Remediate and Protect High Risk, Sensitive Data
Fortify your data security strategy to find and remediate high-risk, sensitive, and regulated data. Reduce risk and take action to minimize your attack surface, achieve compliance, and improve data protection.
Talk to one of our data remediation security specialists 👇 and check out what we put together for you below.
.png)
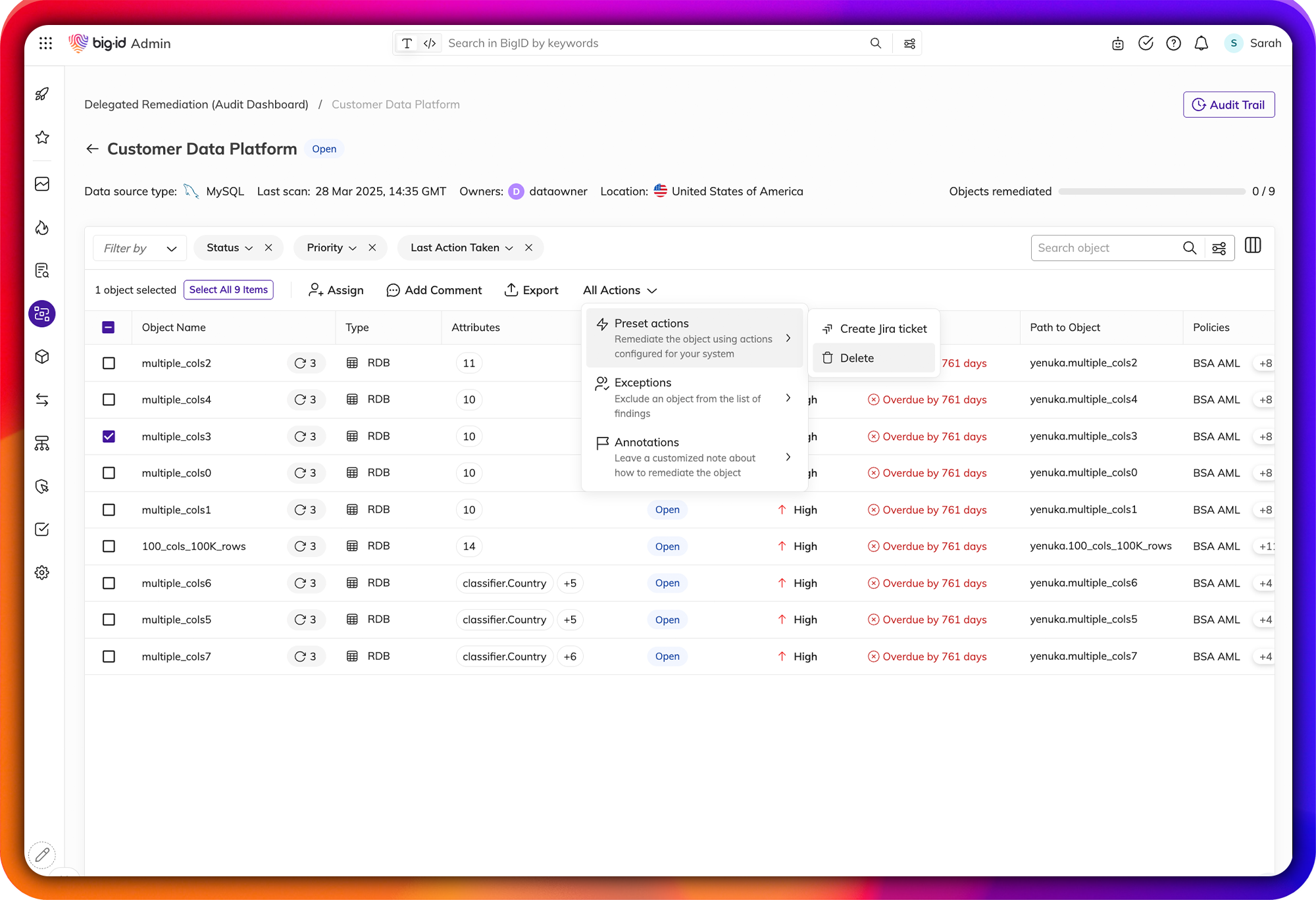
Streamline Data Protection Workflows & Remediate Risk
Remediate high-risk, sensitive, & critical data, everywhere.
Make it easier than ever for the right people to take the right actions, on the right data. Manage data protection all in one place - a single pane of glass to annotate, delete, quarantine, archive, mask, encrypt, and anonymize sensitive data.
Assign findings and tasks to the right data owners, take action on the right data, and maintain an audit trail of all data protection activity. Enforce and prioritize your remediation actions by policy and report on actions taken on sensitive data.
Data-Centric, Risk-Aware Security for AI in the Multi-Cloud & Beyond
Get ahead of AI security challenges with a data-first approach.
BigID helps you proactively identify sensitive, toxic, and high-risk data fueling AI models, so you can reduce exposure, ensure compliance, and minimize risk. Whether it's PII, IP, or shadow AI, BigID gives security teams the visibility and control they need across multi-cloud and on-prem environments, from training data to AI pipelines.
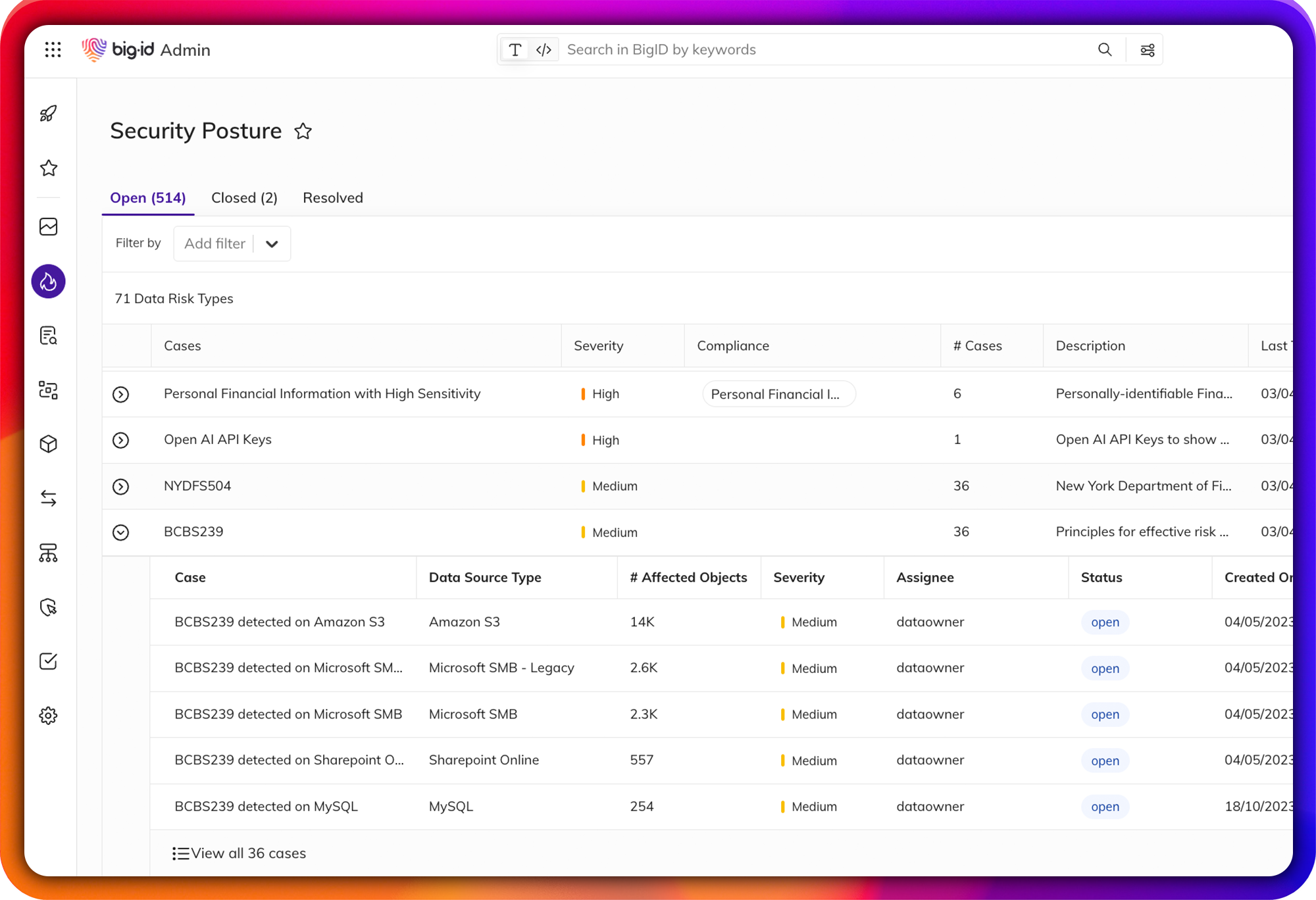
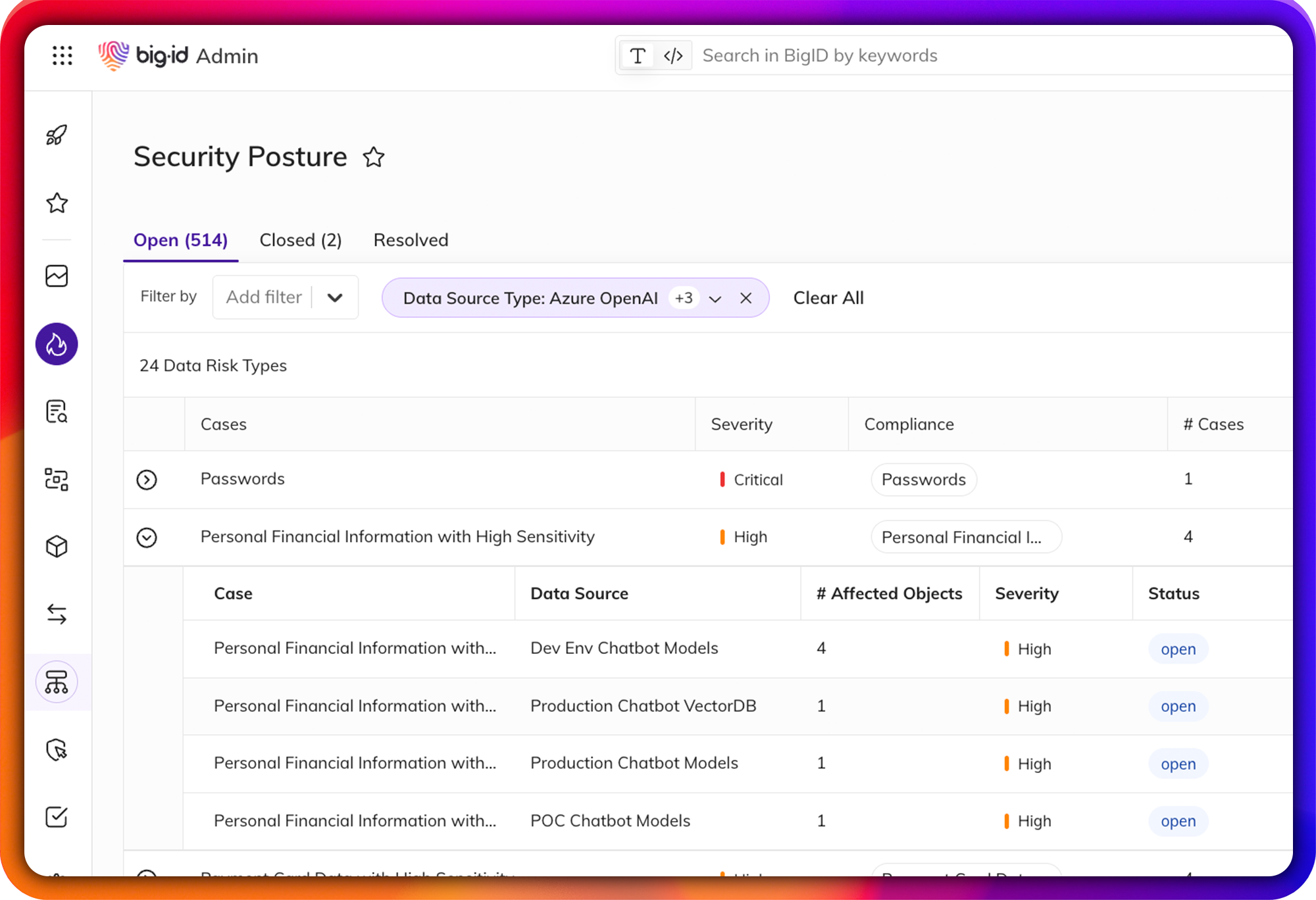
Jumpstart DSPM
Data Security Posture Management for the Multicloud and beyond
Accelerate DSPM: manage risk across the multicloud with a data-centric approach. Automatically map, monitor, and remediate data – with the first platform based on ML-driven in depth data discovery and automation.
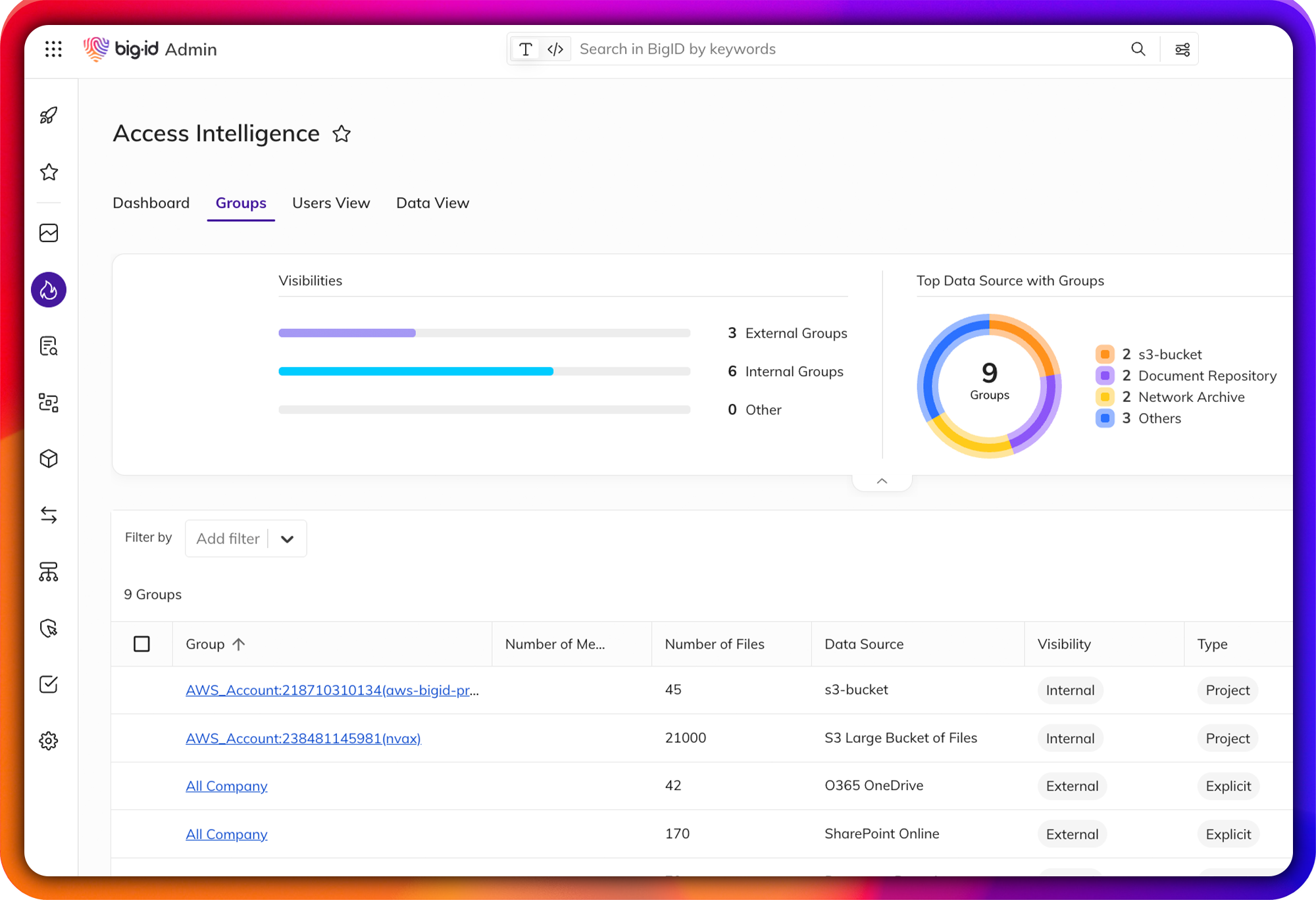
Enable Zero Trust for Data
Identify & remediate high-risk data access issues.
Easily find over-permissioned and over-exposed data across your entire data landscape: mitigate unauthorized use, reduce the risk of data leaks or breaches., and get to a least privileged permissions model for zero trust.
-1.png?width=2000&height=1368&name=data-overview%20(1)-1.png)
Shine a Light on Dark Data
Automatically find and inventory your most sensitive, critical, and high-priority data - wherever it lives.
Get unmatched data discovery and classification to find and protect the data that matters most to you: whether it's critical, regulated, personal, secrets, passwords, IP, financial, or more across structured and unstructured data. Get more accurate results every time with ML-driven data classification - across your entire data landscape (from on-prem to cloud to everywhere in between)
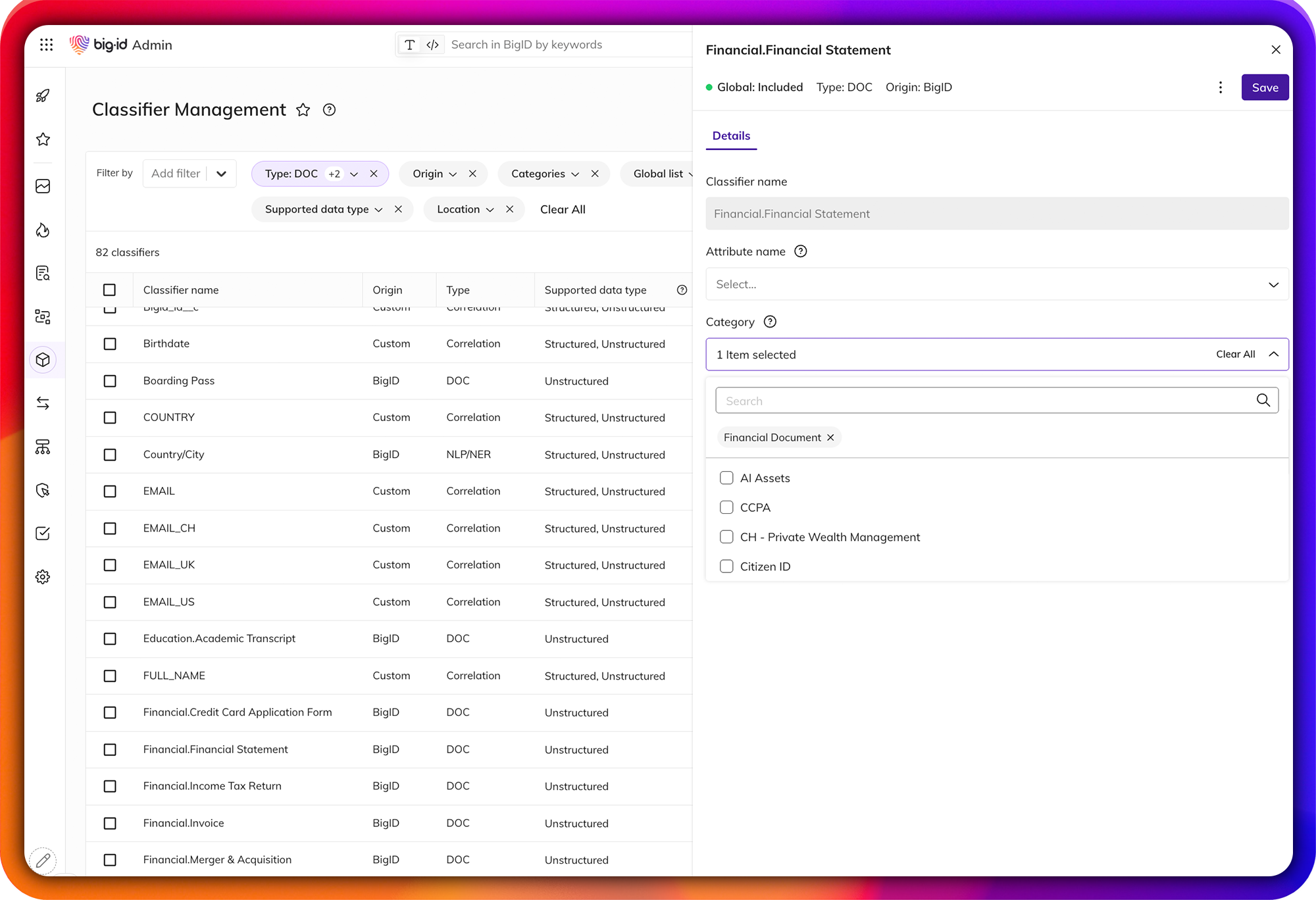
Advanced Sensitivity Classification
Achieve unparalleled accuracy and scalability in data classification.
Go beyond traditional pattern-matching and regular expression (RegEx) with advanced, trainable ML and NLP-based classification. Create custom classifiers that can be tailored specifically to your unique data environment. Test and fine-tune them before deployment to enhance accuracy and mitigate the number of false positives. Label and tag all of your data using a single unified classification ruleset.
Data Security Posture Management (DSPM) for 2025 & Beyond
Stay on the cutting edge of DSPM with the latest innovations and best practices covered in our ultimate guide. We'll dive into the critical capabilities of DSPM and how BigID's pioneering approach enables organizations to keep their data safeguarded, secure, and compliant for 2025 and beyond.

How the US Army Ensures
Their Data is in the Safe Zone
BigID has equipped the US Army with the ability to illuminate dark data, accelerate cloud migration, minimize redundancy, and automate data retention. The result? Enhanced security, minimized risks, and streamlined data management across diverse platforms. See how BigID can help do the same for your organization.

How The University of Maryland Saved $5 Million in Risk Exposure
The University of Maryland used BigID to uncover and reduce over $5M in data risk across 2.5PB of cloud storage. With deep discovery and classification across Google Drive, O365, and Box, they identified and cleaned up thousands of exposed PII records—boosting compliance, minimizing exposure, and improving visibility across their data.
