Comply With the ITAR & Protect US National Security
See how organizations like yours can comply with the International Traffic in Arms Regulations (ITAR) to uphold US national security and foreign policy interests. With BigID, you can identify and secure your defense data to reduce the risk of data breaches and leaks.
Talk to one of our data-centric ITAR specialists 👇 and check out what we put together for you below.
Recognized as the #1 industry-leading data security, privacy, compliance, and AI solution



-1.png?width=152&height=193&name=image%20(23)-1.png)

5 Reasons Why You Should Choose BigID for ITAR
Coverage
Support for 100’s of data sources and types - unstructured or structured, on-prem or across the cloud to find all your technical data for ITAR. Accelerate insights and eliminate blind spots with Auto-Discovery.
Classification
Combines regular expression (RegEx) with advanced, AI and ML-based techniques to classify more data types important to ITAR, more accurately, at scale. Deploy hundreds of OOB classifiers. Build your tailored composite classifiers. Train your own NLP and deep learning classification models.
Risk Management
Extend data security and risk management to your defense and technical data from discovery through remediation. Take action on your data and streamline remediation. Automatically label, tag, retain, discard, encrypt, mask, and move risky and unnecessary data to reduce exposure.
Integrations
Open and API-first platform that integrates with and enriches the existing security stack. Seamlessly coordinate security and risk remediation workflows across the right tools. Our partners include ServiceNow, Palo Alto Networks, Splunk, Snowflake, Microsoft, Google, AWS, and more.
Enterprise-Grade
Choose how to deploy BigID: SaaS, self-managed, or hybrid. We use top-tier security including password vault, RBAC, and step-up authentication. Customize scans with features like API triggers, blackout periods, and iterative scans.
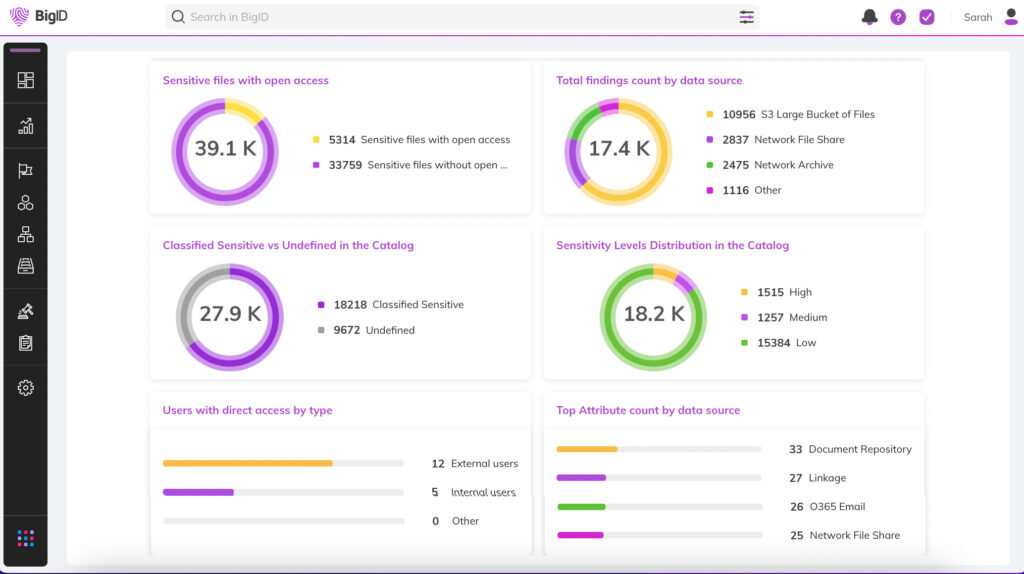
Shine a Light on Dark Data for ITAR
Automatically find and inventory your most sensitive, critical, and high priority data - wherever it lives.
Get unmatched data discovery and classification to find the data that matters most to the ITAR: whether it's critical, regulated, personal, secrets, passwords, IP, financial, or more. ITAR applies to information and data around military equipments, classified information about defense items and services, and software related to defense products.
Get more accurate results every time with ML-driven data classification - across your entire data landscape (from on-prem to cloud to everywhere in between).
Monitor Data Processing for ITAR
Build a Record of Processing Activities to map the data in your organization
Identify and document data inventory to visually map defense data across the organization to assess how data is processed, transferred, and shared across the enterprise and to third parties


Take Action on the Data that Matters Most to ITAR
Remediate high-risk, sensitive, & critical data, everywhere.
Make it easier than ever for the right people to take the right actions, on the right data. Annotate, delete, quarantine, and more based on the data itself - all while maintaining an audit trail.
Reduce the risk of data breaches and data leaks while staying compliant with ITAR requirements.
Enable Zero Trust for ITAR Data
Identify & remediate high-risk data access issues.
Flag potential foreign nationals in emails and documents that contain ITAR-related information. Investigate high-risk users and groups across your organization.
Easily find over-permissioned and over-exposed data across your entire data landscape: mitigate unauthorized use, reduce the risk of data leaks or breaches., and get to a least privileged permissions model for zero trust.

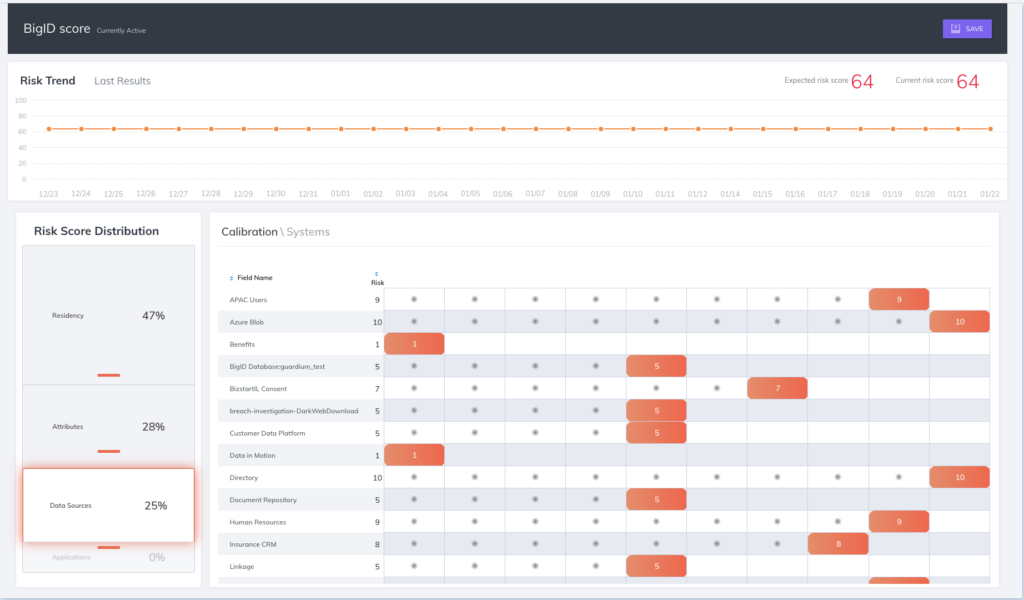
Customize Risk Scoring
Not all data is the same to the ITAR - define your crown jewel data to prioritize risk.
Define and monitor risk according to your sensitive or critical data - based on your own definitions and parameters. Automatically flag high-risk data and prioritize the most critical issues.
Simplify Incident Response
Determine breach impact & streamline incident response for ITAR regulators
Organizations must take steps to secure their defense data and implement a response plan in case of a breach of the ITAR.
Assess the scope of a breach, identify impacted users and determine appropriate response plans. Comply with breach reporting requirements to minimize financial, legal, and brand impact.
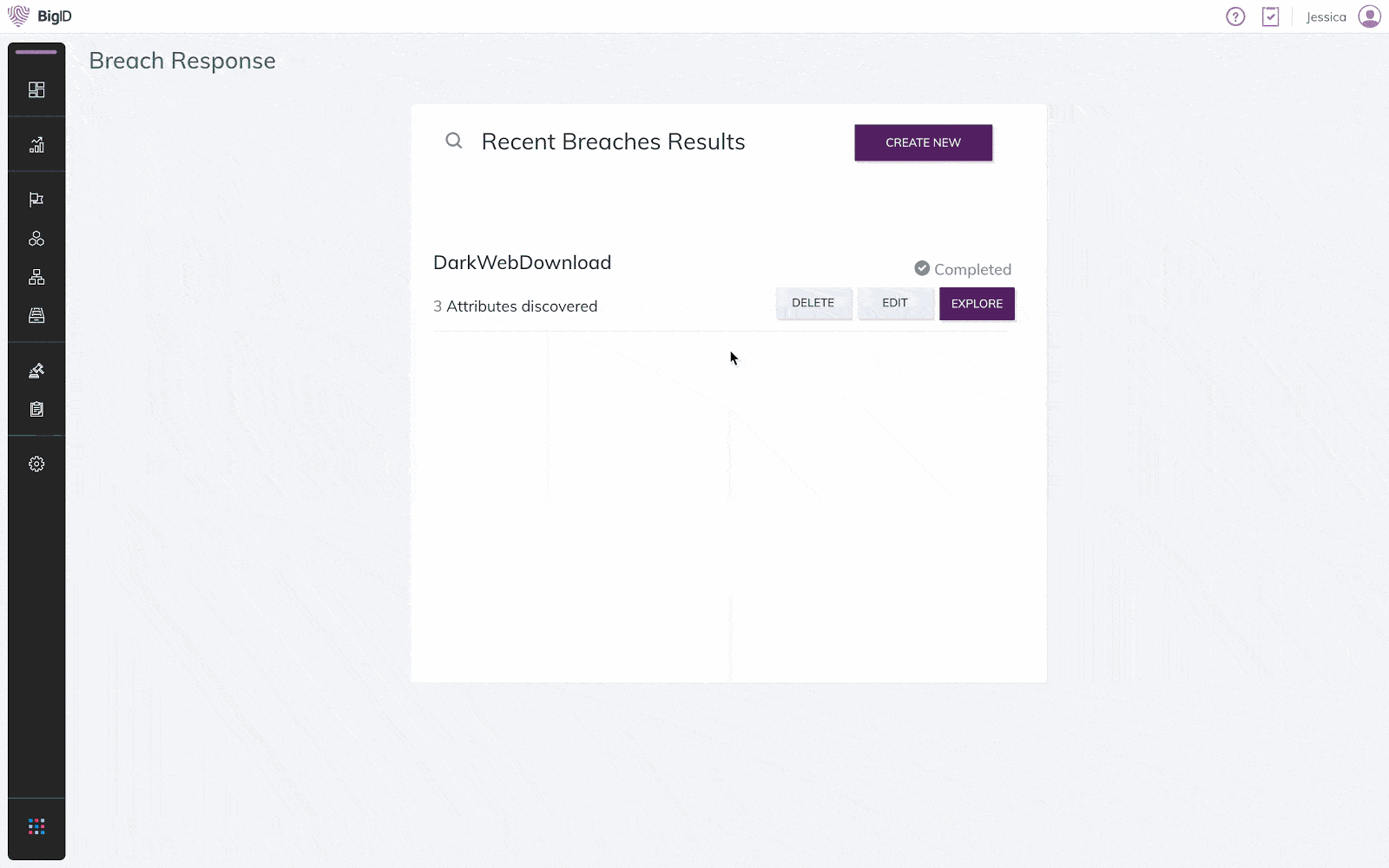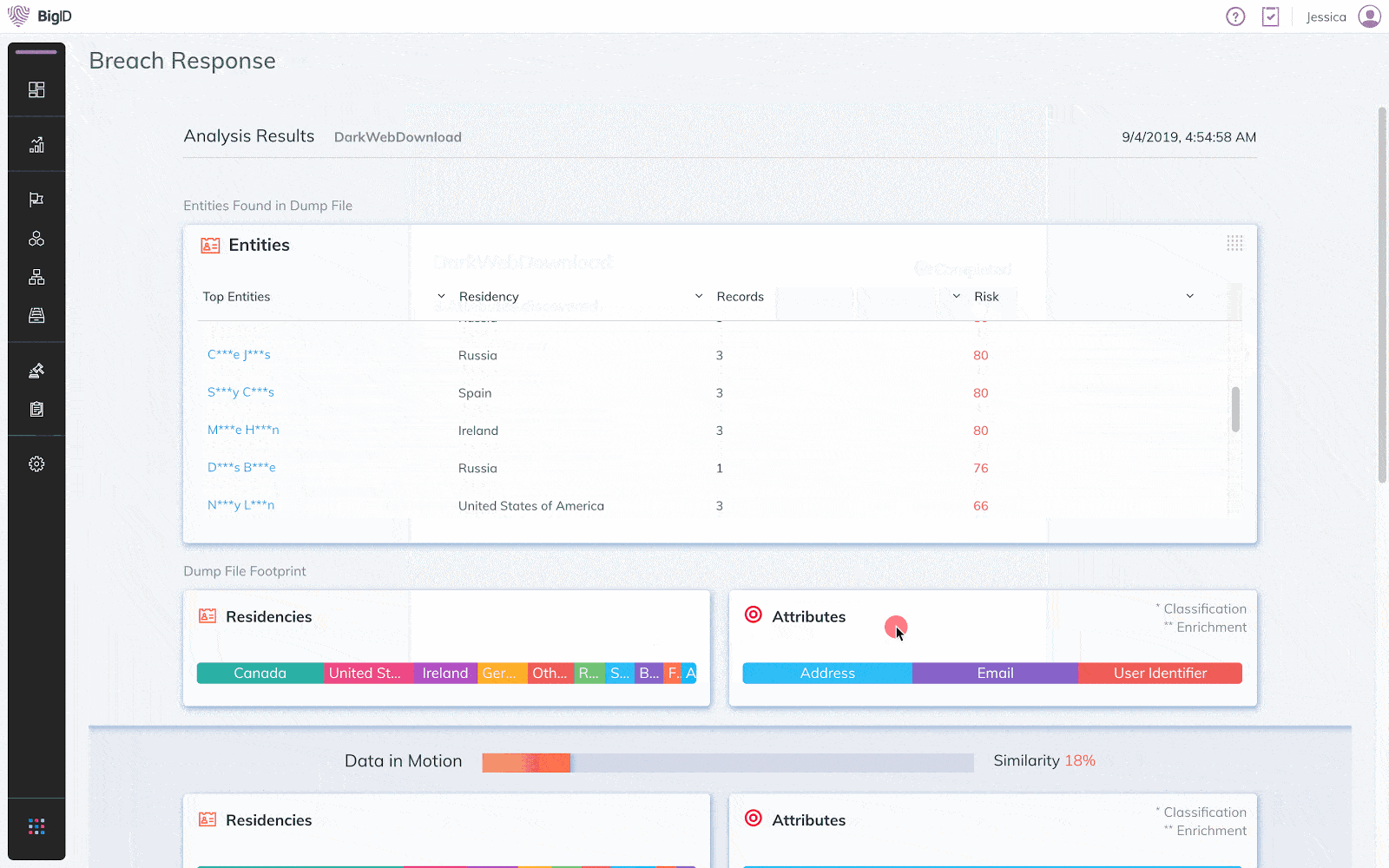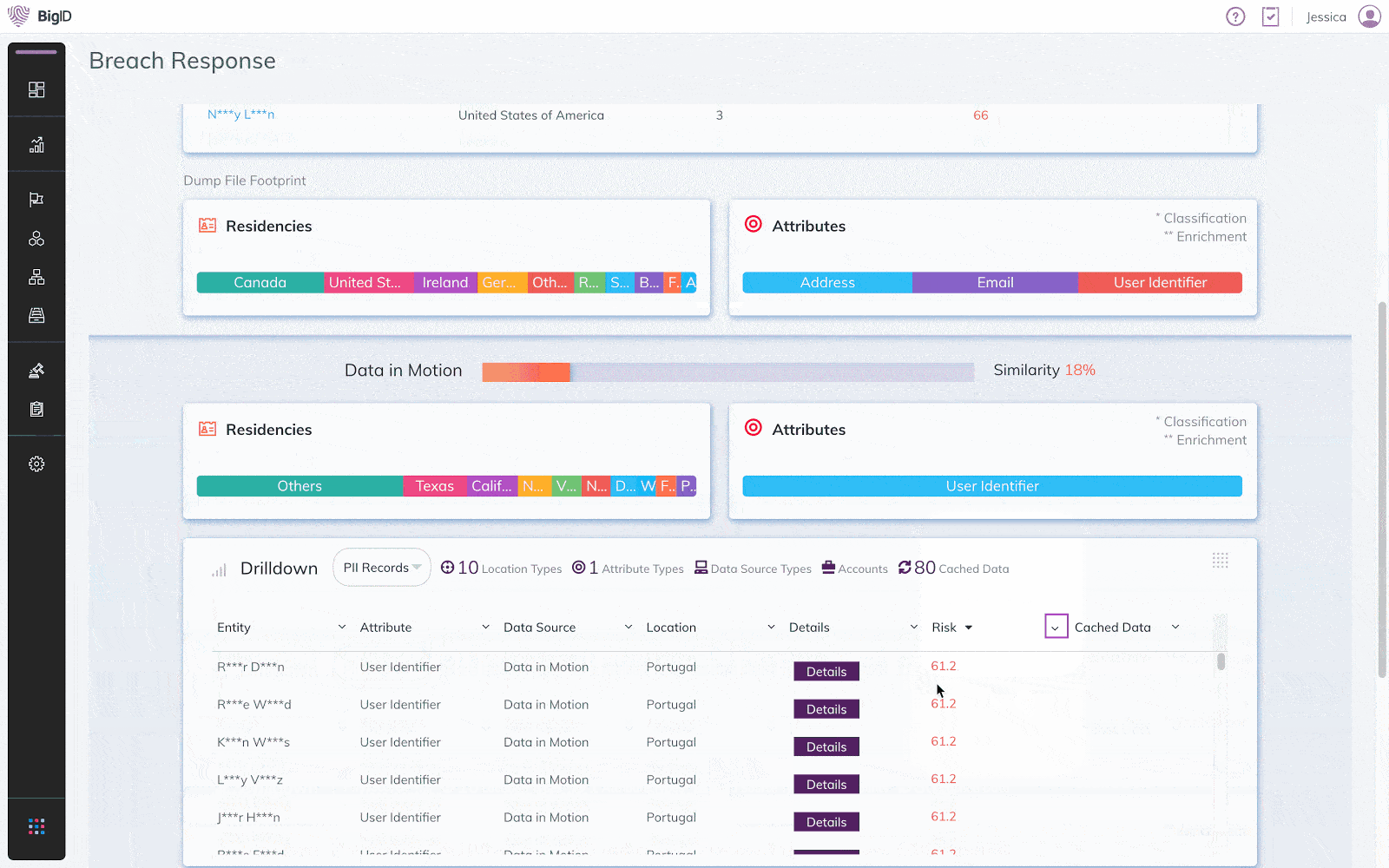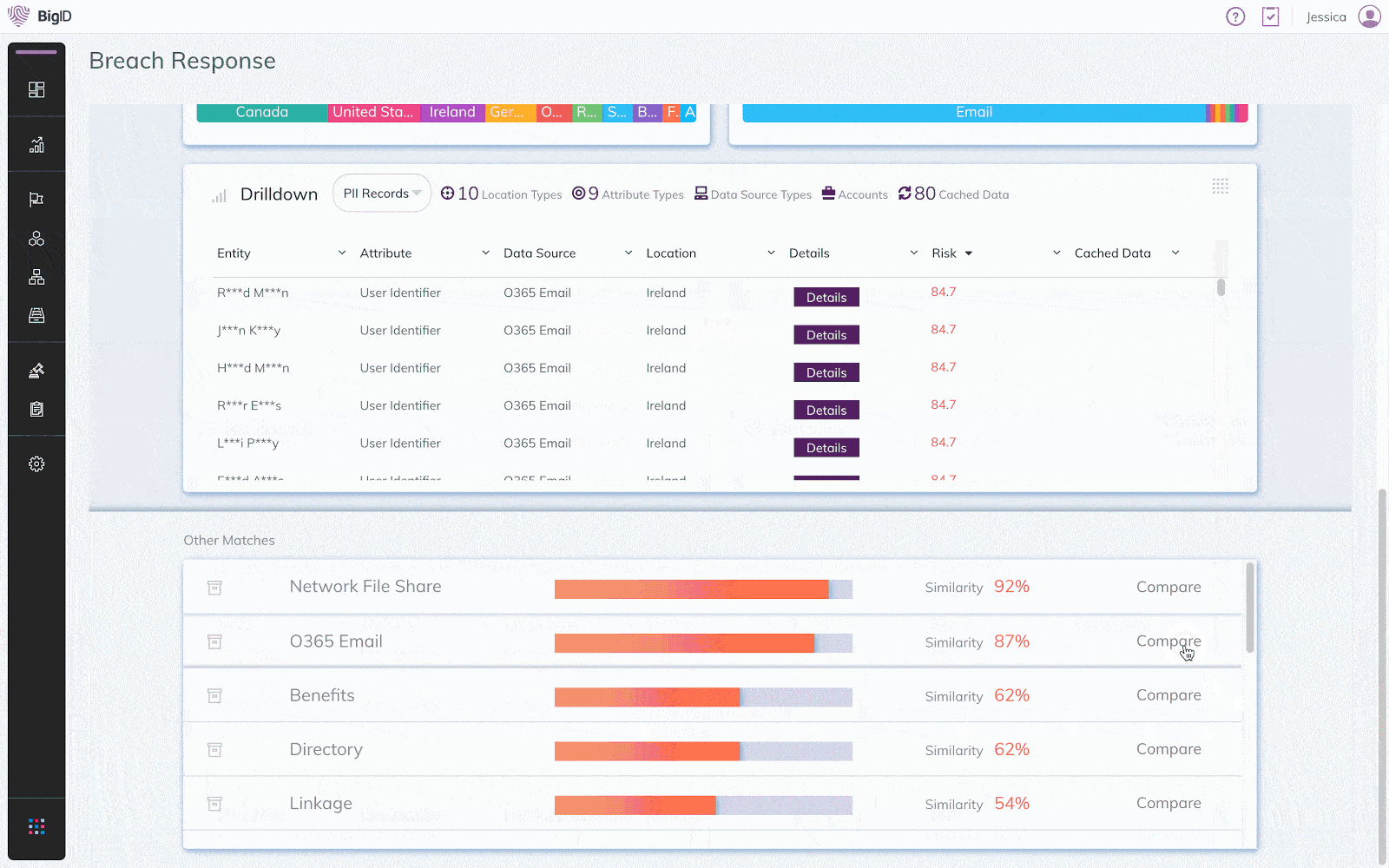
BigID is a Market Leader in Data Security Posture Management (DSPM)

"BigID embodies three major features we judges look for to become winners: understanding tomorrow's threats, today, providing a cost-effective solution, and innovating in unexpected ways that can help mitigate cyber risk and get one step ahead of the next breach."

FAQs About BigID
What data sources does BigID cover?
BigID covers over 500+ data sources across the cloud, on-prem data centers, and everywhere in between! We have unmatched coverage so you can find and classify sensitive data, wherever it lives. Connect to hundreds data sources natively: including SaaS, PaaS, IaaS, dev tools, apps, big data & NoSQL, email, and on-prem data centers - at petabyte scale.
Will BigID cover unstructured and semi-structured data?
We offer unparalleled coverage across all data types, from unstructured to semi-structured to structured data. This allows you to uncover dark data and automatically find all the data that matters most to you, including PI, sensitive data, regulated data, financial data, and more. Combine RegEx with advanced ML and AI to scan your data 95% faster.
Will BigID integrate with my existing tech stack?
We strive to be an open and API-first platform that can easily integrate and orchestrate workflows with other enterprise infrastructure. Our partnerships include Collibra, Alation, SAP, Salesforce, ServiceNow, Confluence, Splunk, Snowflake, Microsoft, Google, AWS, and more. BigID also provides extensive APIs, documentation, and code samples to help organizations build custom integrations and orchestrations, so you can get the most out of your tech stack.
What uses cases can BigID solve for?
- Accelerate cloud migrations
- Validate mergers & acquisitions
- Manage insider risk
- Improve data security posture
- Enabling zero trust
- Staying compliant with global regulations
- Manage cross-border data transfers
- Minimize attack surfaces
- Revolutionize DLP with machine learning
- Automate end-to-end data lifecycle management
- Enrich your existing tech stack
- And more…!
ITAR Compliance: Rules & Exemptions for the International Traffic in Arms Regulations
If your organization deals in product, services, or information included in the United States Munitions List (USML), you are subjected to ITAR complaince. Download the guide to get everything you need to know on the ITAR, understand the rules and exemptions, comply with the regulation, and secure your data.
