Bring Your Data Privacy, Security, & Governance Programs into PDPL Compliance
Automate compliance with the new Personal Data Protection Law (PDPL) required by the Kingdom of Saudi Arabia (KSA) by following the data management framework established by The National Data Management Office (NDMO) with BigID. See how you can find and map sensitive data, manage data rights requests, assess risk, and take action to improve your data risk management and better protect your data.
Talk to one of our data-centric NDMO specialists 👇 and check out what we put together for you below.
Recognized as the #1 industry-leading data security, privacy, compliance, and AI solution



-1.png?width=152&height=193&name=image%20(23)-1.png)

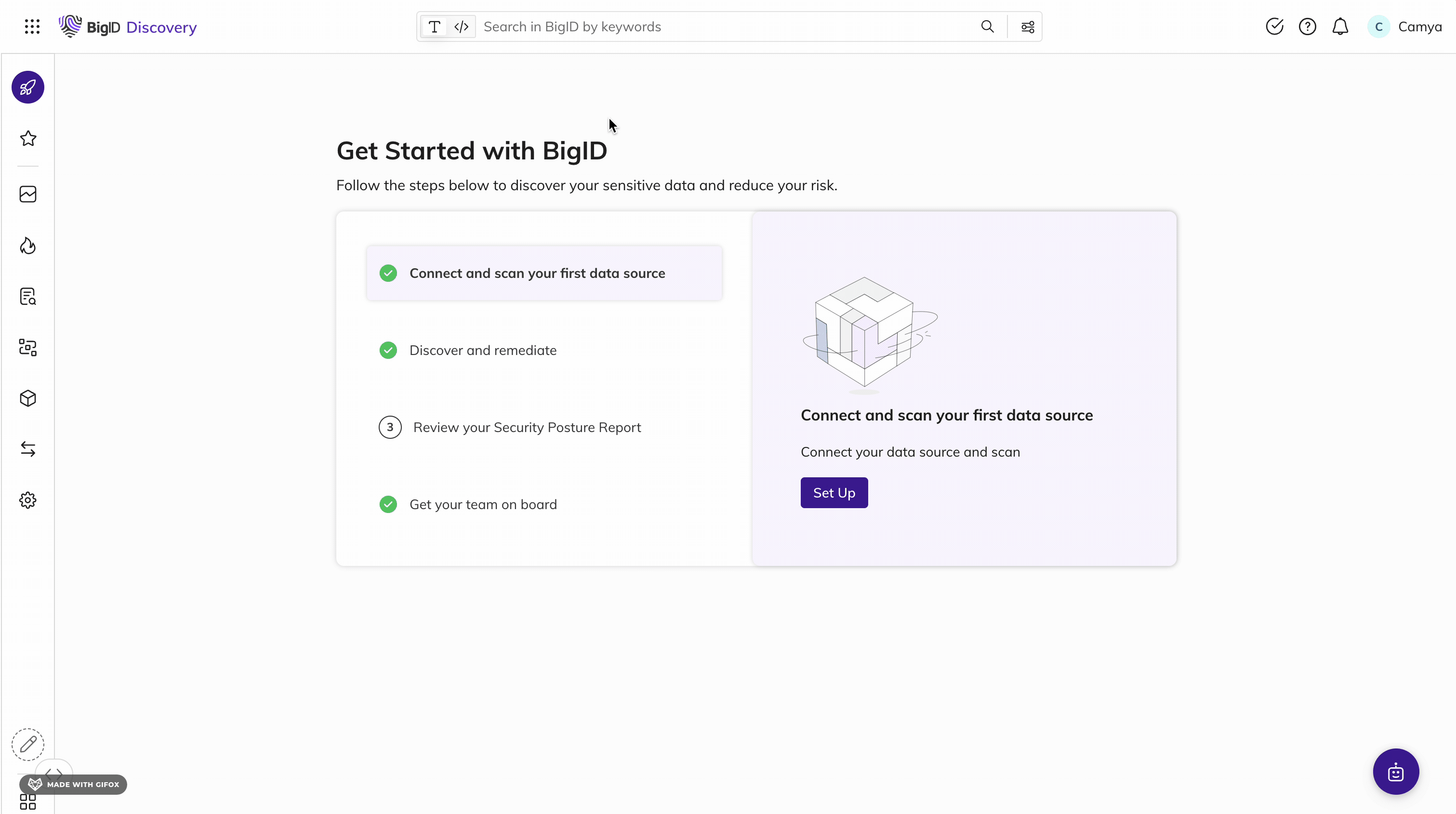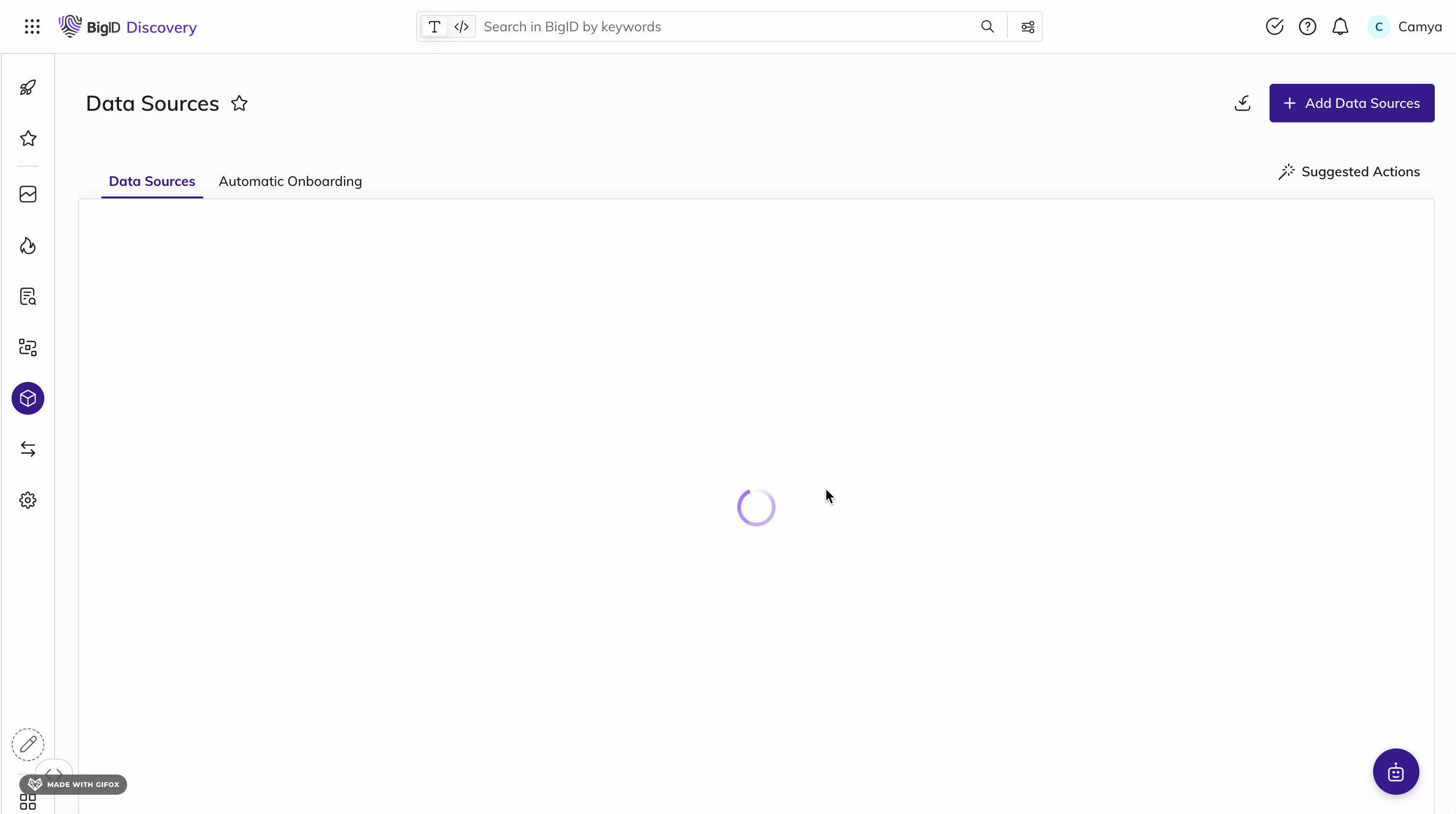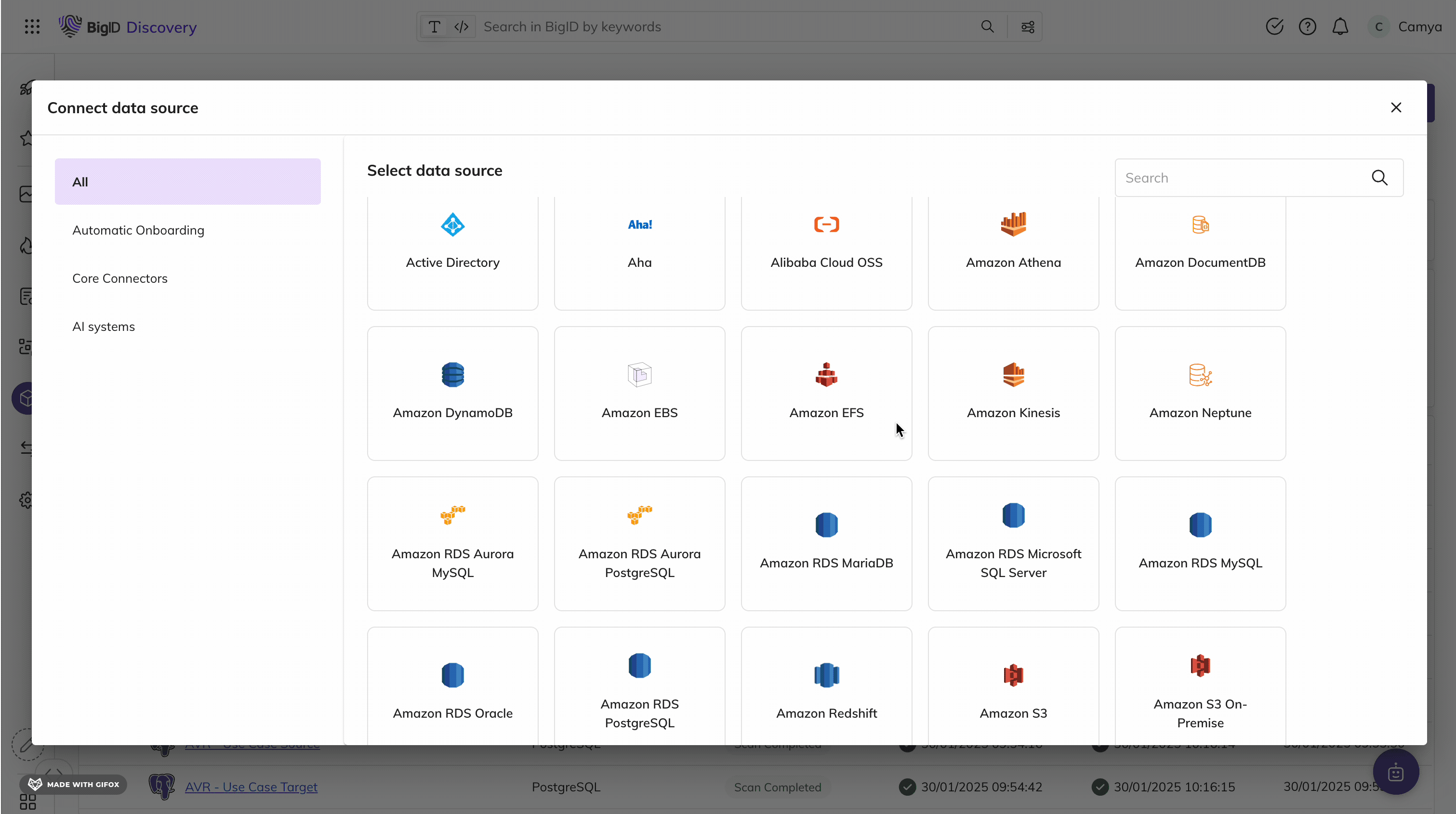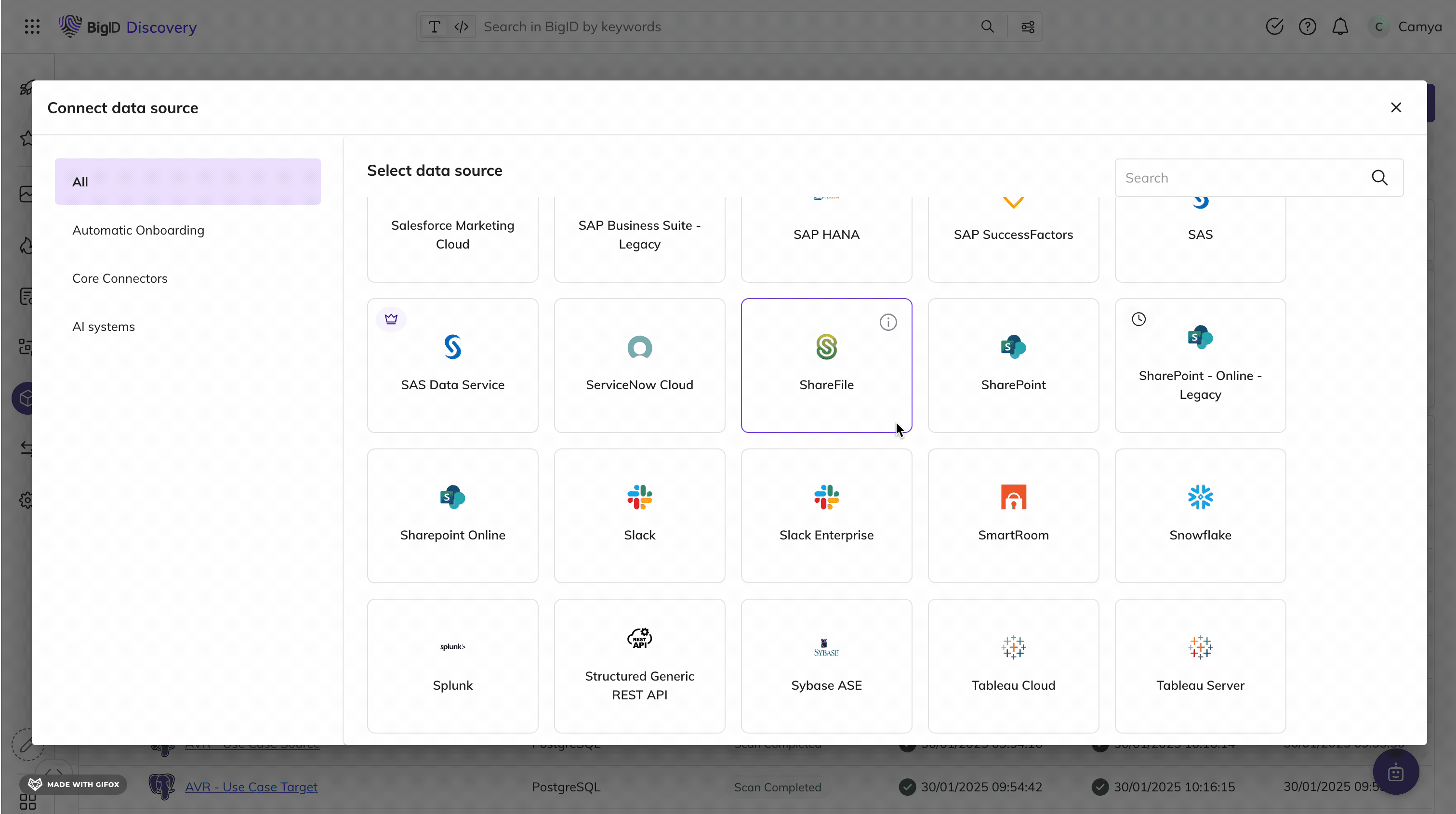
Navigating the NDMO Framework
Follow the roadmap to data compliance in Saudi Arabia
The NDMO is the regulatory authority responsible for data governance in the Kingdom of Saudi Arabia (KSA). NDMO enforces the PDPL, the first-ever comprehensive data protection law in the KSA. It aims to regulate the collection, processing, storage, and transfer of personal data by public and private organizations in the KSA. This framework spans the data lifecycle from creation, storage, movement, usage, and disposal.
BigID is uniquely positioned to enable organizations to comply with PDPL. With BigID, organizations can find, classify, and map all sensitive data to the KSA, automate data rights requests and risk assessments, and reduce risk with data retention policies and data breach management.

5 Reasons Why You Should Choose BigID for PDPL
Coverage
Find sensitive data that matters most to the KSA and PDPL, wherever it lives. Support for 100’s of data sources and types - unstructured or structured, on-prem or across the cloud. Accelerate insights and eliminate blind spots with Auto-Discovery.
Classification
Combines regular expression (RegEx) with advanced, AI and ML-based techniques to classify all KSA data types, more accurately, at scale. Deploy hundreds of OOB classifiers. Build your tailored composite classifiers. Train your own NLP and deep learning classification models.
Automation
Find more KSA PI and PII with greater accuracy using machine learning. Automatically map all of your data and fulfill data rights management requests end-to-end, including data deletion. Orchestrate remediation and retention workflows to enforce policies around sensitive KSA data.
Reporting
Conduct privacy impact assessments and record of processing activities to map sensitive KSA data by individual and assess risk. Access pre-built and customizable dashboards, reports, and executive summaries for privacy, data mapping, and security.
Scale
Grow with the ever-evolving privacy landscape in the KSA with advanced capabilities like cross-border transfers. Go beyond Privacy and extend into Security and Governance to reduce risk and stay compliant with PDPL.
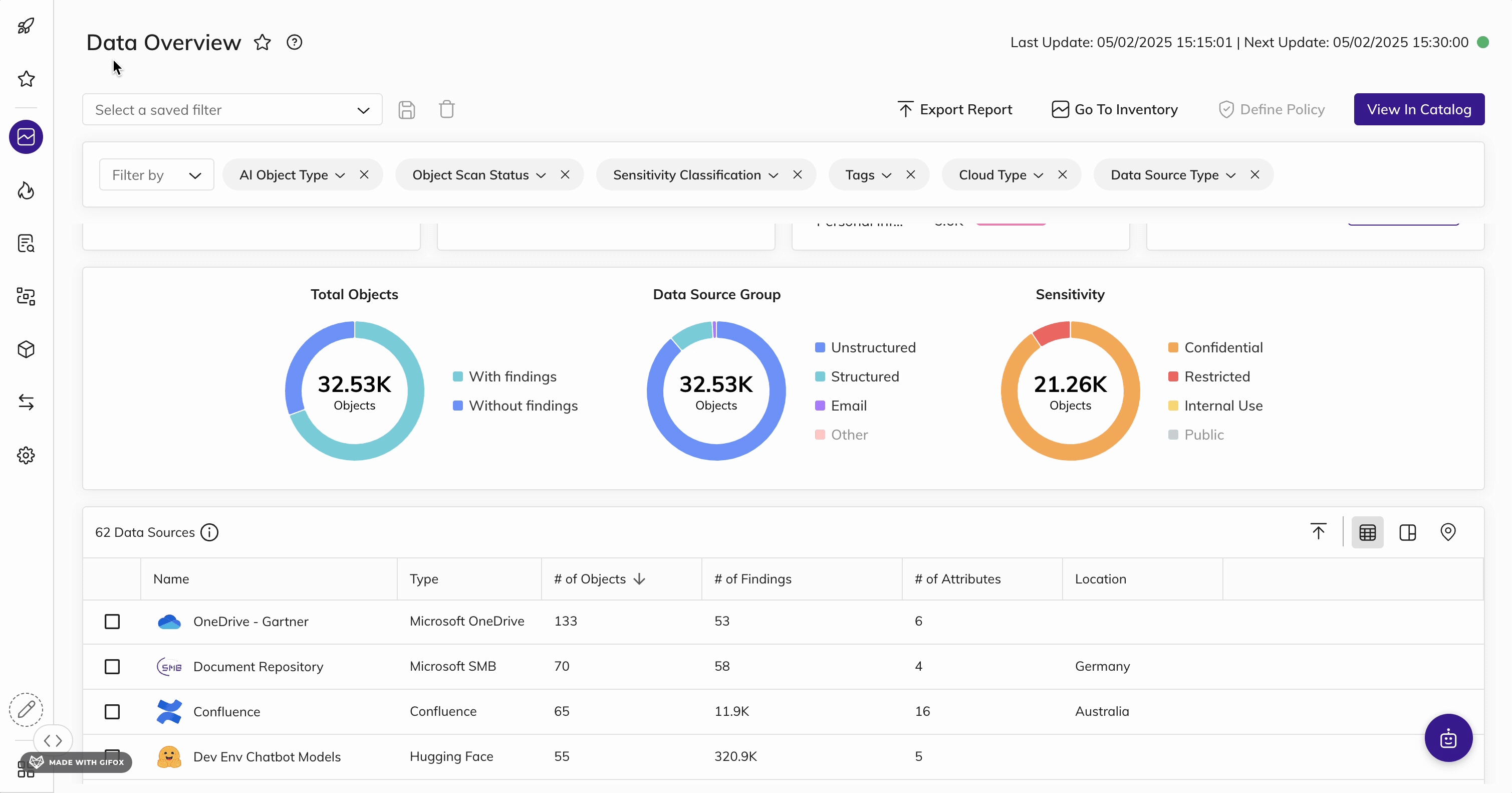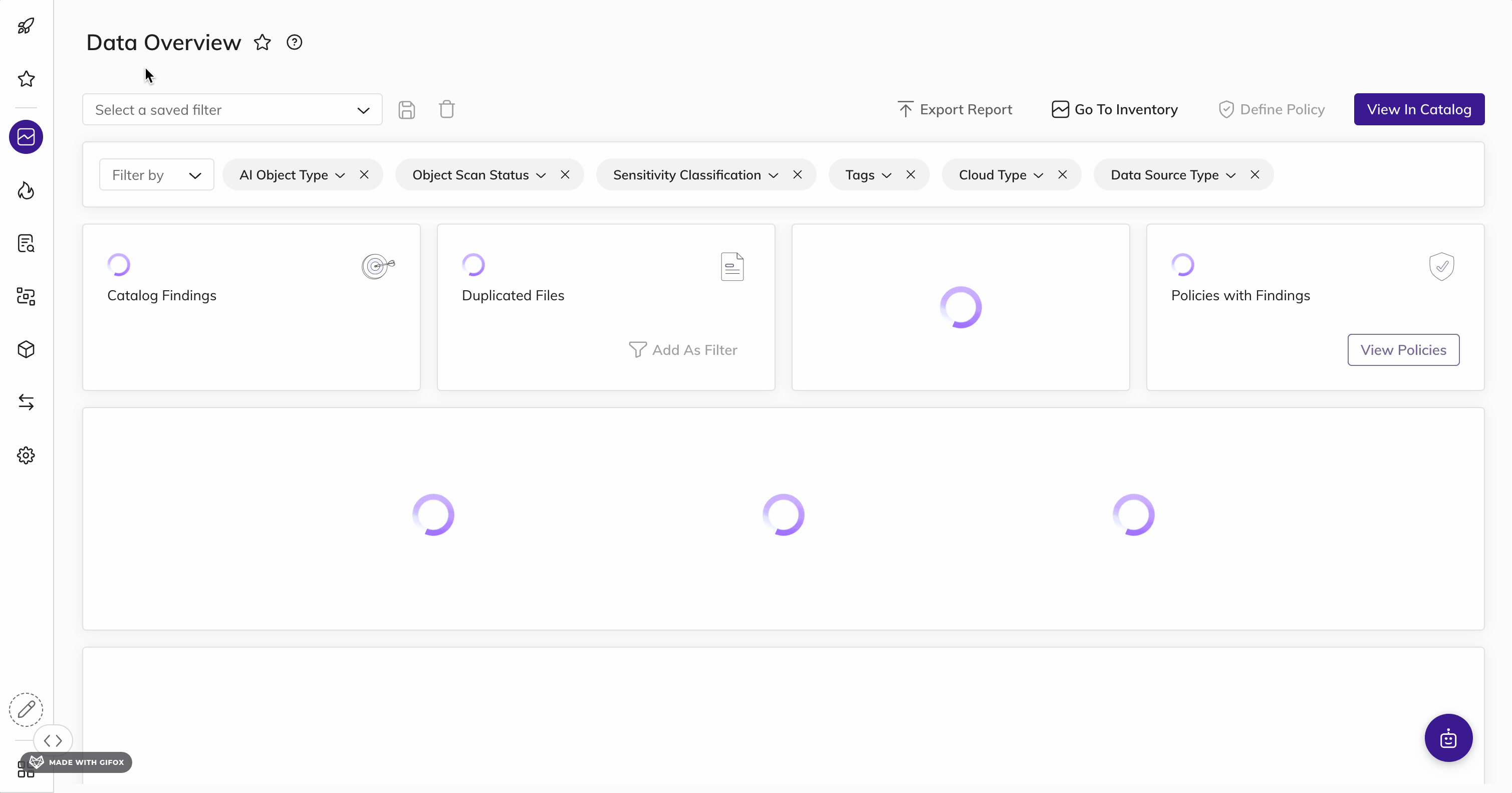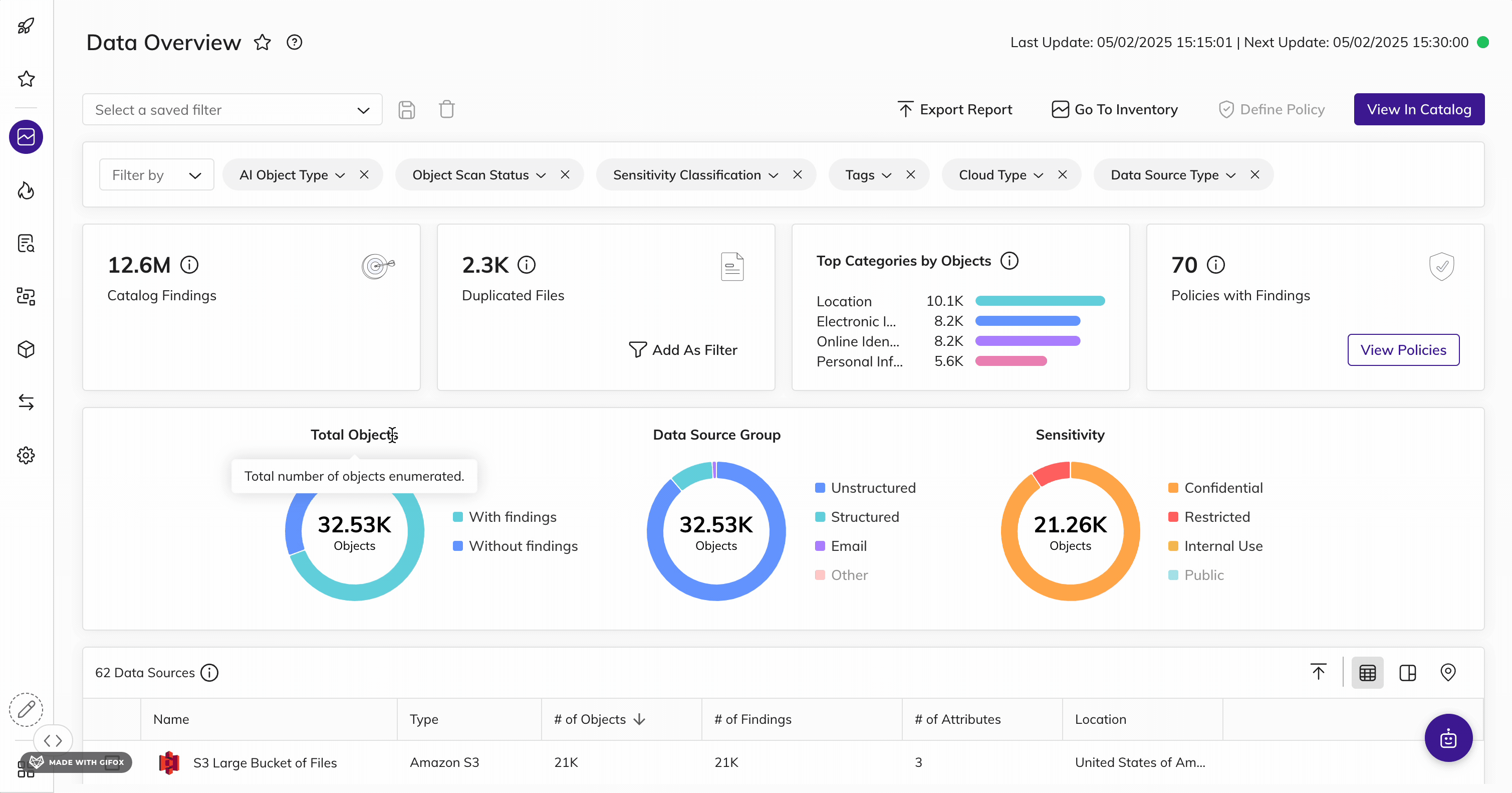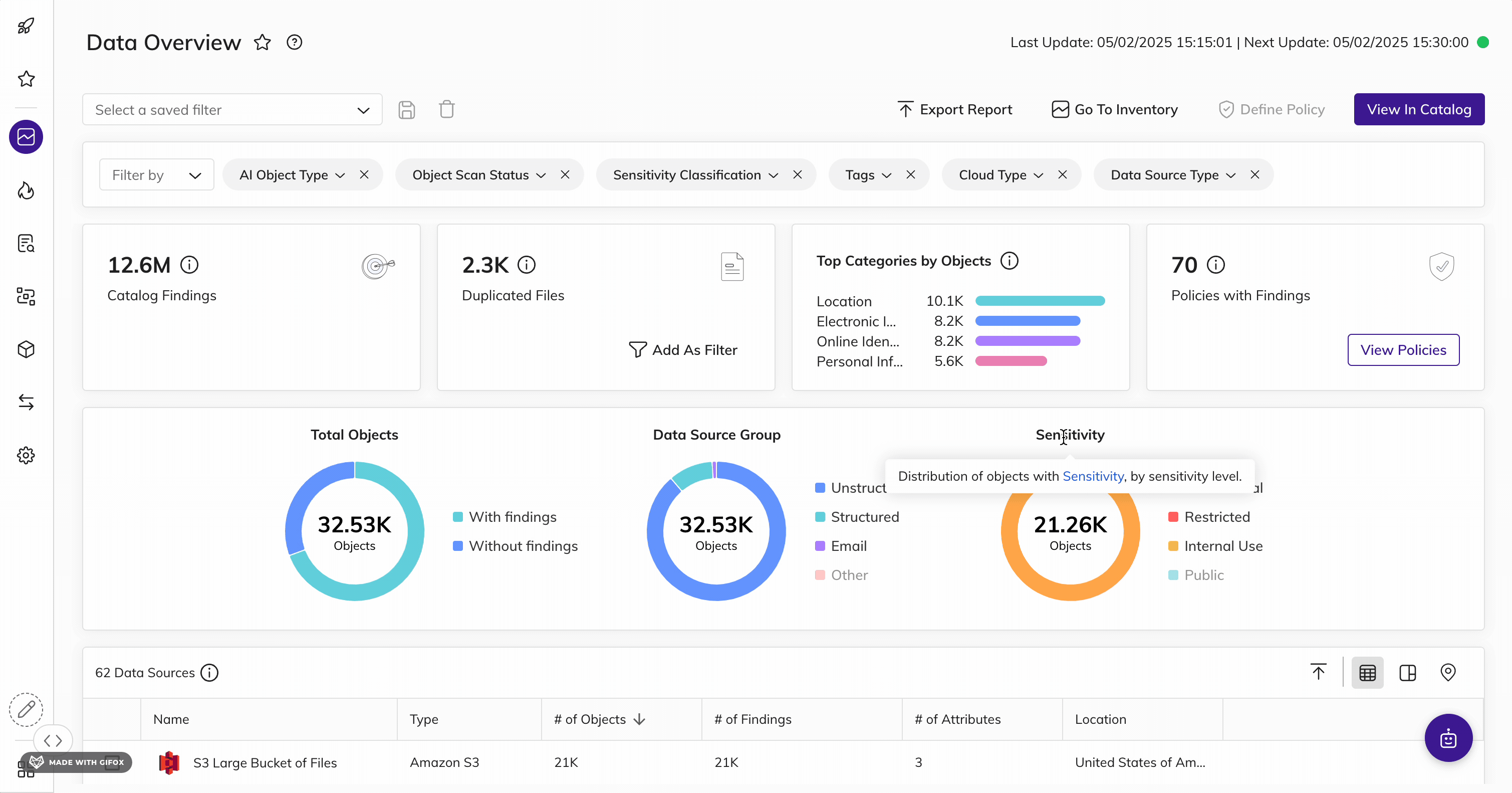
Shine a Light on KSA Data
Automatically find and inventory your most sensitive, critical, and high-priority KSA data - wherever it lives.
BigID helps organizations meet PDPL requirements set by the NDMO framework with unmatched data discovery and classification to find the data that matters most to the KSA.
Get advanced data discovery and classification to find KSA resident and household data: whether it's critical, regulated, personal, secrets, passwords, IP, financial, or more. Get more accurate results every time with ML-driven data classification - across your entire data landscape (from on-prem to cloud to everywhere in between) for structured and unstructured data.
Automate Data Rights Requests for KSA Consumers
Automate KSA data rights fulfillment from access to deletion
Dynamically manage Data Subject Access Request (DSAR) at scale by discovering, classifying, and connecting KSA data to specific user profiles to automate data subject access requests, validate data deletion, and generate DSAR pdf reports. Give customers the right to choose what they do with their data and comply with PDPL.
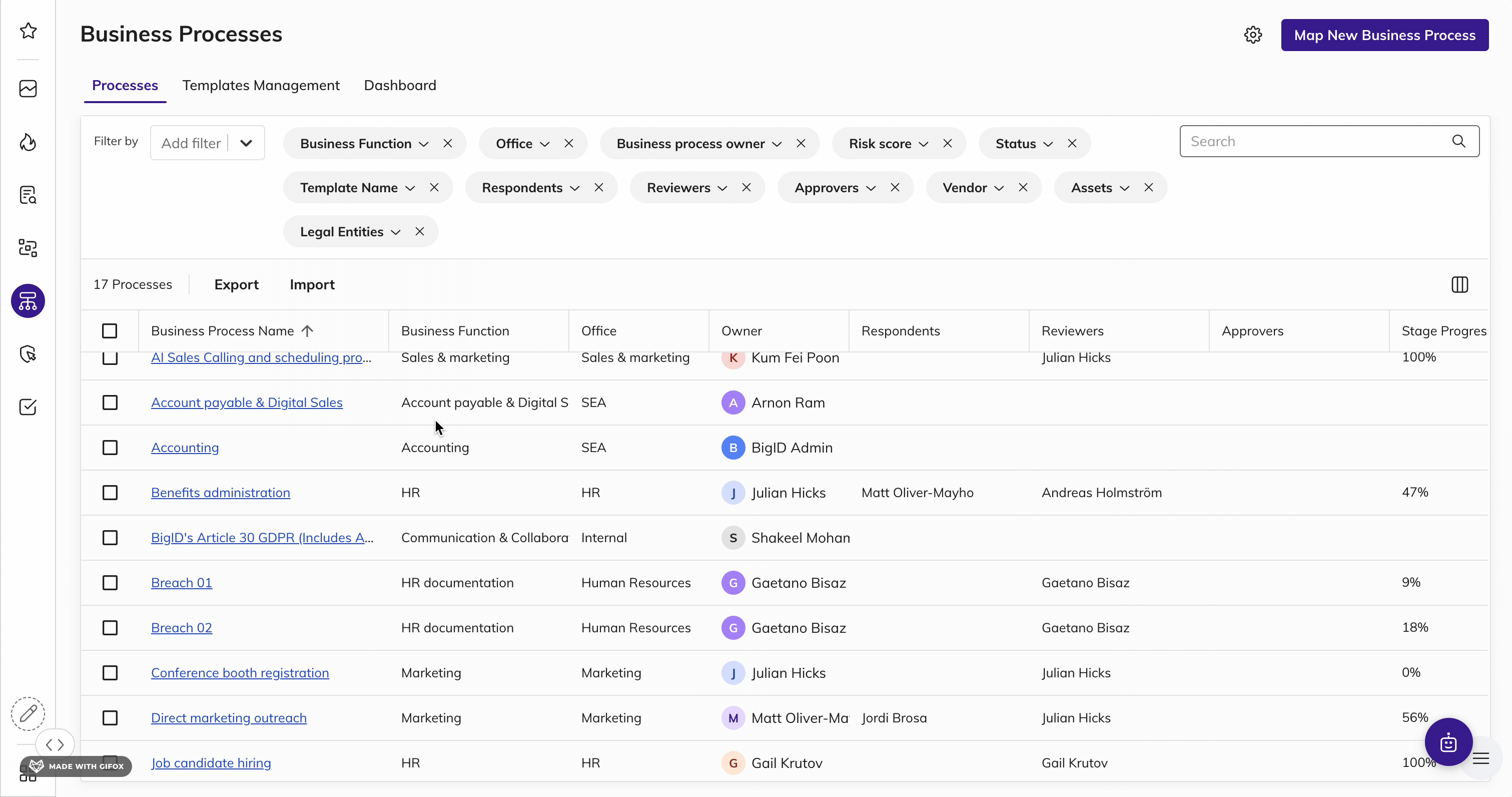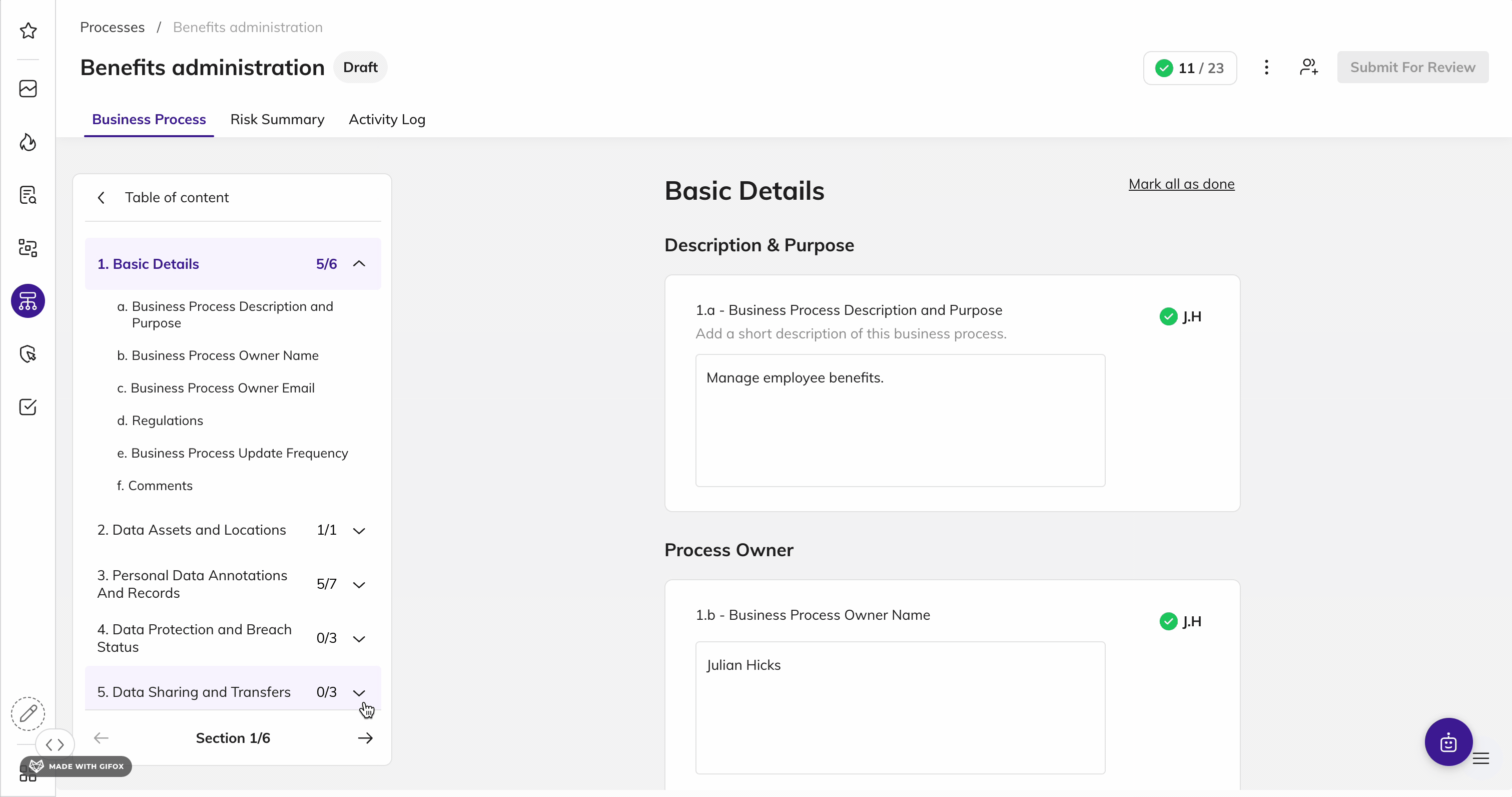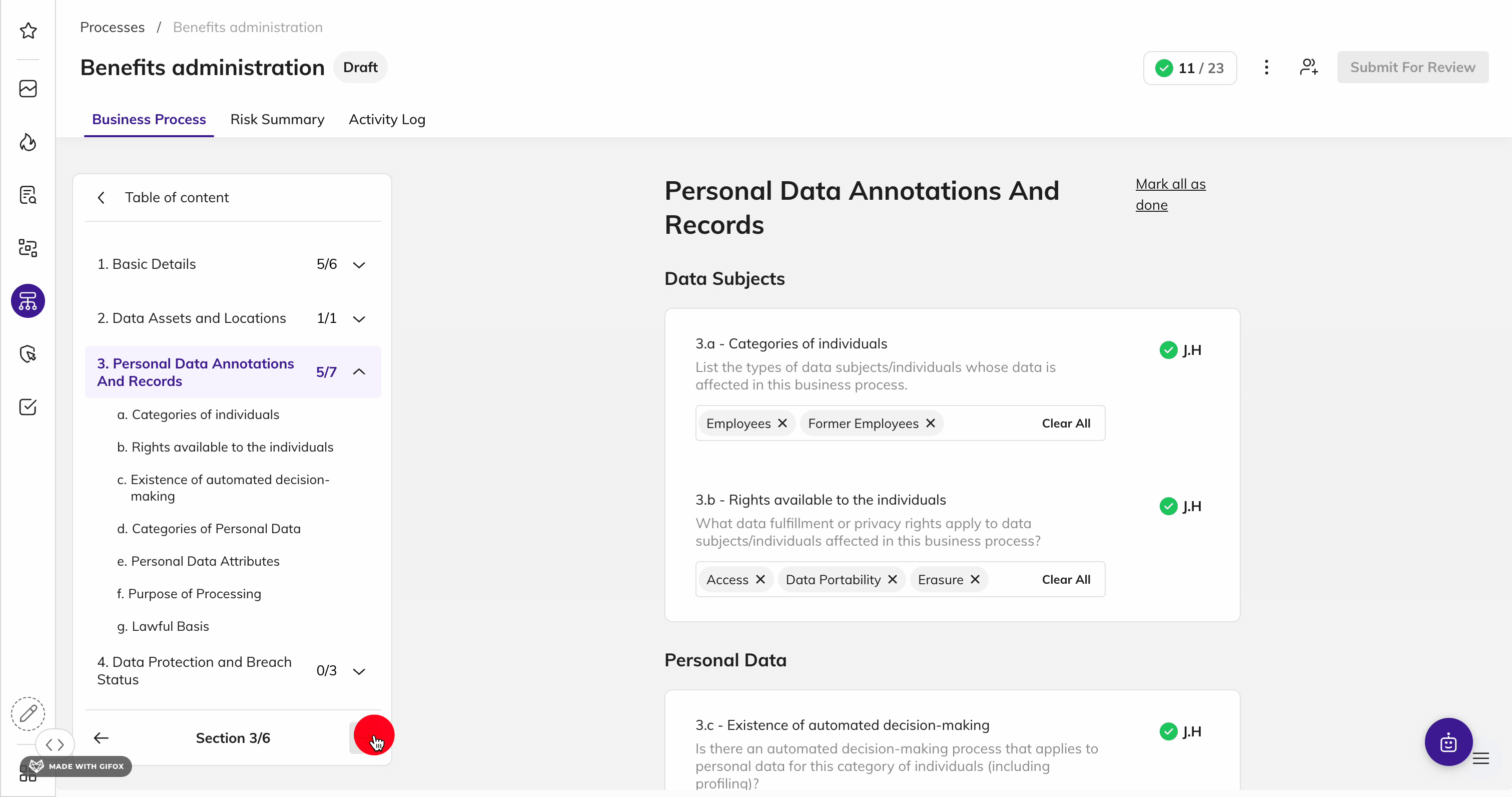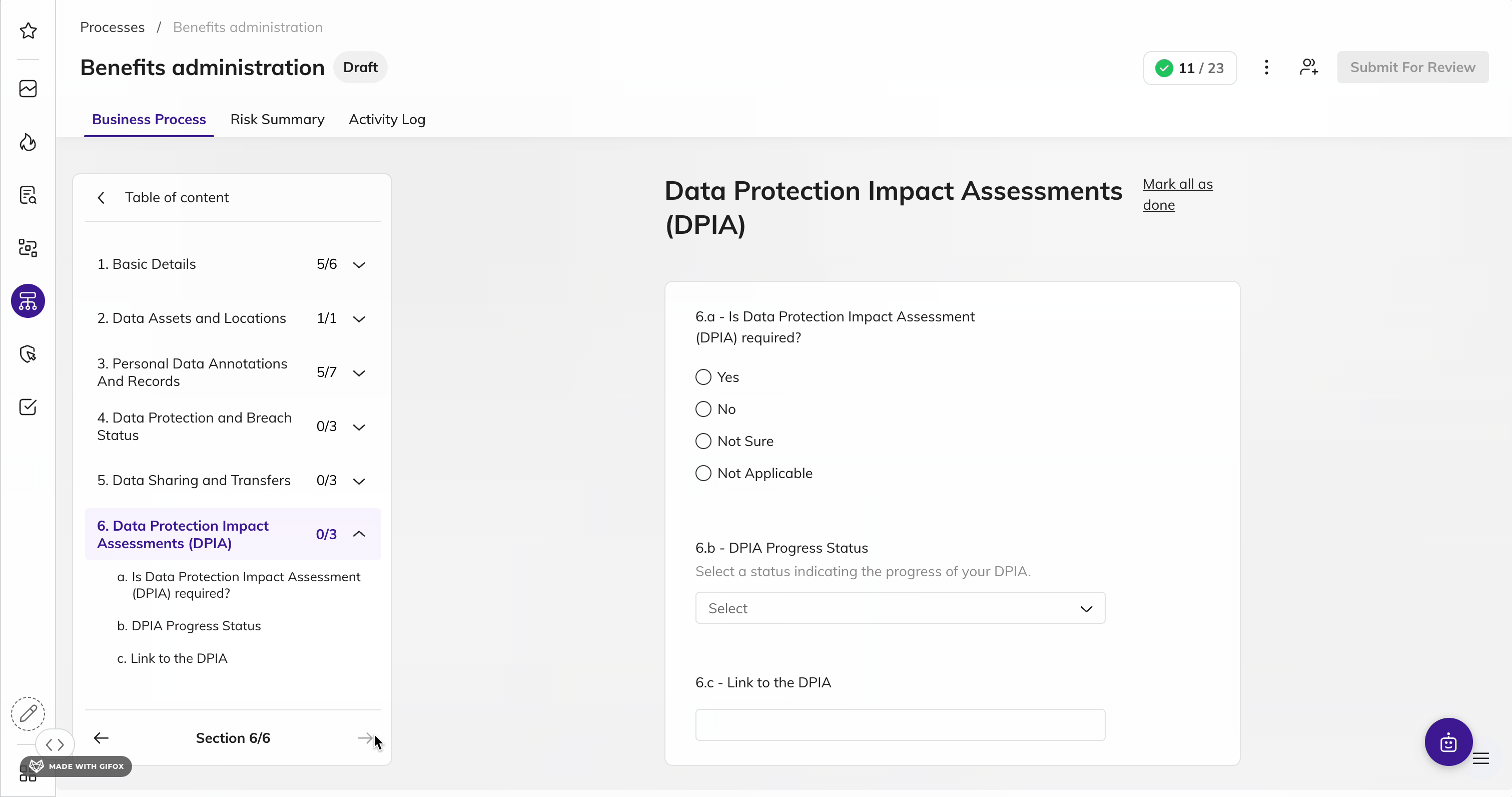
Map & Inventory Data by KSA Individual
Build a Record of Processing Activities (RoPa) for Data Mapping
Identify and document data inventory to visually map data across the organization to assess how data is processed, transferred, and shared to reduce risk.
Discover all personal and sensitive KSA information by identity, map the data relationships across sources, and visualize how data flows across your organization. Maintain an up-to-date and current documentation of how KSA consumer data flows to comply with the NDMO framework.
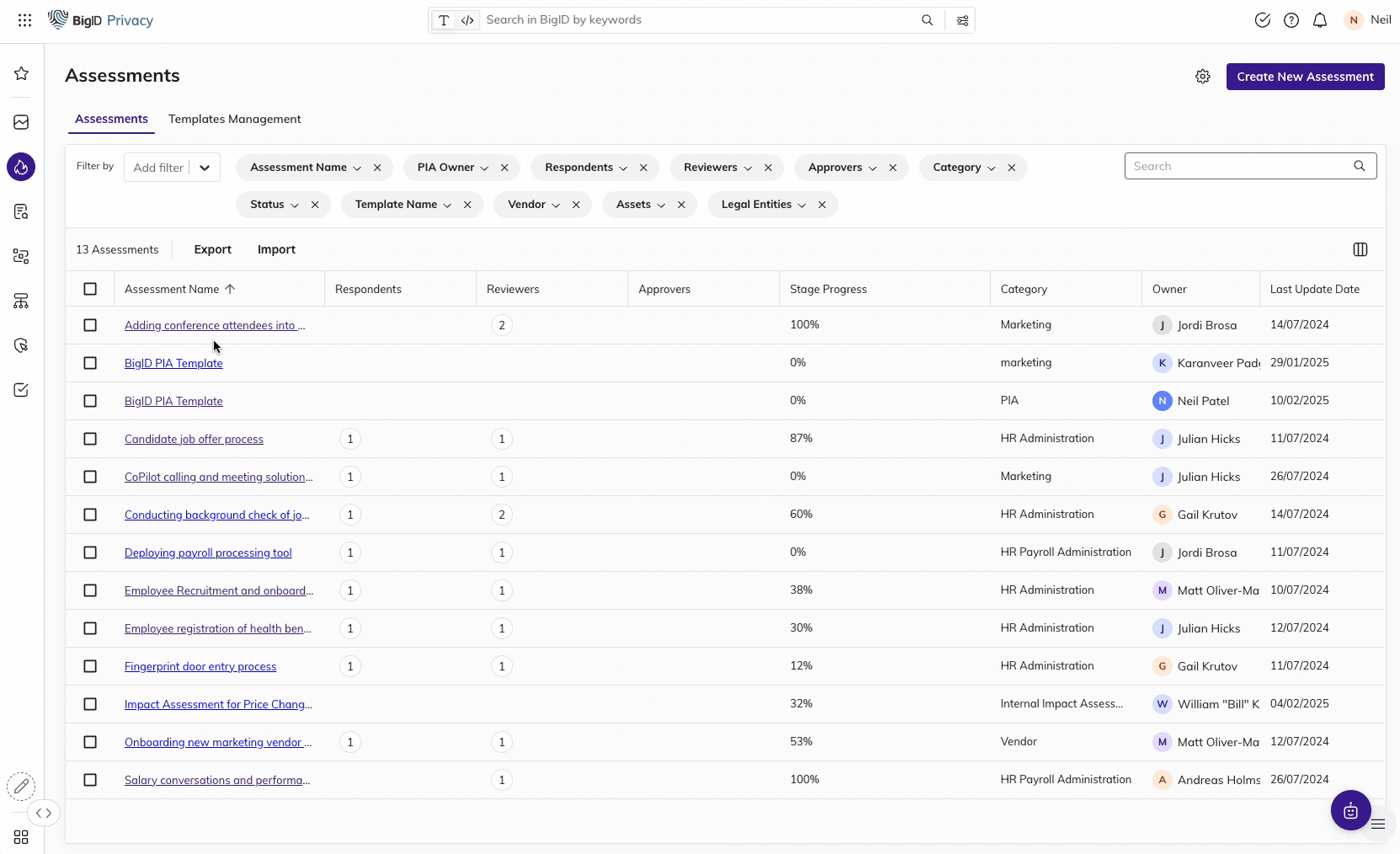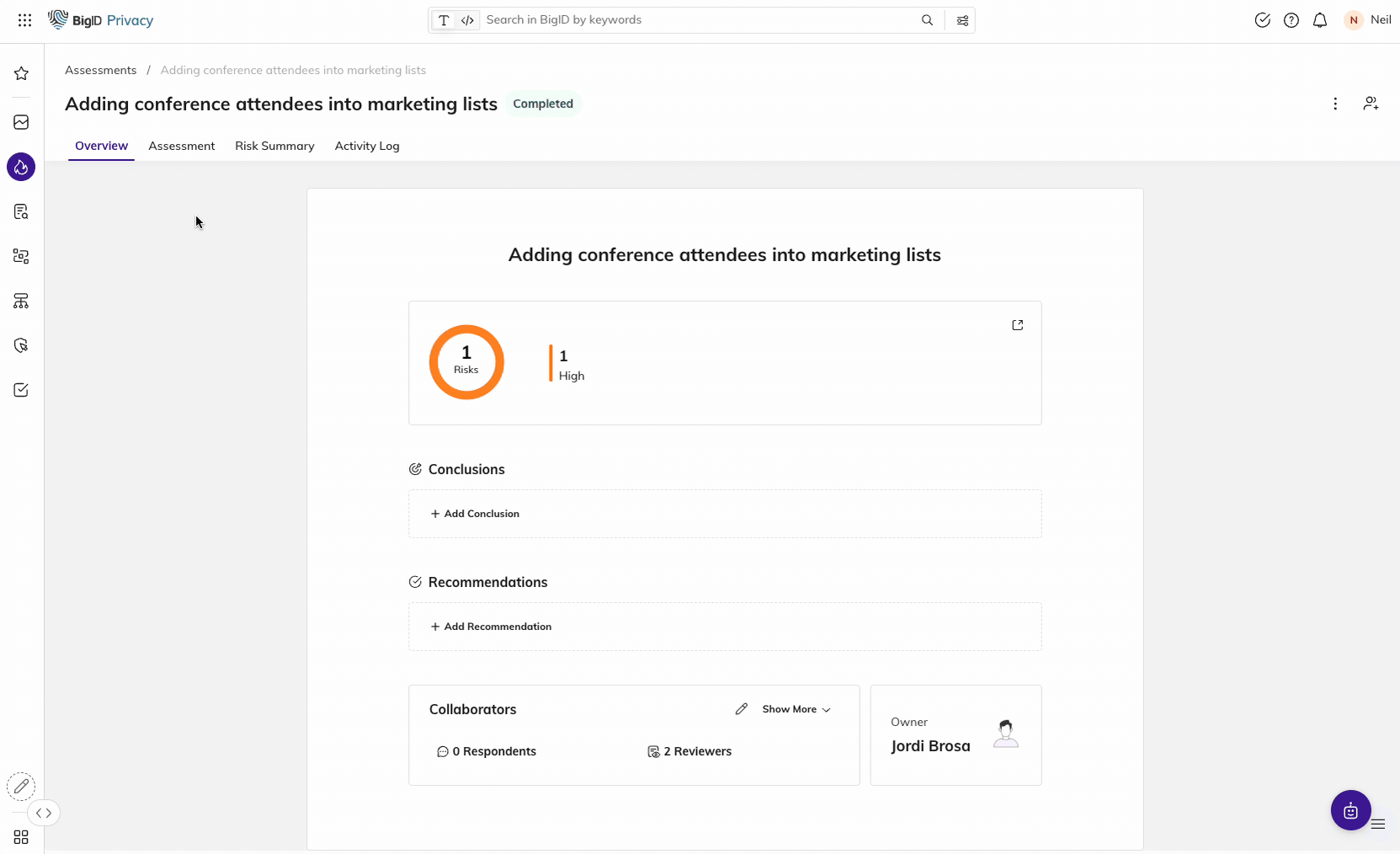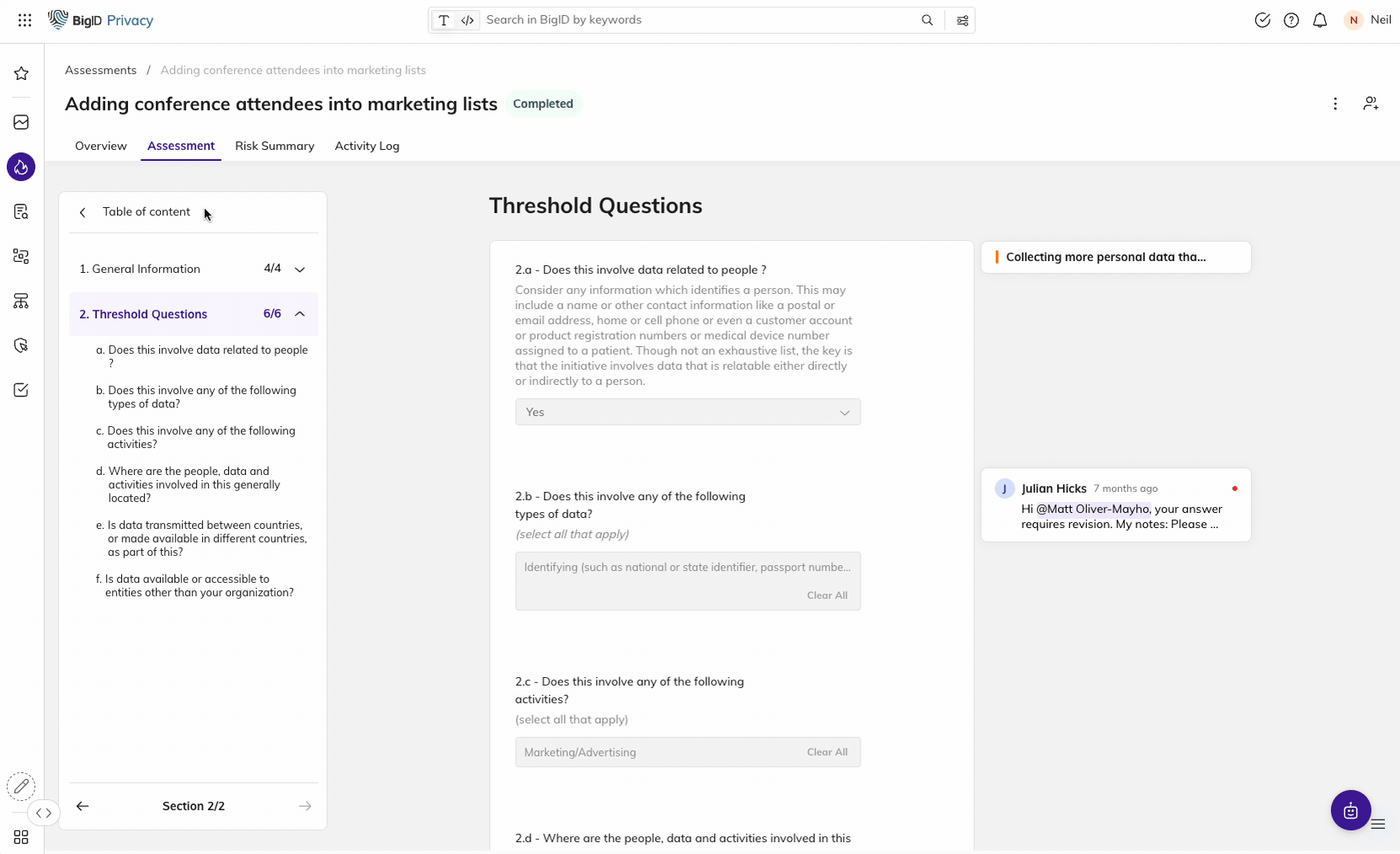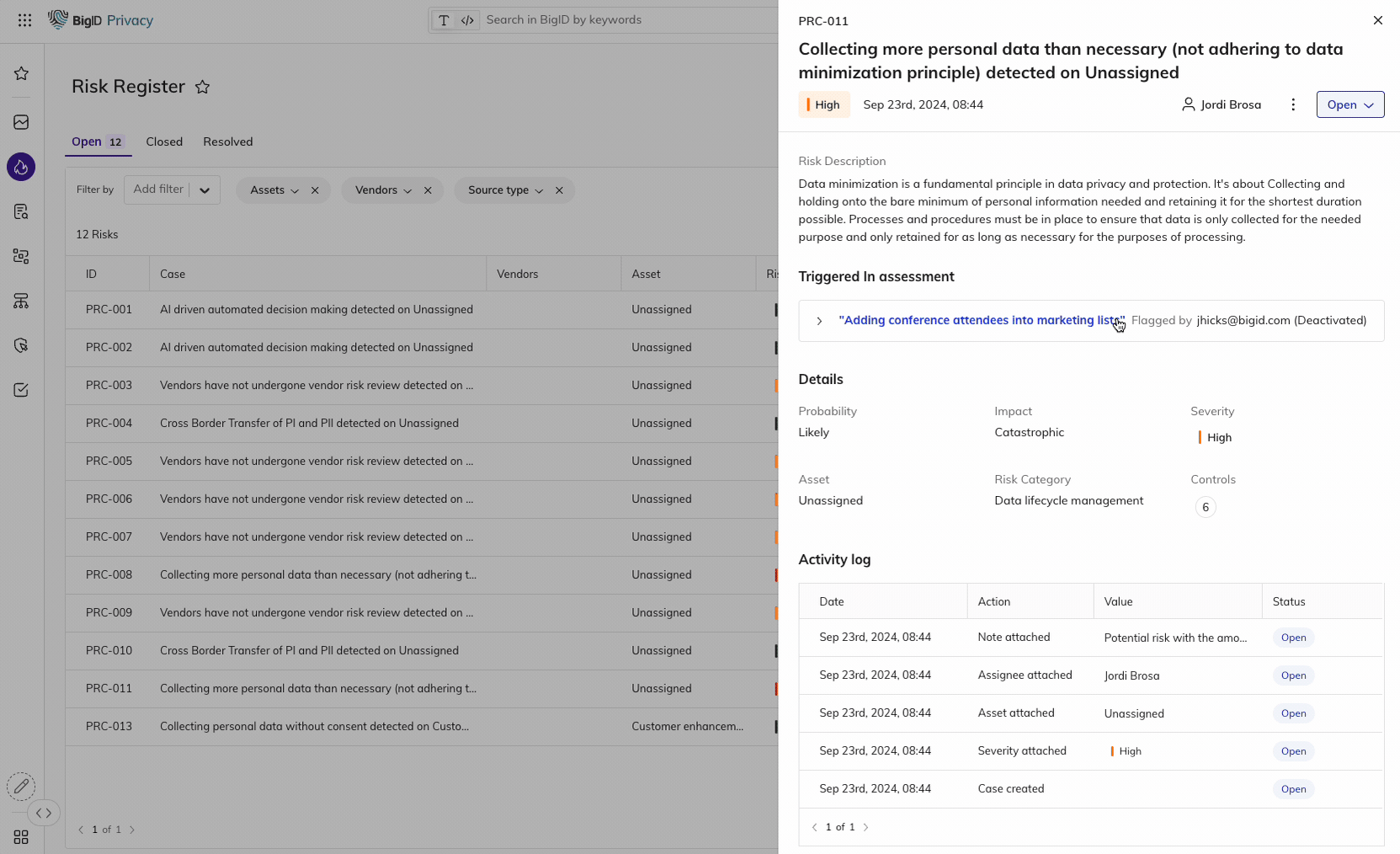
Conduct Privacy Impact Assessments for the NDMO
Quickly assess the risk associated with your data processing activities
Manage privacy risk assessments in a centralized location to estimate the risk associated with data inventory (owner, purpose, stored, used, shared, and maintained) and comply with privacy protection regulations like PDPL.
Establish a systemized process with industry-standard templates to streamline collaboration with data owners. Eliminate the manual process of documenting PIAs with automated end-to-end fulfillment.
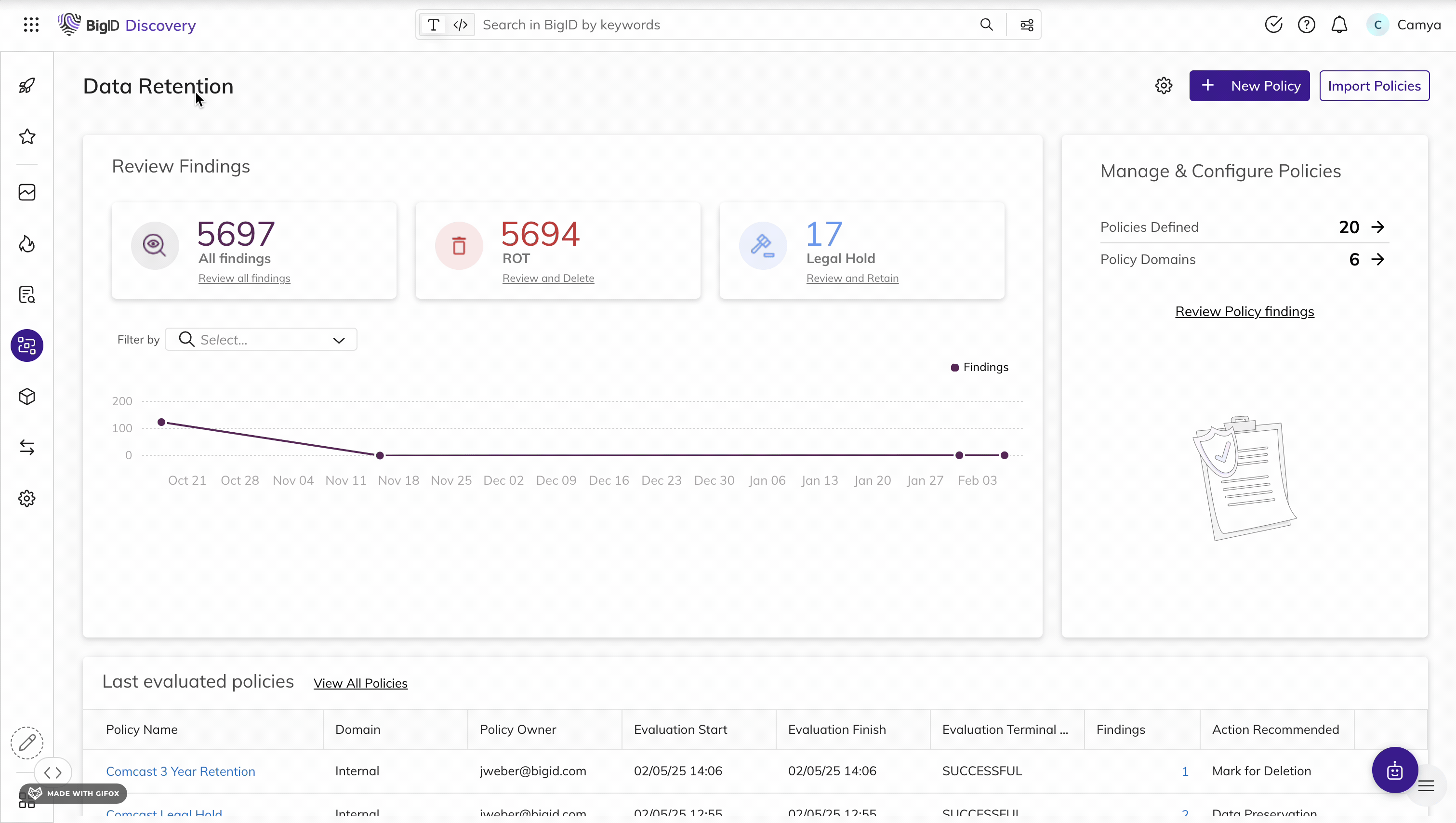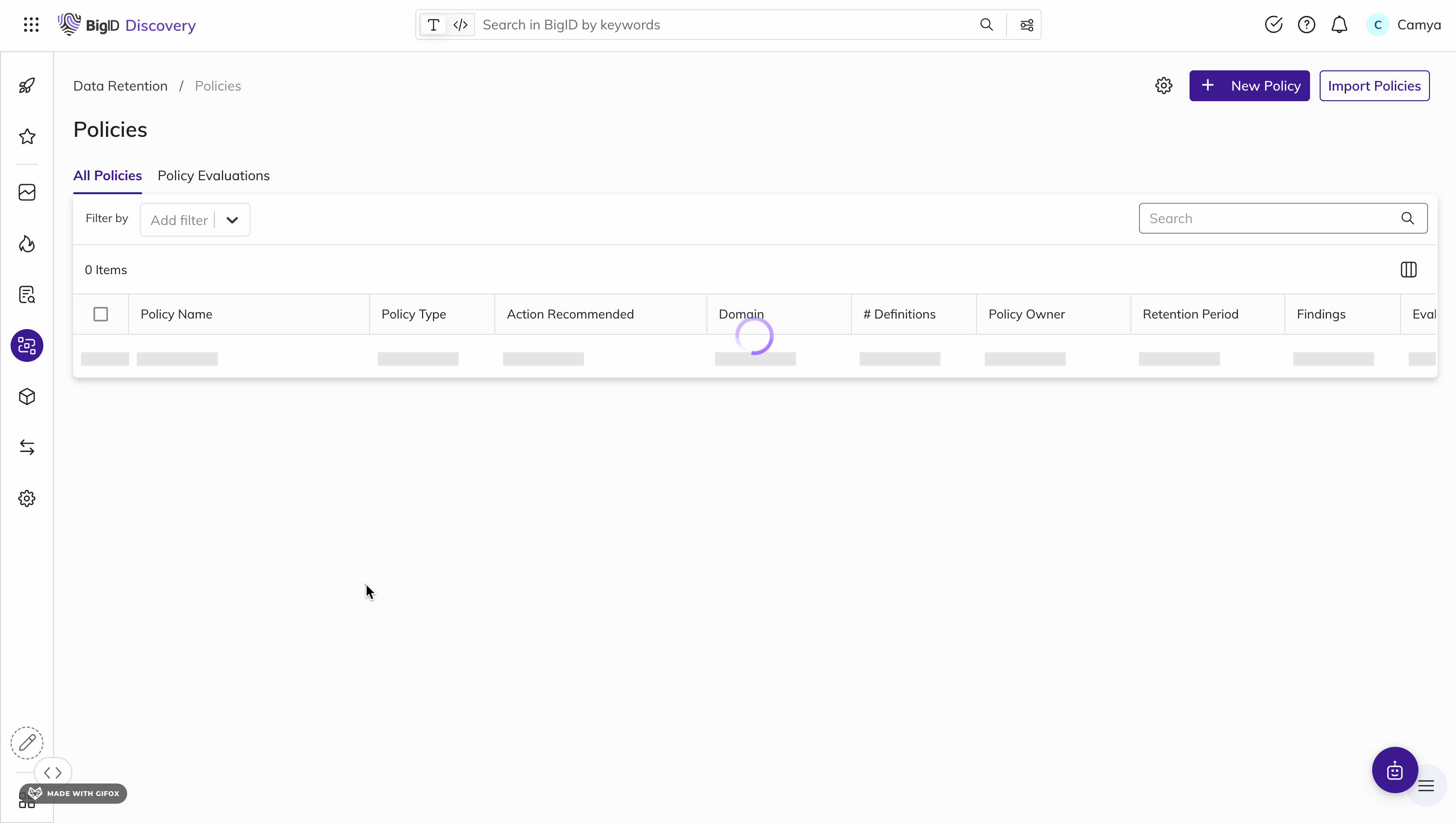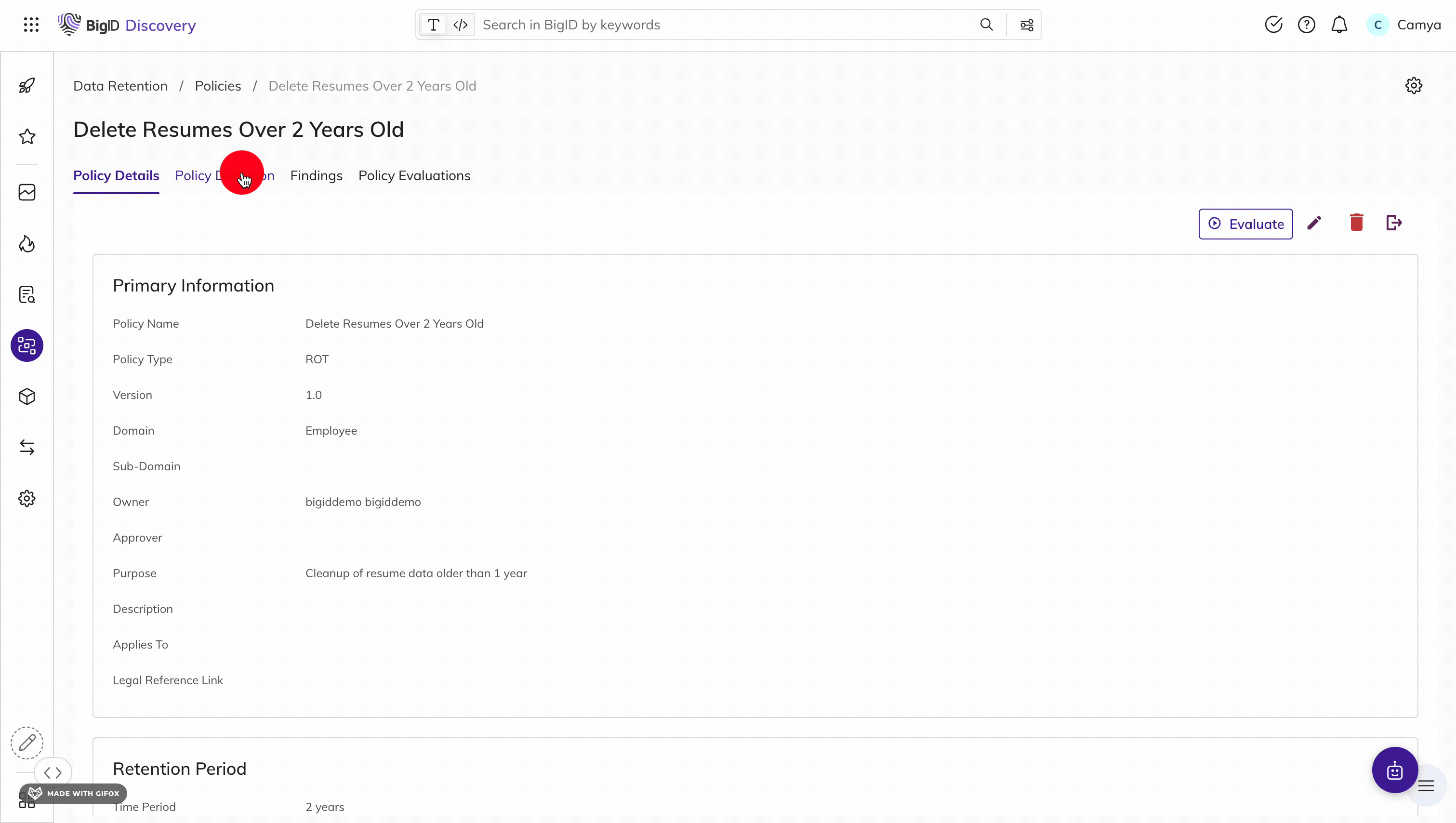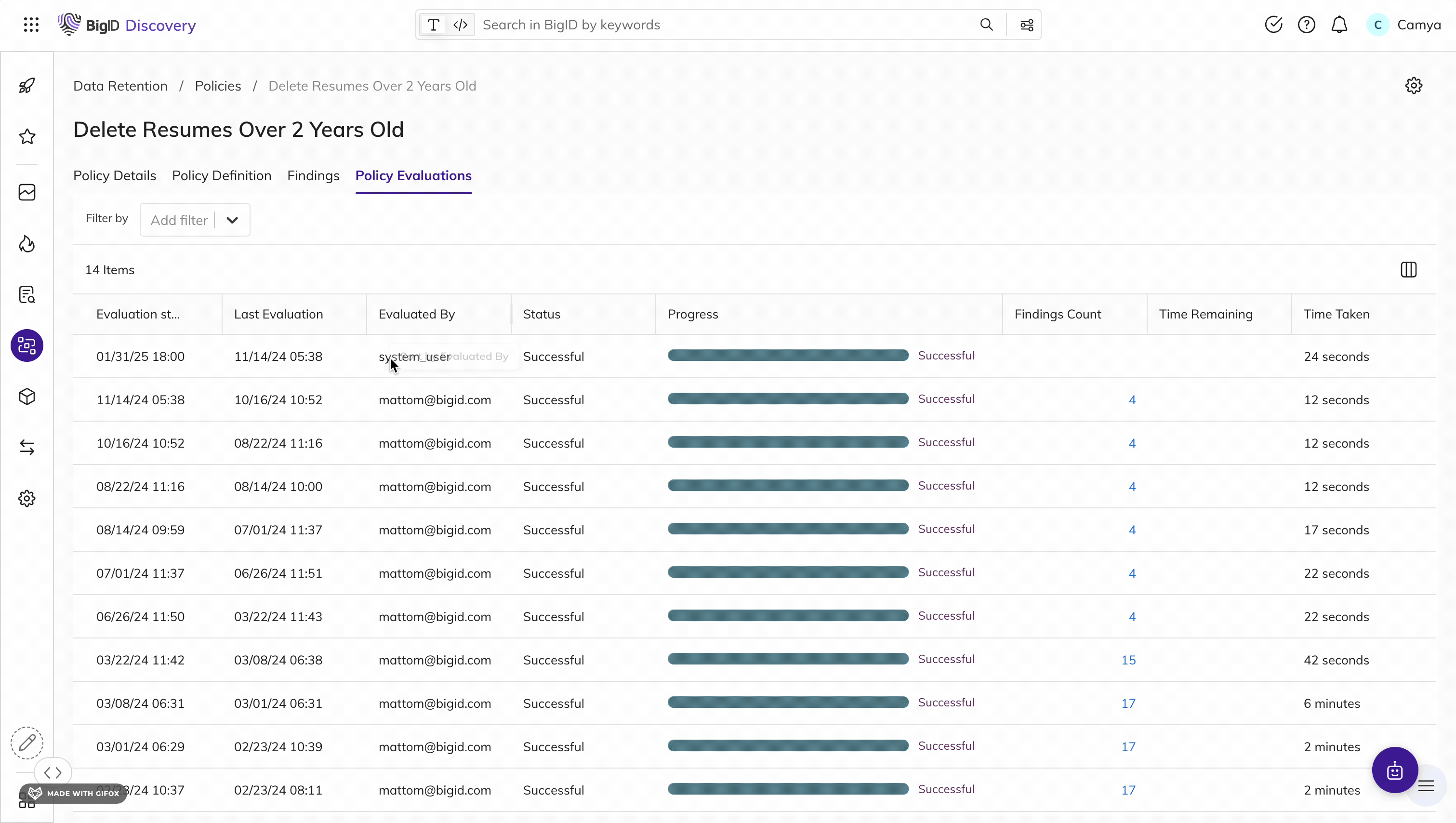
Enforce retention policies and remediation workflows for PDPL
Automate and validate end-to-end data management at scale
Enforce policies around sensitive KSA data and kick off remediation workflows with the Data Remediation App. Use the RoPA Data Mapping App to map sensitive and regulated data processing and sharing to assess the risk profile for a business process. Use the Data Retention App to detect data retention violations and carry out remediation wherever sensitive data exists. Identify and clean up duplicate and ROT data to minimize attack surfaces.
Enable Zero Trust for KSA Data
Restrict access to system components and sensitive data by business need to know
Reduce risk by managing access to sensitive and critical KSA consumer data. Easily find over-permissioned and over-exposed data across your entire data landscape: mitigate unauthorized use, reduce the risk of data leaks or breaches, and get to a least privileged permissions model for zero trust.
Use the Access Intelligence App and ML-based insight to identify, flag, investigate, and prioritize overexposed data – then revoke access rights from groups to reduce the risk of data leakage and comply with PDPL.
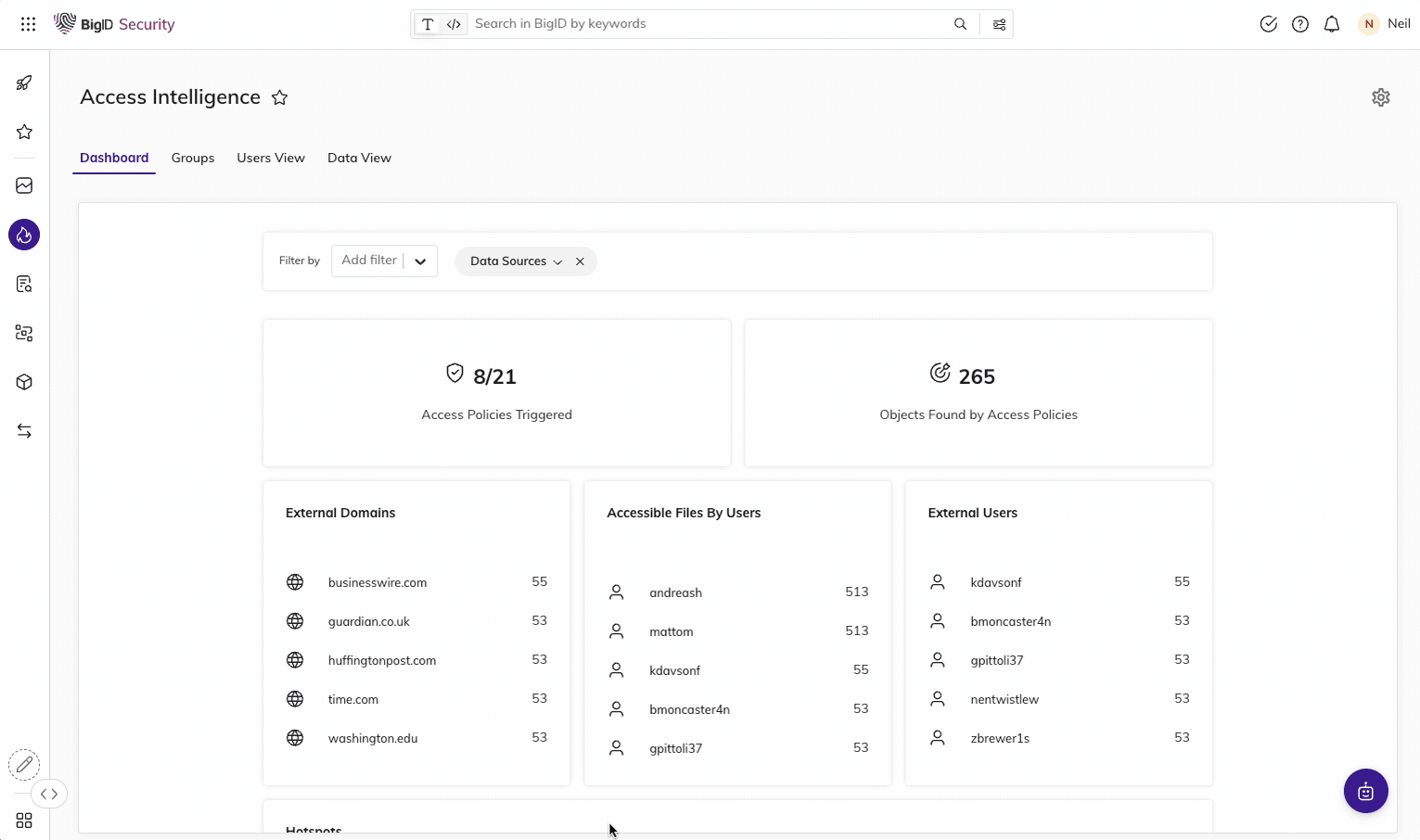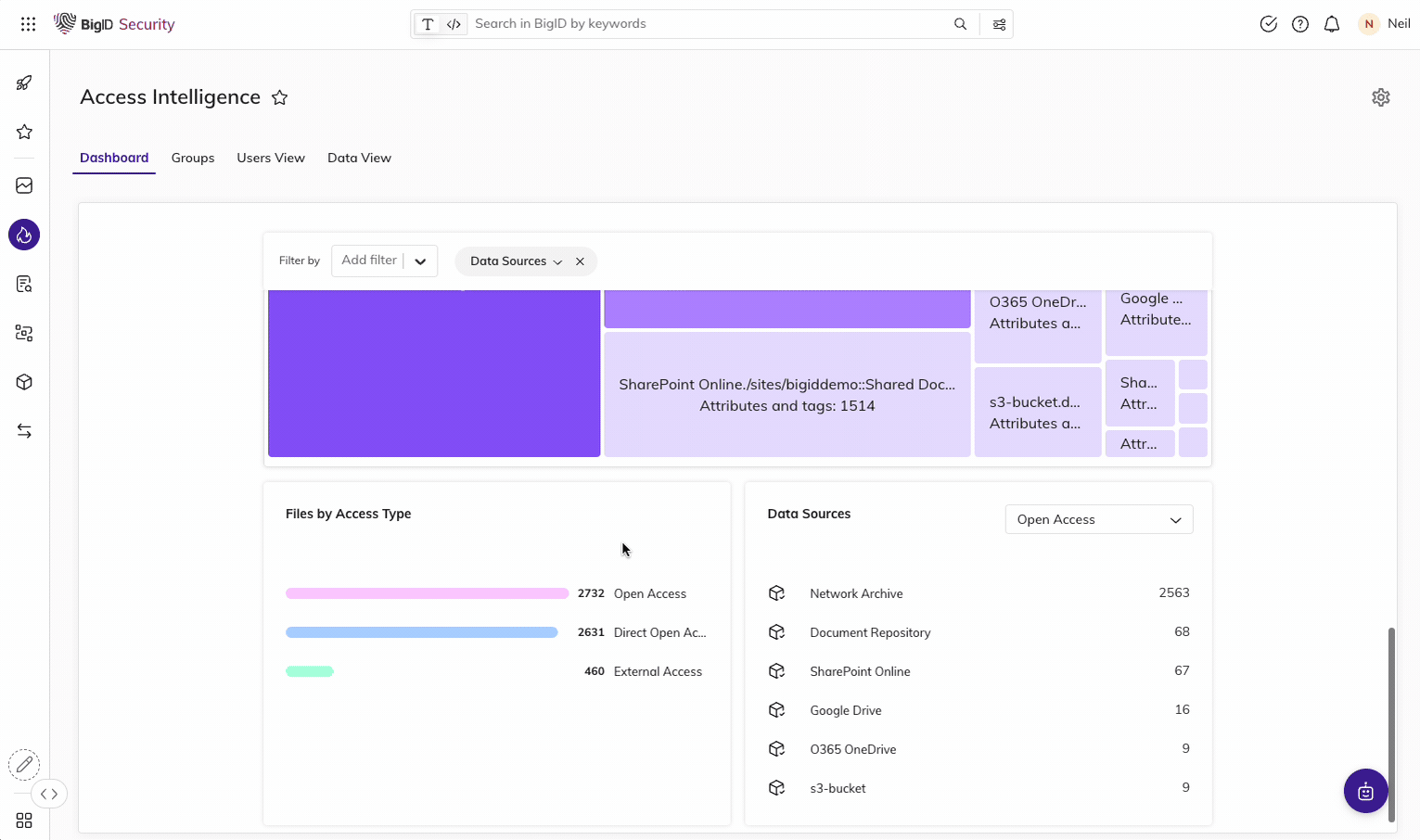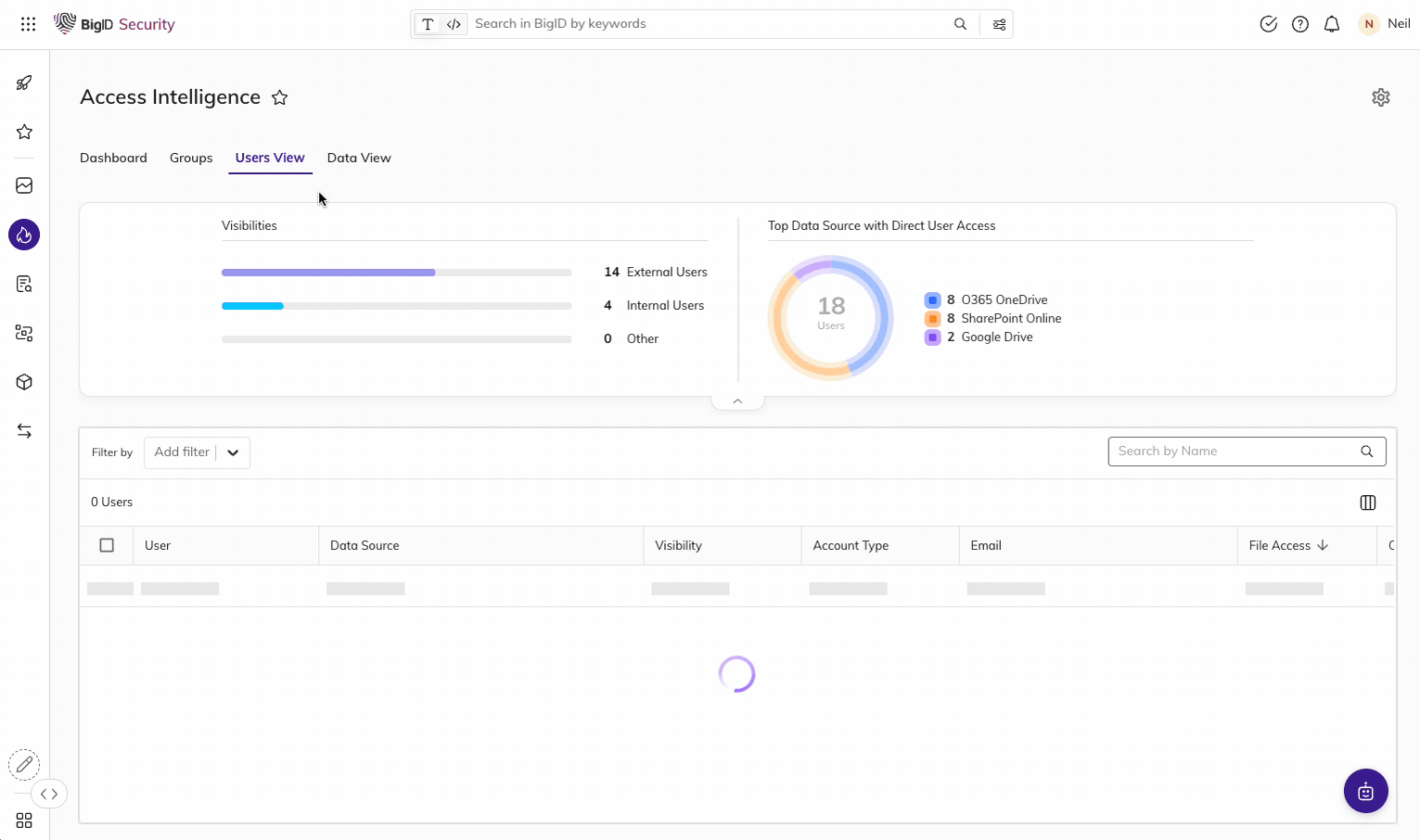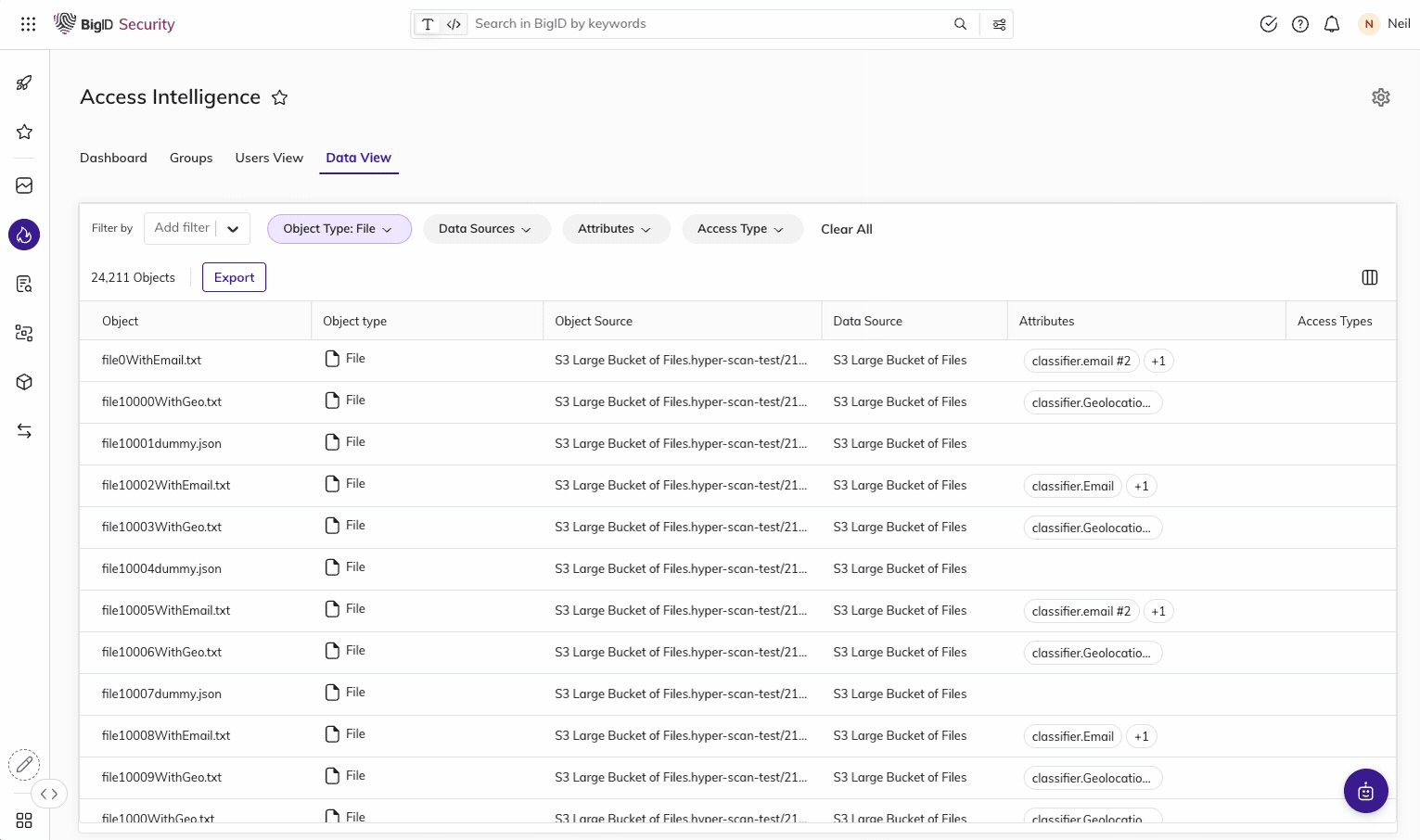

Simplify Breach Incident Response for PDPL
Determine breach impact & streamline incident response
Assess the scope of a breach, identify impacted users and determine appropriate response plans. Determine whose data and attributes are impacted by a breach and systems and applications that have accessed the breached data source.
Comply with PDPL breach reporting requirements to minimize financial, legal, and brand impact through automated workflows to facilitate response and notification.
Navigating the NDMO Framework for PDPL Compliance
BigID enables enterprises to establish core competencies to meet National Data Management Office (NDMO) framework requirements by allowing privacy, security, and data governance teams to inventory, account and report on how they collect and process personal information.
Read the whitepaper to learn how the BigID platform aligns with the 15 Domains of the NDMO framework about data lifecycle management from creation, storage, movement, usage, and disposal.
BigID is a Market Leader in Data Management
.jpeg?width=350&height=245&name=og-image-2021-1200x630%20(2).jpeg)
BigID's data security and privacy-first posture brings with it purpose-built applications to reduce security and privacy risk, regardless of the data being in a structured data repository or on a file system.
.jpeg)
FAQs About BigID
What data sources does BigID cover?
BigID covers over 500+ data sources across the cloud, on-prem data centers, and everywhere in between! We have unmatched coverage so you can find and classify sensitive data, wherever it lives. Connect to hundreds data sources natively: including SaaS, PaaS, IaaS, dev tools, apps, big data & NoSQL, email, and on-prem data centers - at petabyte scale.
Will BigID cover unstructured and semi-structured data?
We offer unparalleled coverage across all data types, from unstructured to semi-structured to structured data. This allows you to uncover dark data and automatically find all the data that matters most to you, including PI, sensitive data, regulated data, financial data, and more. Combine RegEx with advanced ML and AI to scan your data 95% faster.
Will BigID integrate with my existing tech stack?
We are an open and API-first platform that can easily integrate and orchestrate workflows with other enterprise infrastructure. Our partnerships include Collibra, Alation, SAP, Salesforce, ServiceNow, Confluence, Splunk, Snowflake, Microsoft, Google, AWS, and more. BigID also provides extensive APIs, documentation, and code samples to help organizations build custom integrations and orchestrations, so you can get the most out of your tech stack.
How will onboarding, training, and support work?
BigID is agentless, resource-friendly, and super easy to set up. From day one, we seamless connect to and scan all your data sources. Our team of data experts and customer success will guide you every step of the way to ensure you get the most out of BigID and align the solution to your organization’s use cases. We also created BigID University with easy-to-follow modules to help you accelerate time-to-value.
