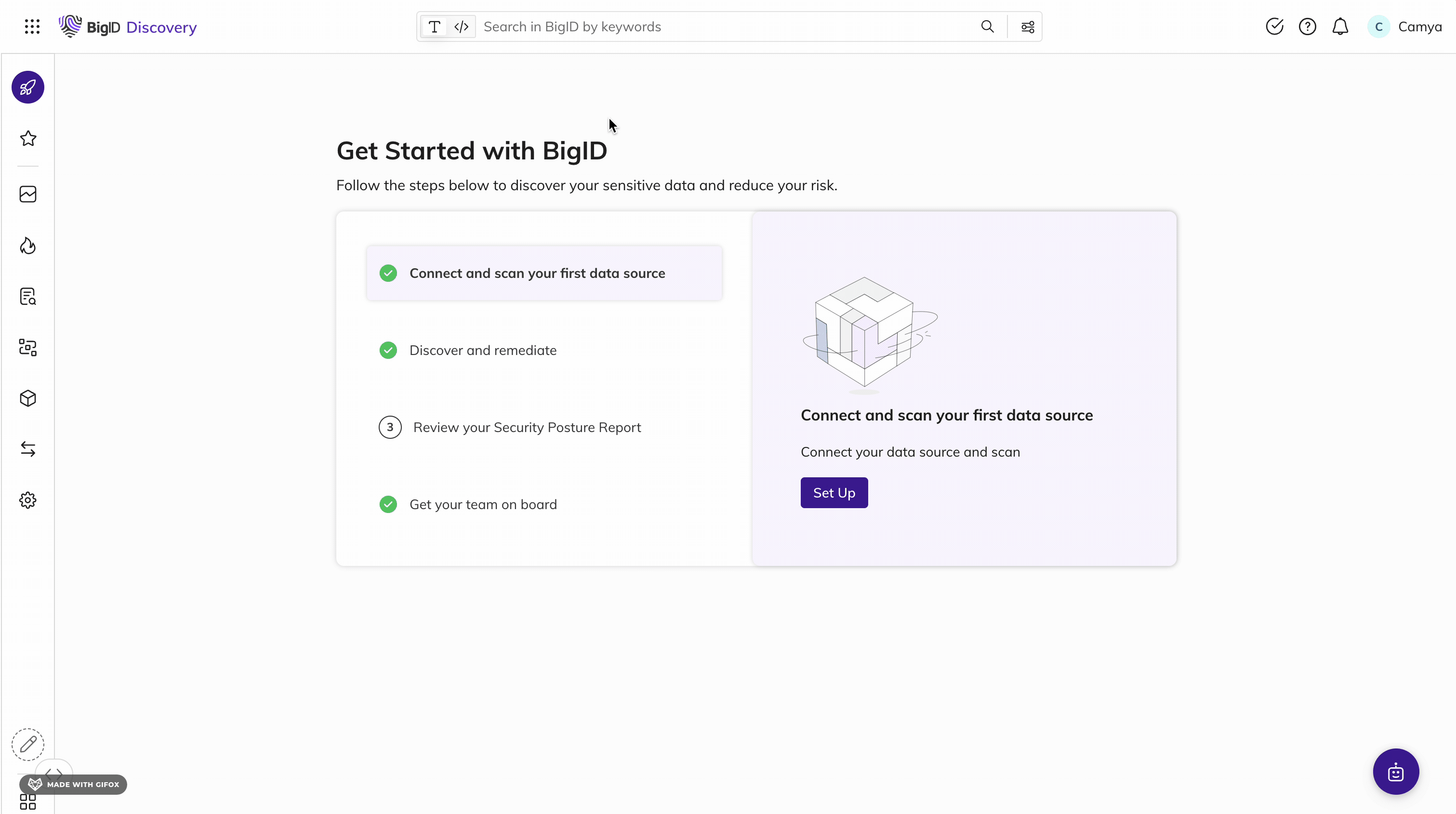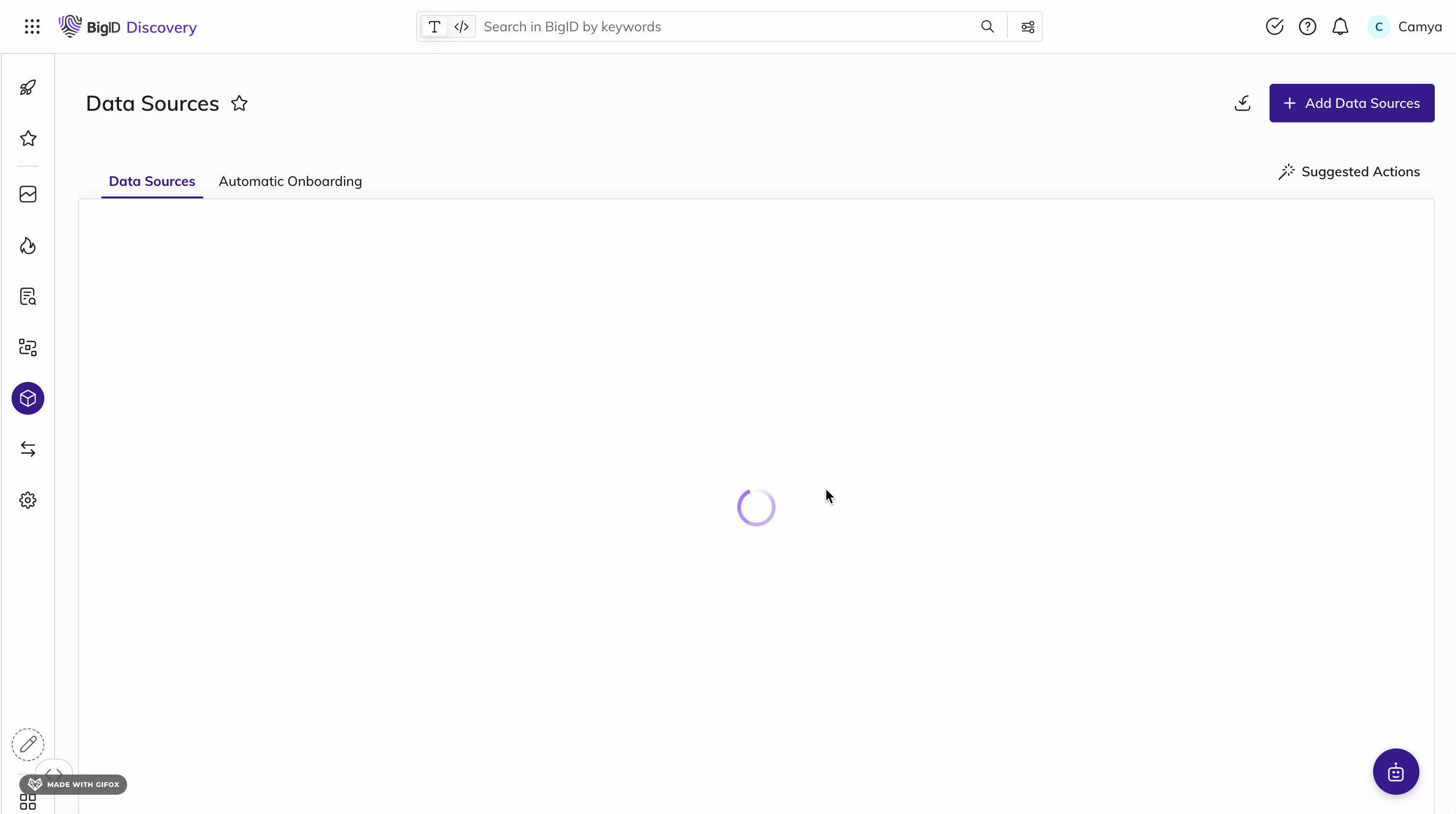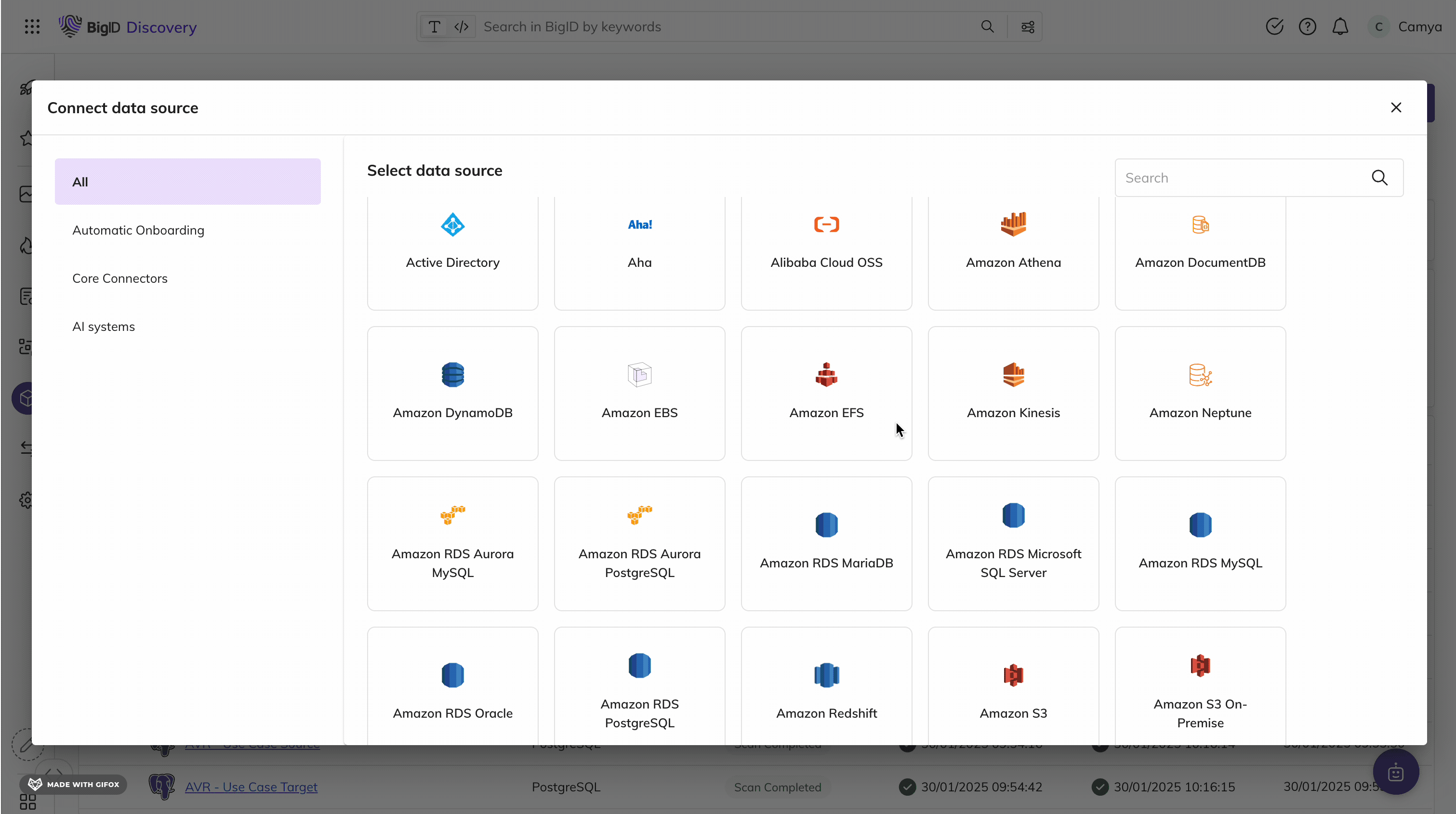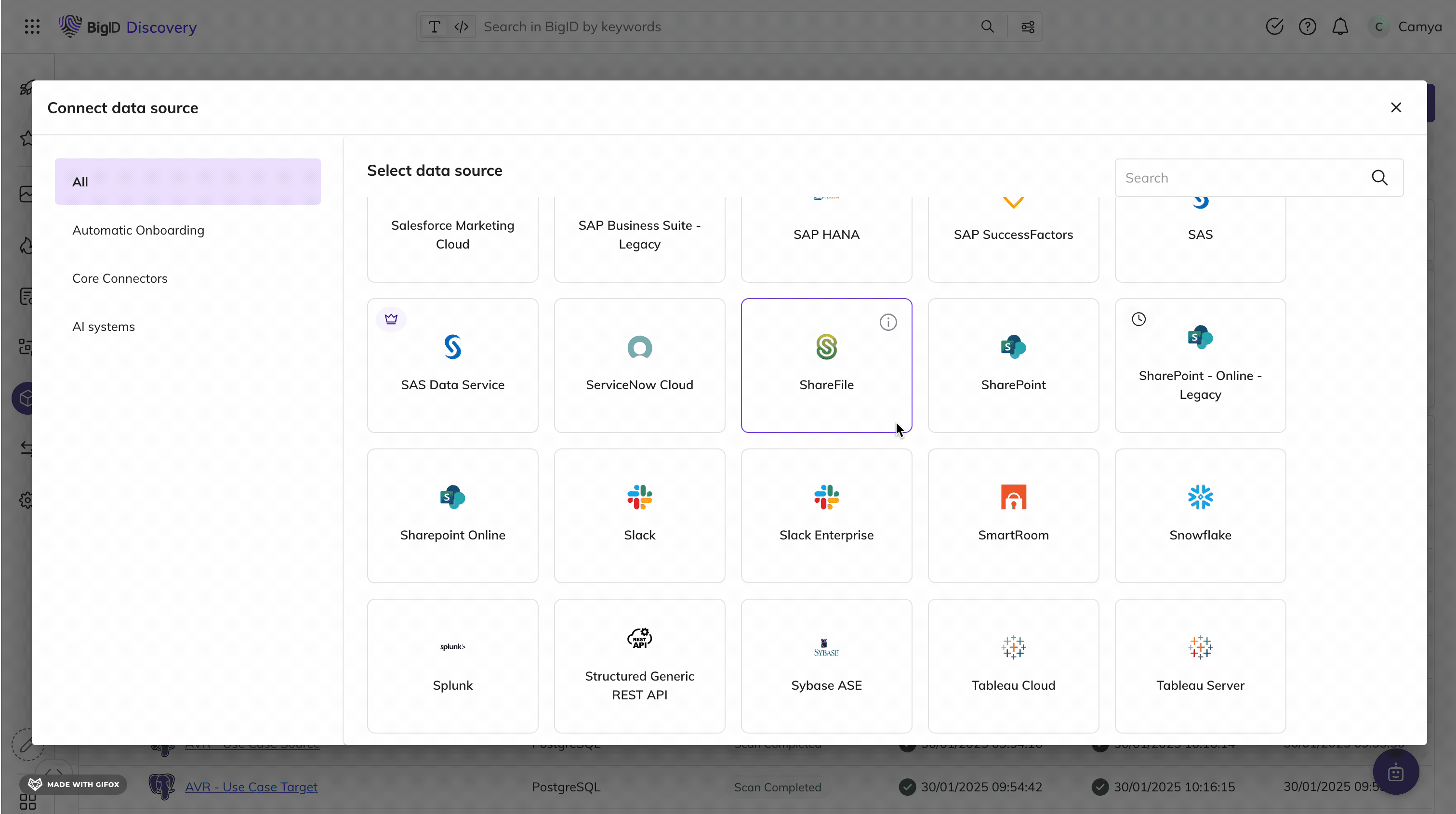
Shine a Light on Dark Data
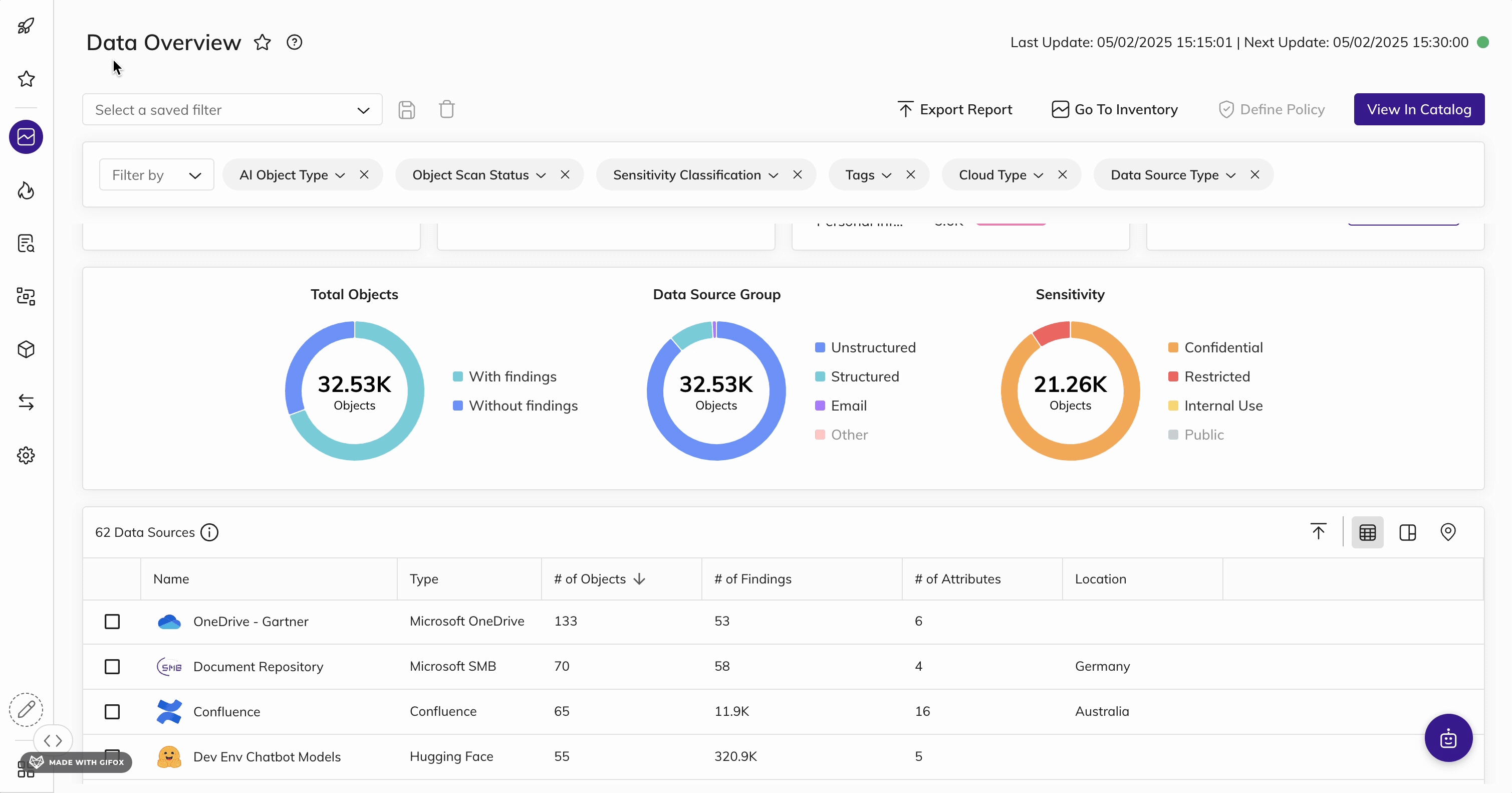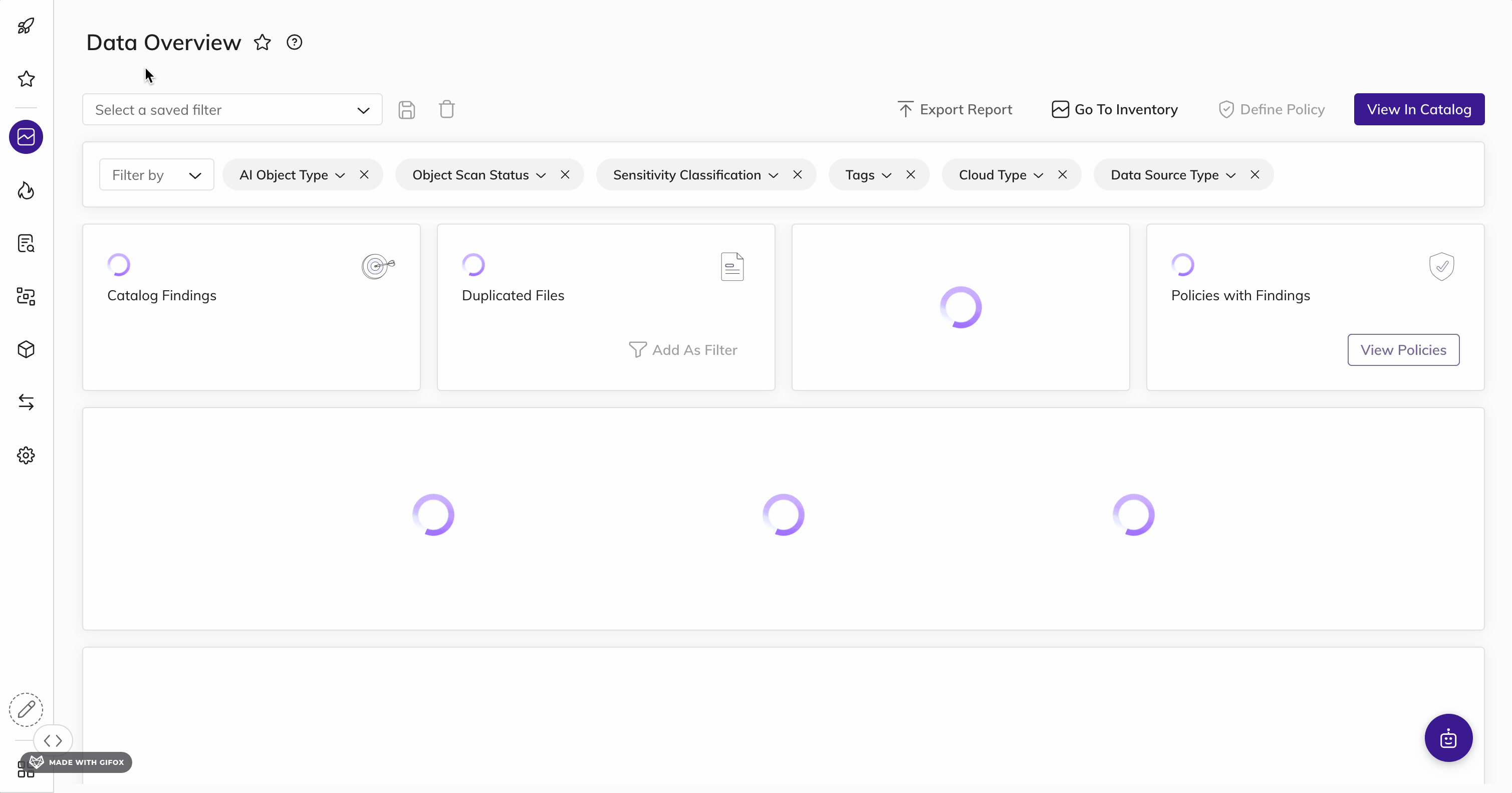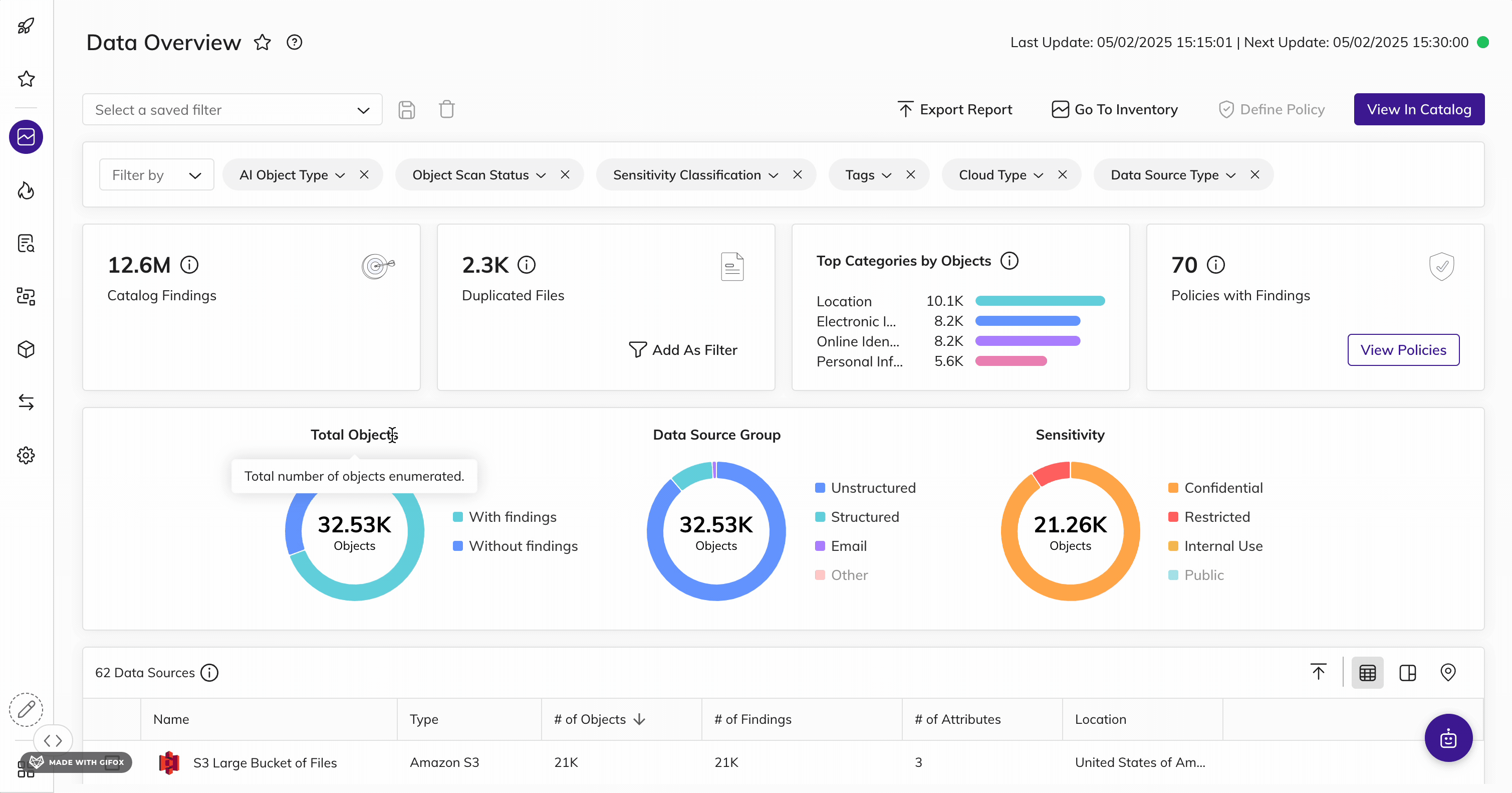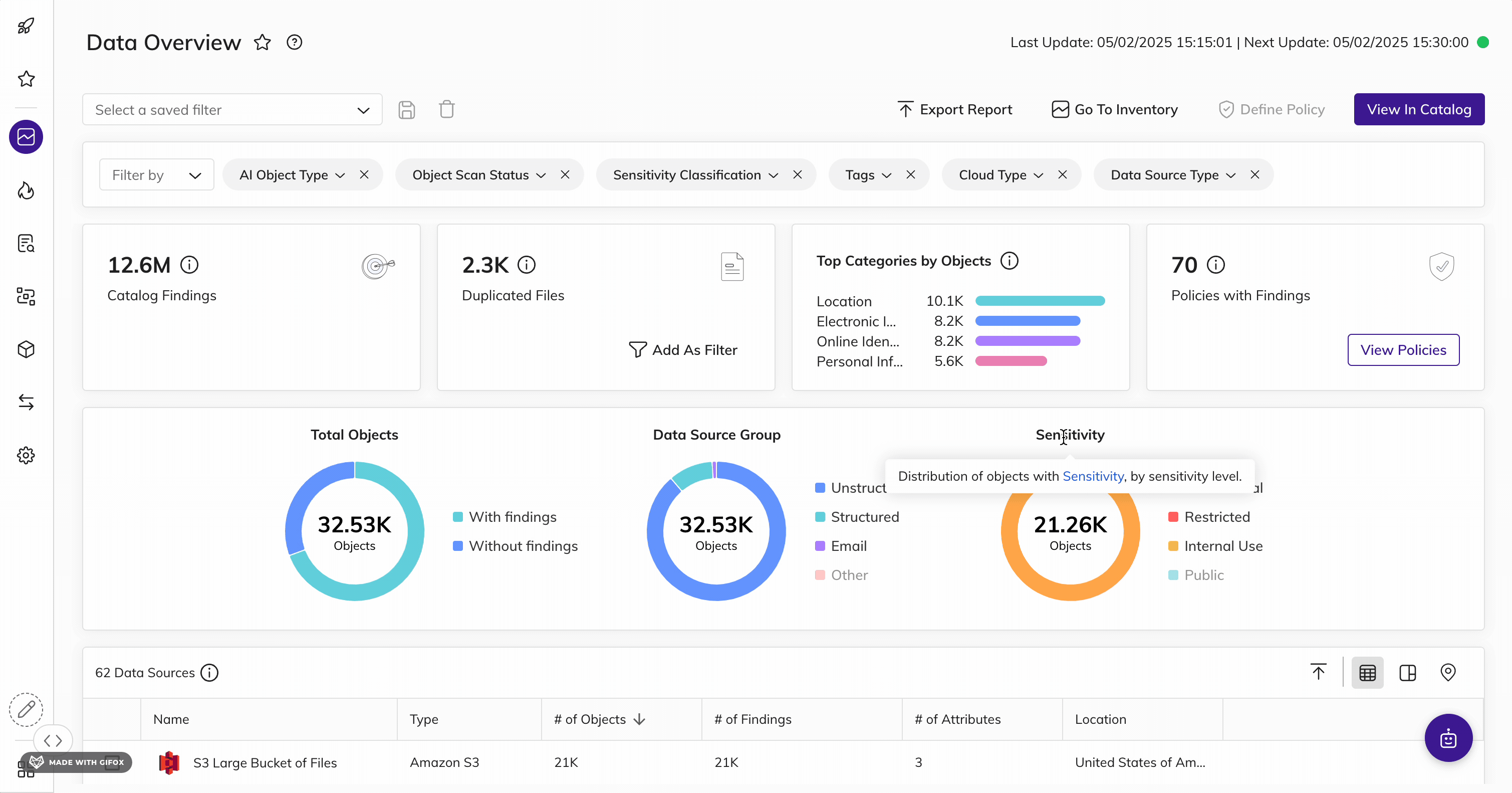
Automatically find and inventory your most sensitive, critical, and high-priority data - wherever it lives.
Get unmatched data discovery and classification to find and protect the data that matters most to you: whether it's critical, regulated, personal, secrets, passwords, IP, financial, or more across structured and unstructured data. Get more accurate results every time with ML-driven data classification - across your entire data landscape (from on-prem to cloud to everywhere in between).
Streamline Data Protection Workflows
Remediate high-risk, sensitive, & critical data, everywhere.
Make it easier than ever for the right people to take the right actions, on the right data. Manage data protection all in one place - a single pane of glass to annotate, delete, quarantine, archive, mask, encrypt, and anonymize sensitive data.
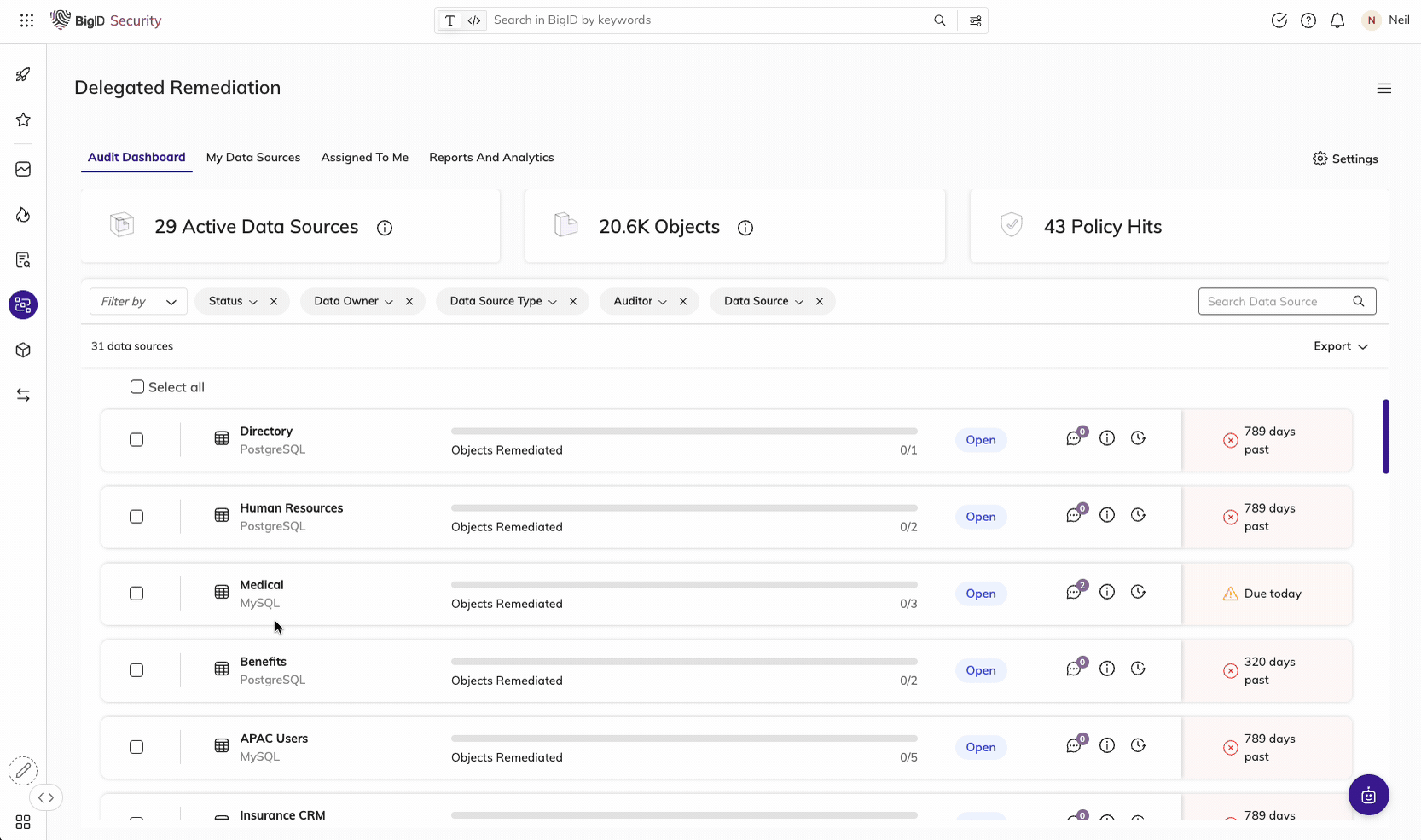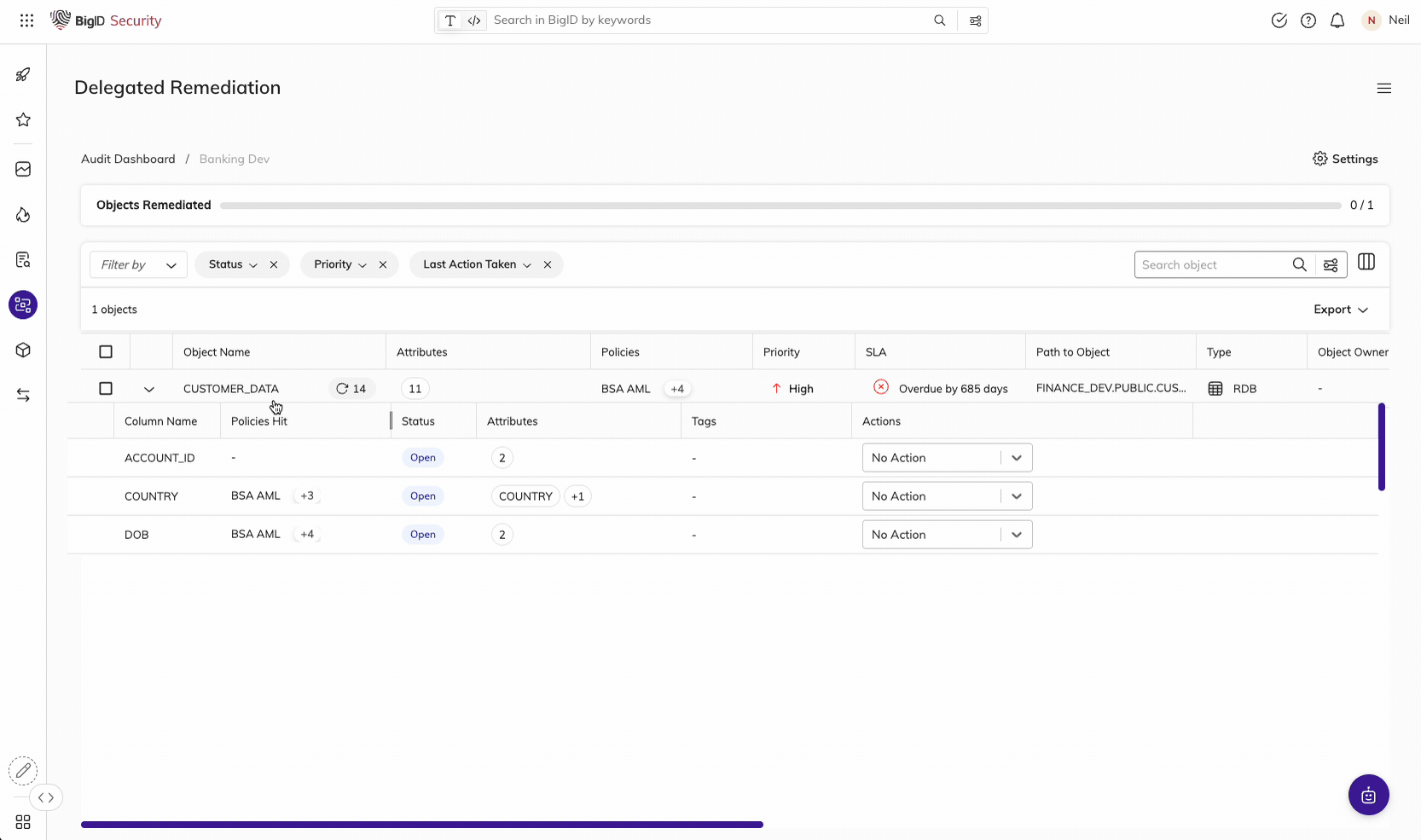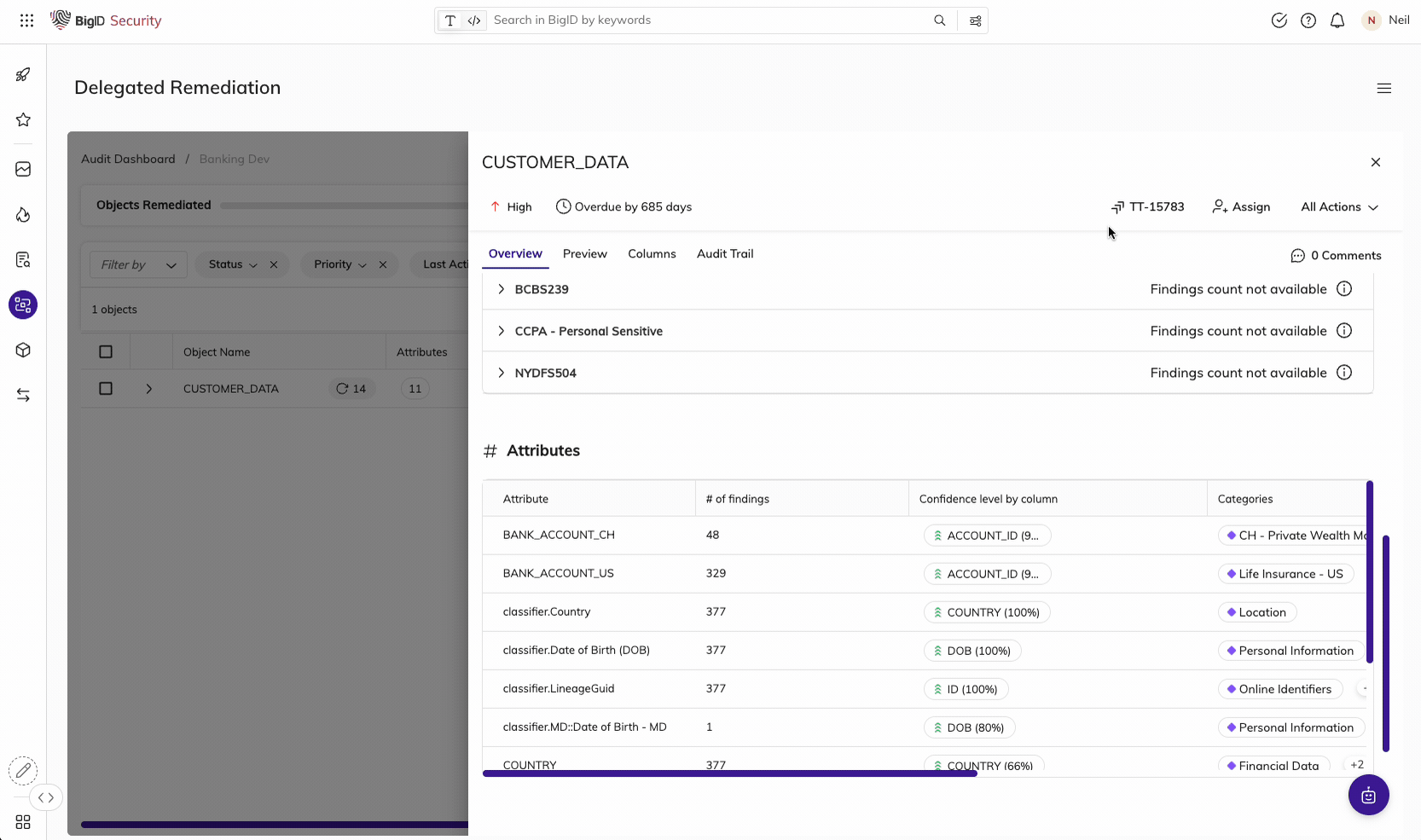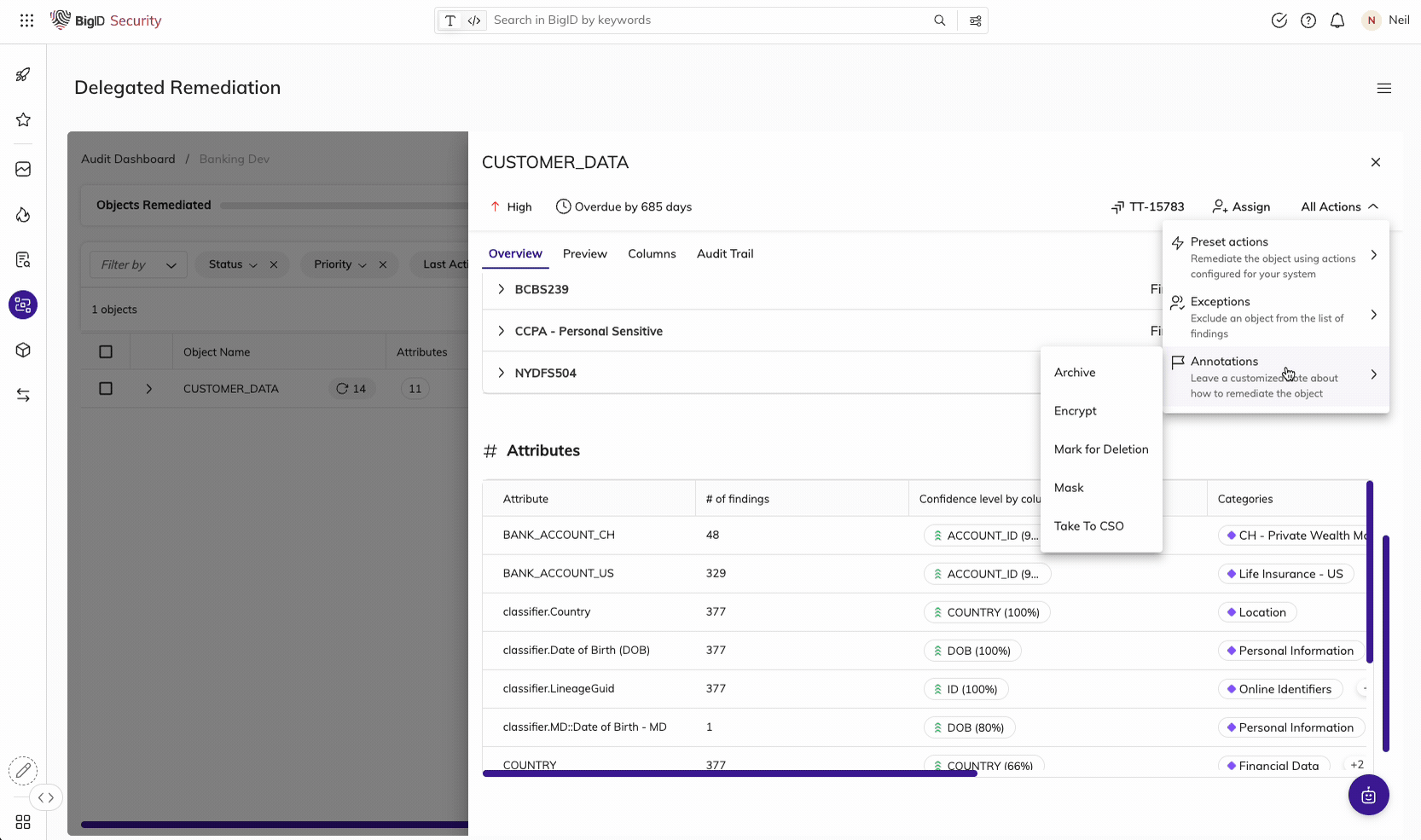
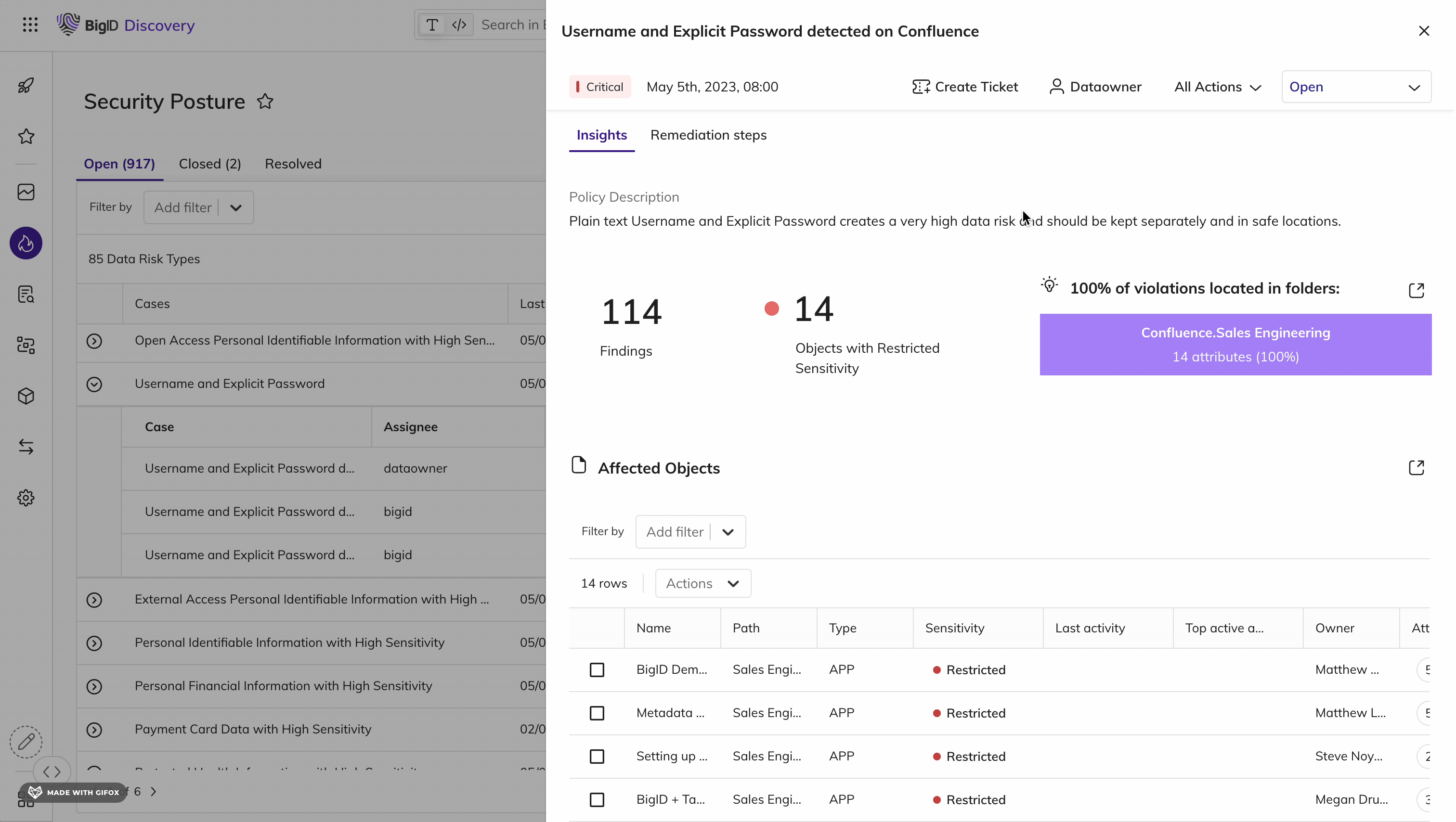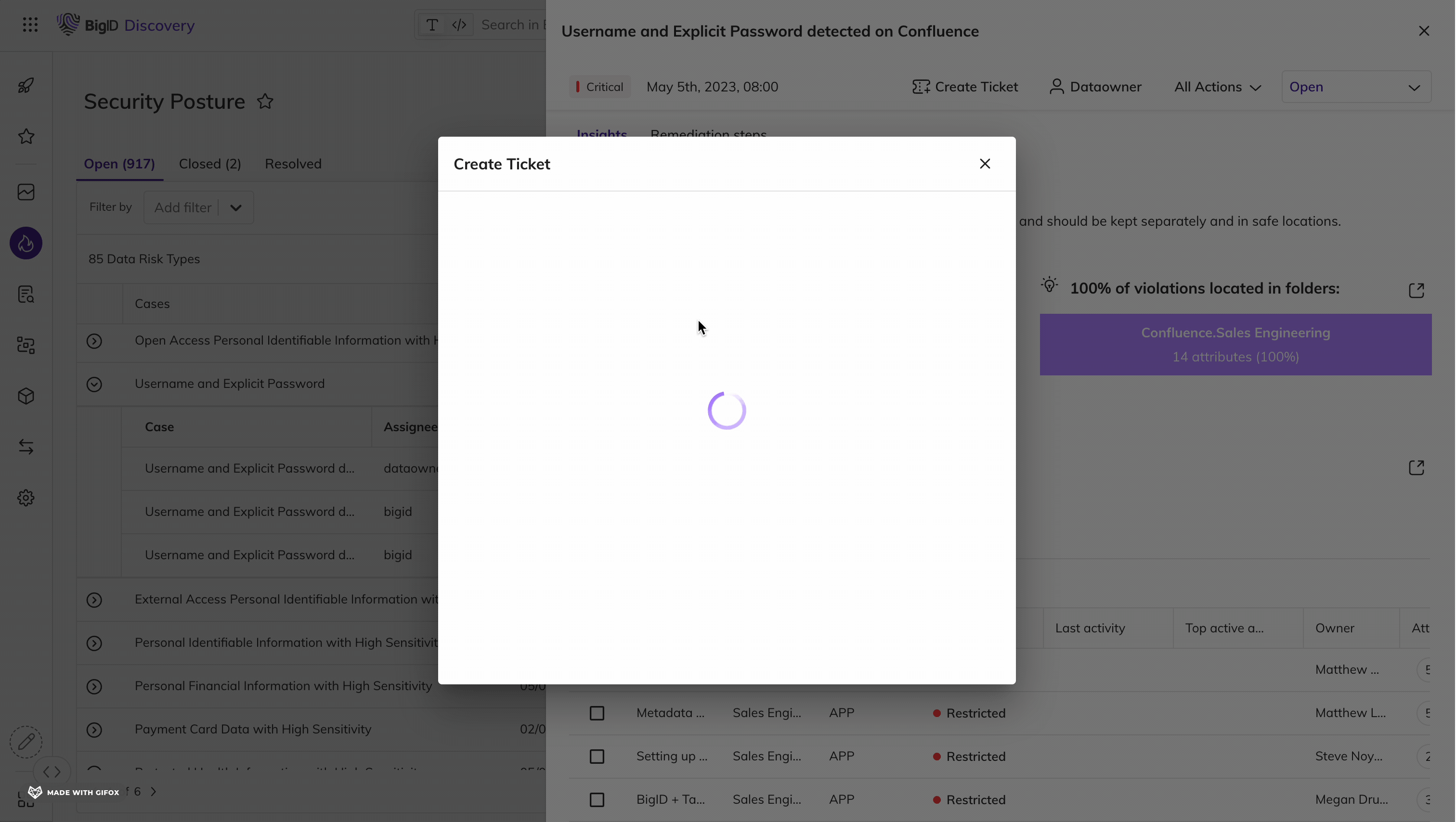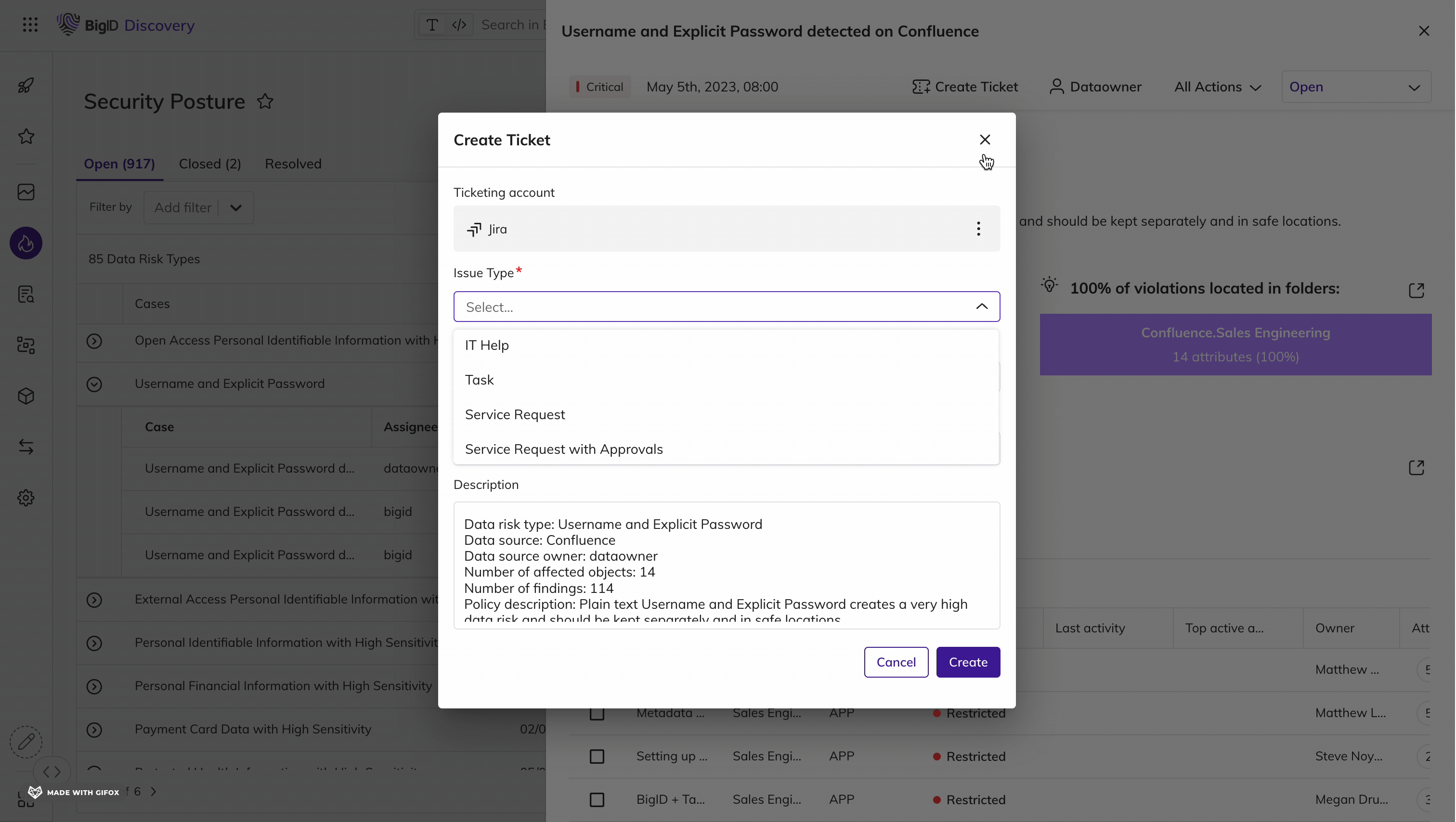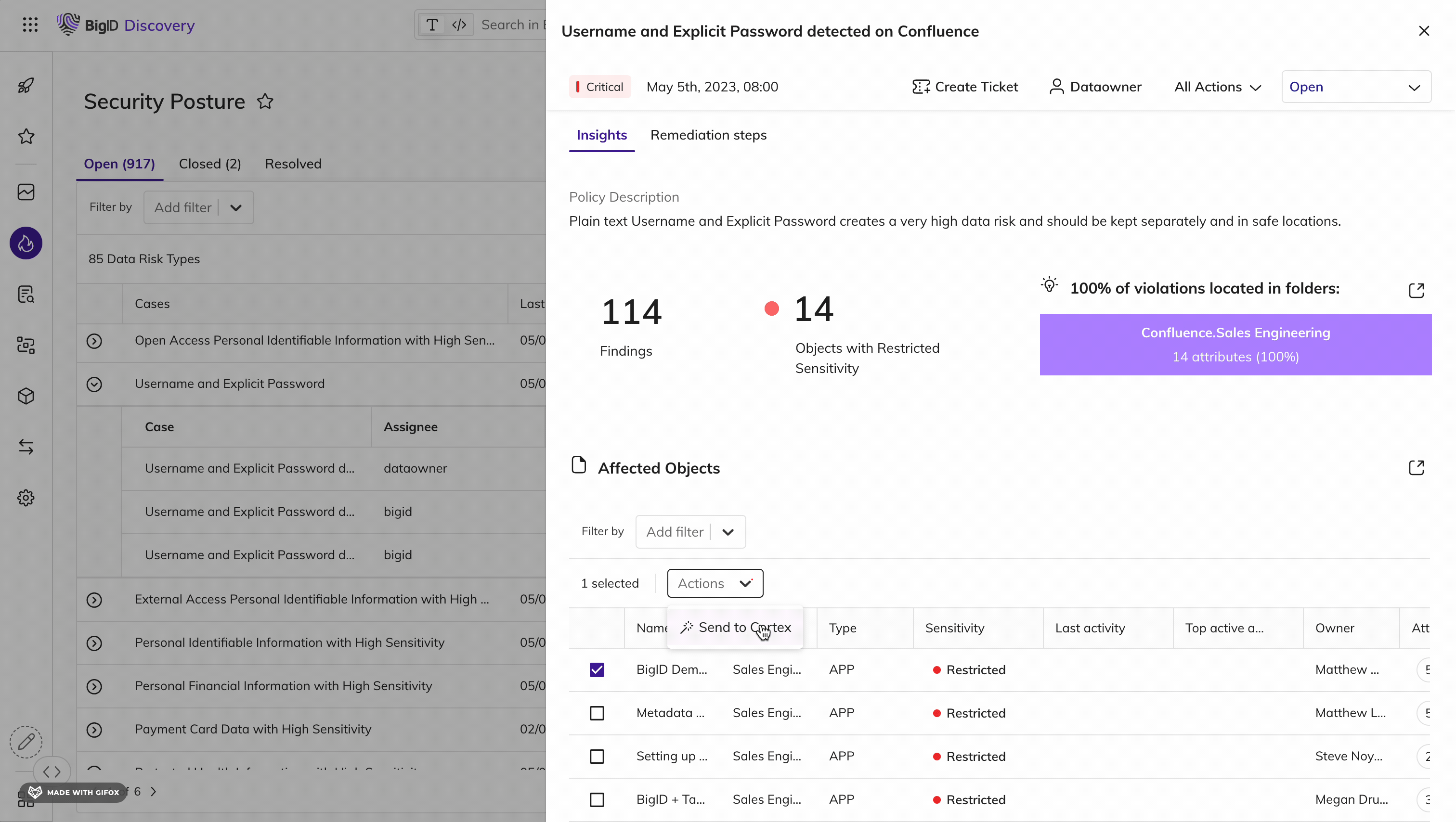
Take Action on the Data that Matters Most
Delegate decisions to the right people, and make better data-driven decisions.
Assign findings and tasks to the right data owners, take action on the right data, and maintain an audit trail of all data protection activity. Enforce and prioritize your remediation actions by policy and report on actions taken on sensitive data.
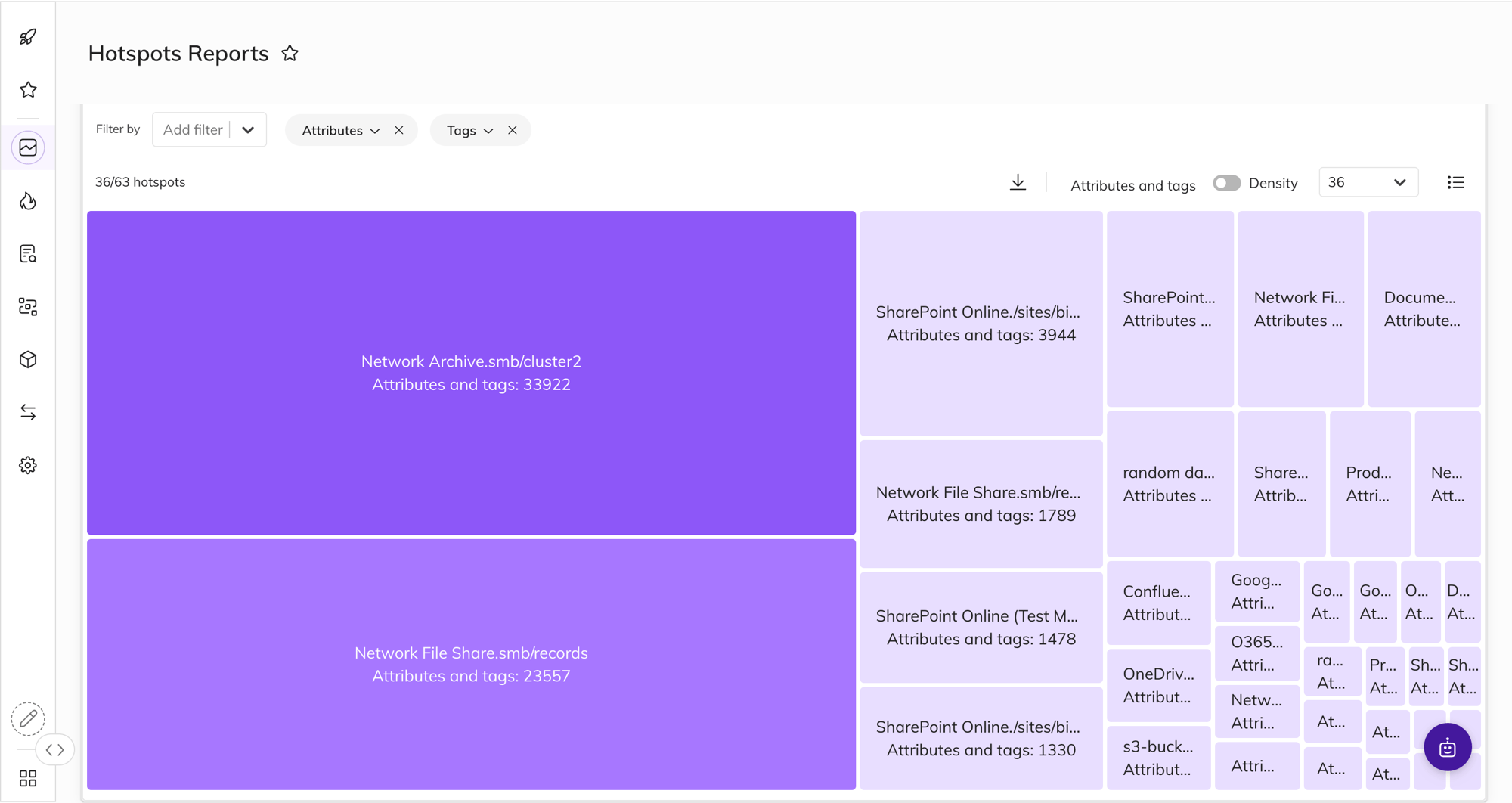
Prioritize Data Protection By Risk
Identify & protect higher risk data vulnerabilities
Manage open issues based on risk, context, and priority – and customize your data protection actions and policies. Drill down into the data to see policies, violations, activity, access issues, and more.
.gif?width=1663&height=1015&name=Data%20Risk%20Management%20(DSPM).gif)
Jumpstart DSPM
Data Security Posture Management for the Multicloud and beyond
Accelerate DSPM: manage risk across the multicloud with a data-centric approach. Automatically map, monitor, and remediate data – with the first platform based on ML-driven in depth data discovery and automation.
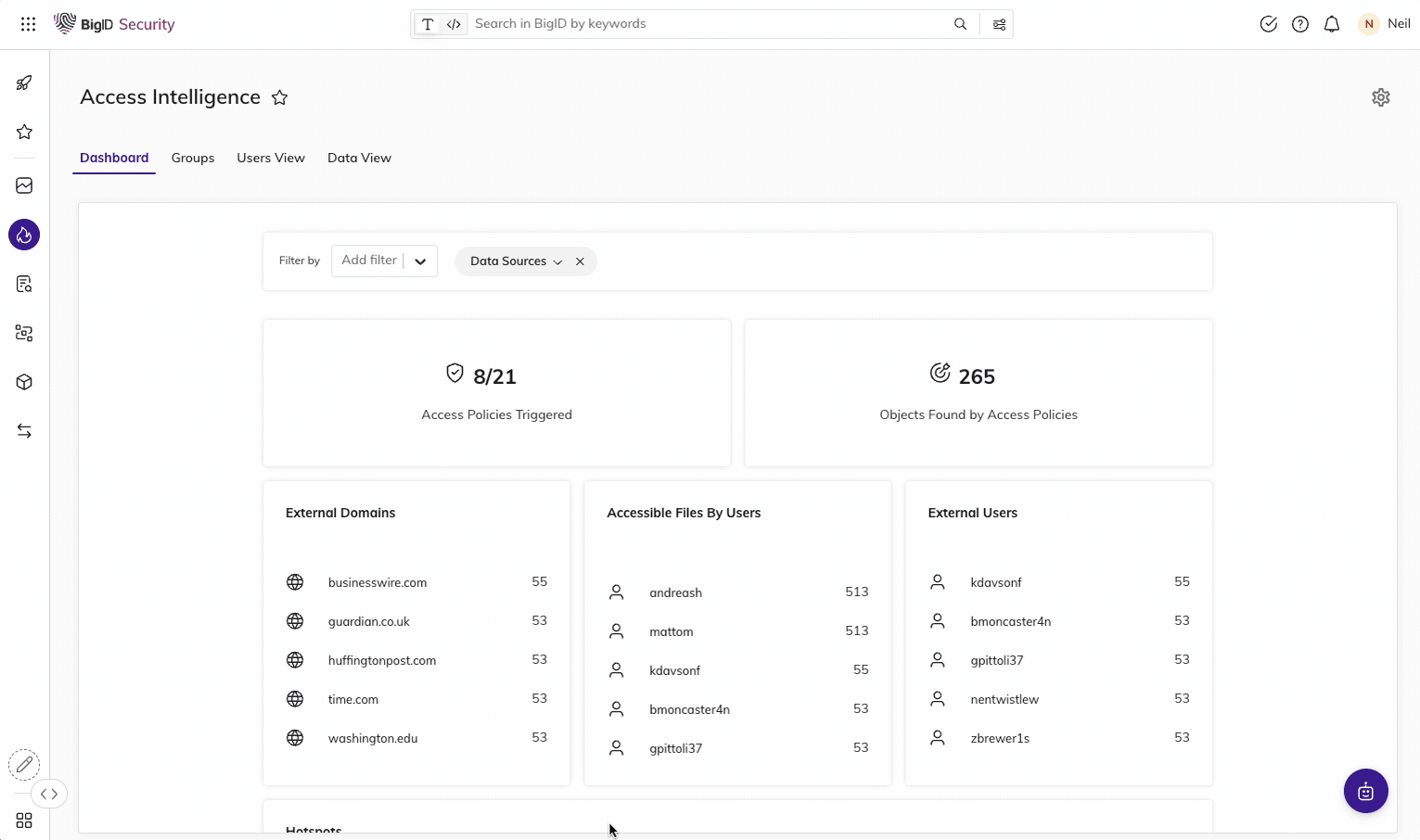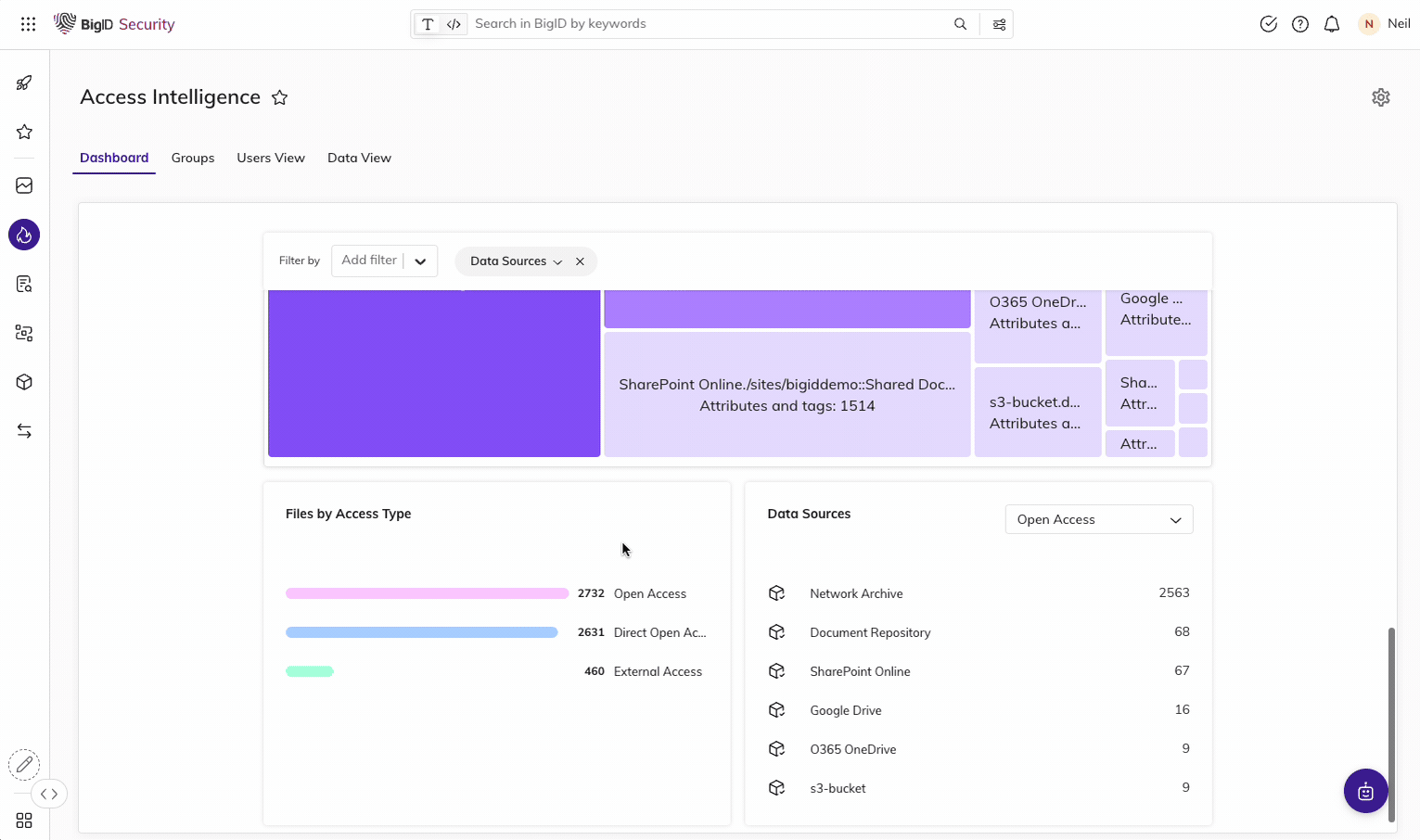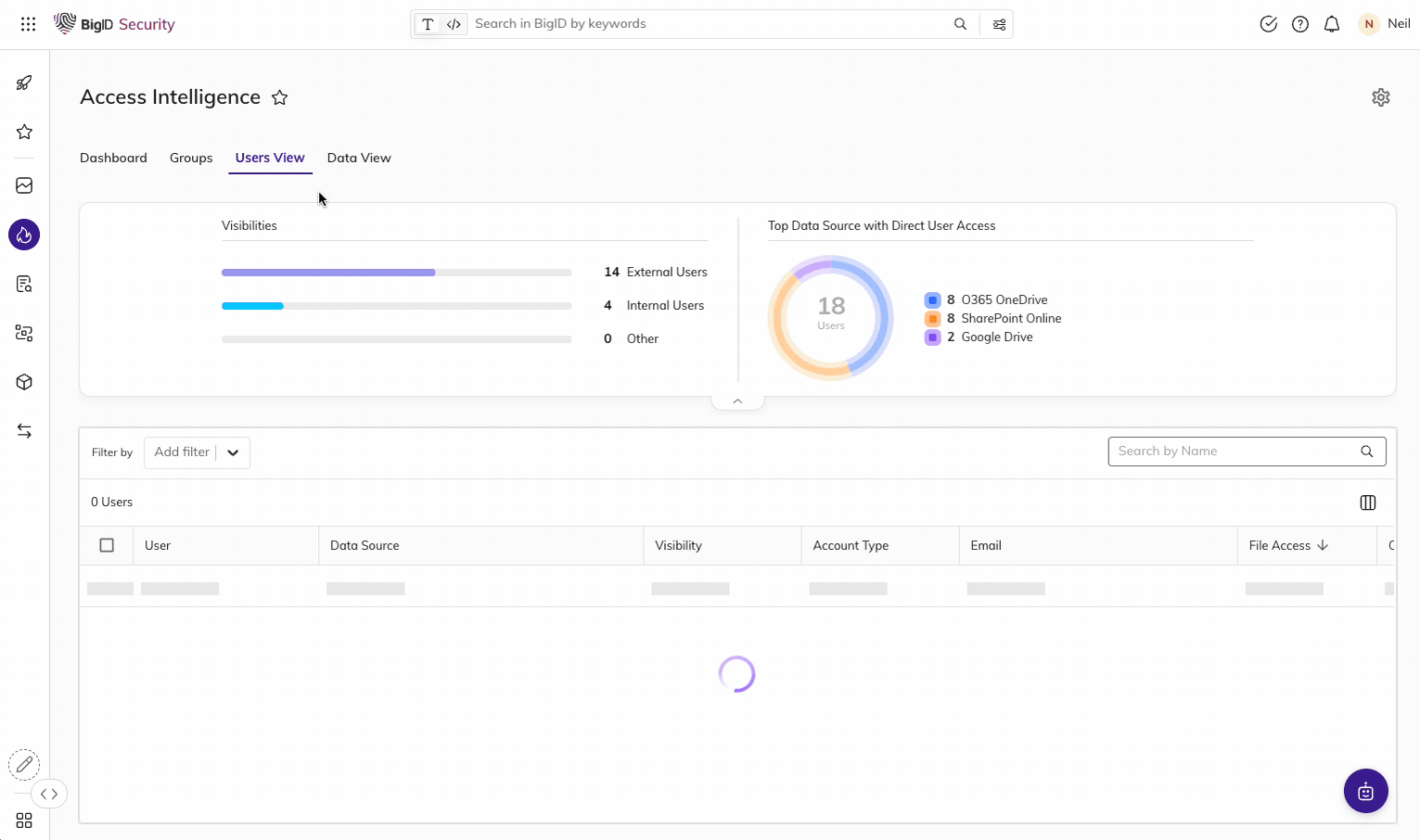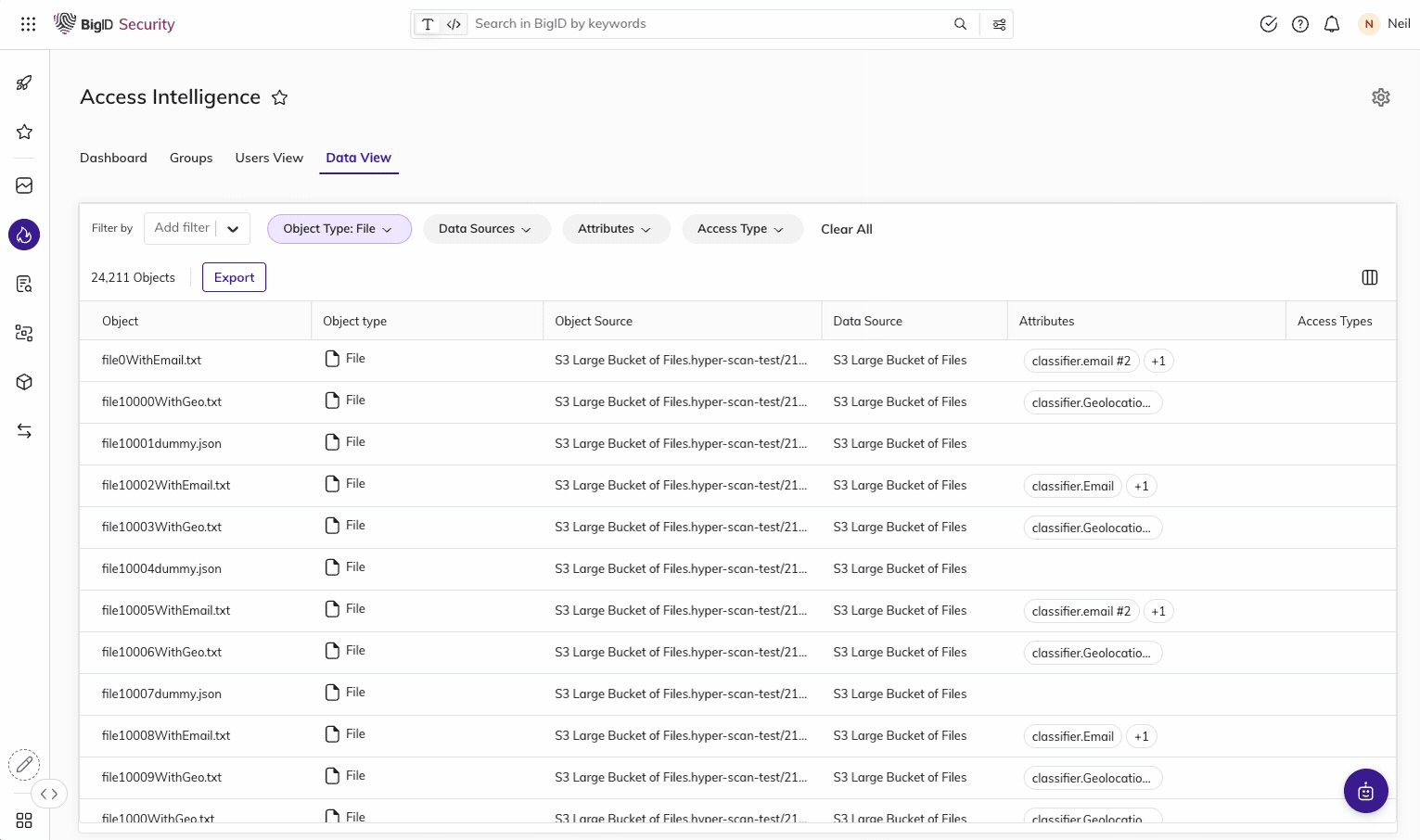
Enable Zero Trust for Data
Identify & remediate high-risk data access issues.
Easily find over-permissioned and over-exposed data across your entire data landscape: mitigate unauthorized use, reduce the risk of data leaks or breaches., and get to a least privileged permissions model for zero trust.
The State of Data Security in 2022
Get insight into the state of today’s overarching data security practices with this exclusive survey from over 400 IT and Security leaders, brought to you by Gartner & BigID.
